Why “secure multi‑cloud” suddenly matters so much
Multi‑cloud isn’t exactly new. Back in the early 2010s, most teams were wrestling with one big question: “AWS or not AWS?” Then Azure and GCP matured, SaaS exploded, and regulators started asking uncomfortable questions about resilience and data residency. Around 2018–2020, many enterprises “slid” into multi‑cloud almost by accident: a bit of AWS from engineering, some Azure because of Microsoft 365, GCP for data science.
Security architecture, however, stayed mostly single‑cloud in mindset. Teams tried to copy‑paste AWS patterns into Azure, glued on a couple of CASB tools, and called it “multi‑cloud strategy”. That worked until the first serious incidents showed up: inconsistent IAM, unmanaged identities in one cloud, over‑permissive service accounts in another, and no unified view of who could access what.
By 2024–2025, regulators, boards and cyber insurers began to explicitly ask about multi‑cloud risk. That’s why, going into 2026, “arquitetura segura em multi‑cloud” is less about technical fashion and more about survival: how to design something defendable across at least two major providers, plus a zoo of SaaS platforms.
Core principles of secure multi‑cloud architecture
Before frameworks and shiny tools, secure multi‑cloud boils down to a few stubborn principles. If these are wrong, no amount of automation will save you.
First, identity is the real perimeter. You can’t rely on IP ranges or “internal networks” when you have five regions, three providers, and half your workloads are serverless. Centralized identity (IdP) issuing short‑lived tokens for every cloud is the heartbeat of a secure design.
Second, governance must be cloud‑agnostic, but controls are cloud‑specific. Your policies should say things like “all data classified as confidential must be encrypted at rest with customer‑managed keys”, not “use KMS with this Terraform snippet”. At the same time, your reference architectures for AWS, Azure, and GCP must translate that policy into native controls that actually work.
Third, visibility first, complexity second. Teams love to design clever topologies with service meshes, cross‑cloud networking and exotic failover patterns. But if your SOC can’t see logs in a unified way and can’t answer “who did what, where and when?” across providers, you’re building a castle with no windows.
Finally, everything is code: not just infrastructure, but policies, guardrails, and even exception handling. If your multi‑cloud controls live in wikis and PowerPoints, they don’t exist.
Key building blocks you really shouldn’t skip
Let’s walk through the foundational pieces that show up in almost every solid multi‑cloud security architecture.
Longer story short: you’re trying to build a spine that every new project can attach to, instead of reinventing from scratch.
– Central IdP and SSO: All human access federated via one identity provider, with role‑based access and just‑in‑time elevation.
– Cloud‑native IAM baselines: Predefined roles and permission sets for common personas (SRE, data engineer, app dev), versioned and deployed via code.
– Landing zones for each provider: Network, logging, encryption, and baseline security controls packaged as templates.
– Unified logging and telemetry: Central log lake or SIEM where events from all clouds and SaaS platforms land in a normalized way.
– Policy as code: Guardrails and checks baked into CI/CD, infra pipelines and ticketing workflows.
Once this spine exists, the melhores práticas de segurança em multi cloud para empresas deixam de ser teoria e começam реально работать в ежедневной рутине команд.
Historical traps: how we learned the hard way
A lot of what we call “best practices” today is just a scar with a nicer name.
Early multi‑cloud attempts around 2015–2018 often fell into two extremes. One group insisted on abstracting everything: generic APIs, universal security layers, “write once, run anywhere” for security controls. They discovered the hard way that cloud‑agnostic usually means “poorly integrated, expensive, and 80% of native features unused”.
The other extreme was fully siloed: each cloud had its own architecture, its own landing zone and its own security team. On paper, that gave deep expertise. In reality, executive management had no consolidated risk picture and incident response during cross‑cloud campaigns (like ransomware operators combining VPN abuse + cloud misconfigurations) was chaotic.
By 2022–2024, patterns started converging: shared governance and identity at the top, strong provider‑specific implementations underneath, glued by platforms de gestão de segurança multi cloud para 2026 that focus on visibility, posture management and automated remediation rather than fake abstraction.
Core patterns that still hold in 2026
There are a few architecture patterns you’ll see in almost every mature organization.
Short version: you don’t have to invent everything from scratch; you do need to adapt them to your scale, risk and regulatory landscape.
– Hub‑and‑spoke per cloud, mesh on top
Each provider gets its own network and account/subscription structure (hub‑and‑spoke, shared services VPC/VNet, etc.). On top of that, a minimal cross‑cloud connectivity layer is built, often via VPN or private interconnects, plus zero‑trust access patterns for humans and services.
– Centralized policy with delegated enforcement
Security defines global policies (like “no public S3 buckets with PII”), but enforcement happens via cloud‑native tools and policy‑as‑code pipelines managed by the platform teams.
– Tiered environments with inherited controls
Dev, test, staging, prod – each tier shares a consistent security baseline, with stricter monitoring, alerting and change management as you move closer to production.
This is where serviços de consultoria em arquitetura multi-cloud segura can be useful: not because you can’t read a provider’s docs, but because an outsider can quickly benchmark your patterns against what works (and fails) in dozens of other environments.
Real‑world case 1: Large retailer untangling uncontrolled multi‑cloud
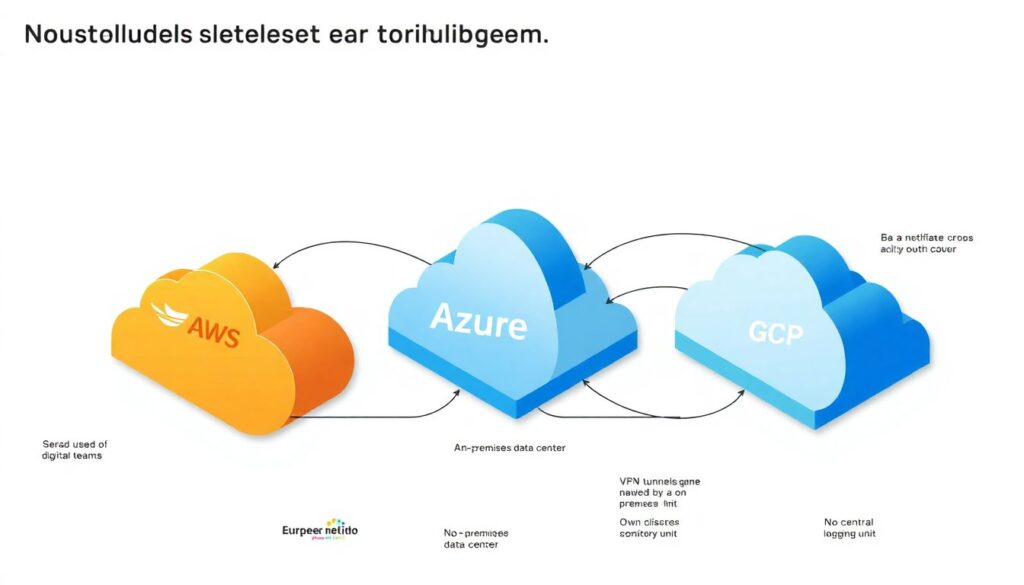
A European retail group arrived at multi‑cloud the messy way: AWS used by digital teams, Azure via a massive Microsoft agreement, plus GCP quietly adopted by the data science unit. Each cloud had its own IAM structure, its own VPNs back to on‑premises, its own security tools, and no central logging.
They had a near‑miss incident: a former contractor still had admin access to a GCP project he’d created, and discovered it while trying to log into his old Gmail; luckily, he reported it. Internal investigation revealed:
– Over 300 IAM roles with “owner” or equivalent permissions across three providers
– No consistent MFA enforcement for admins
– Fragmented logs, with some environments logging only to local storage
The remediation program focused on identity, logging, and baselines before any fancy restructures:
1. Introduced a single enterprise IdP and federated access to all clouds.
2. Replaced “admin” roles with least‑privilege, time‑bound access using approval workflows.
3. Built per‑cloud landing zones and migrated high‑risk workloads first.
4. Stood up a central SIEM to collect logs from AWS, Azure, GCP and key SaaS providers.
The outcome: they cut the number of standing admin accounts by 80% in six months and got, for the first time, a consistent view of privileged actions across providers. Their implementation de arquitetura multi cloud segura em grandes empresas was not perfect, but it was auditable, measurable, and structurally improvable.
Real‑world case 2: Fintech over‑abstracting security and paying the price
A fast‑growing fintech wanted to be “portable” across clouds. They built everything on top of containers and a heavy service mesh, wrapped it in their own security abstraction layer, and limited the use of cloud‑native features. The theory: easier migrations, consistent controls; the practice: complexity, blind spots, and hidden assumptions.
Two concrete problems showed up:
– Their homegrown secrets service didn’t integrate cleanly with cloud serverless offerings, so dev teams quietly used native secrets managers on the side.
– Their generic network security layer wasn’t aware of subtle differences in how security groups/NSGs and routing worked in each cloud, leading to misaligned firewall rules.
During a red‑team exercise, testers discovered an internal dashboard in one cloud that bypassed the global security proxy and allowed lateral movement via a misconfigured instance profile. The SIEM saw odd behavior, but the linkage between identity in Cloud A and context in Cloud B was missing.
To fix this, they dropped the idea of a single abstraction layer and instead doubled down on:
– Cloud‑native IAM and secrets managers, with a unified policy model and centralized identity.
– Zero‑trust principles enforced at the service level, not just at the network edge.
– Stronger posture management and ferramentas de monitoramento e compliance para segurança multi cloud to cover provider‑specific quirks.
They kept some abstraction where it made sense (observability, deployment pipelines) but accepted that security needs to embrace each cloud’s strengths instead of pretending they’re all the same.
Common misconceptions that still cause trouble
Some myths just refuse to die, especially when teams are under pressure to “go multi‑cloud” quickly.
First myth: “Our provider handles security, we handle business logic.”
Every major vendor repeats the “shared responsibility model”, yet people keep stumbling. Providers secure the underlying infrastructure, but identity design, data classification, key management and segmentation are on you. Especially in multi‑cloud, no one vendor will stitch your story together.
Second myth: “Multi‑cloud automatically improves resilience.”
Not if you replicate the same weak patterns twice. If your failover plan is “we’ll spin up in Cloud B if Cloud A fails”, but you’ve never tested cross‑cloud DNS cutover, data sync, or IAM replication, you don’t have resilience – you have an assumption.
Third myth: “We can copy our on‑prem network security model into the cloud(s).”
Trying to recreate a big flat “internal network” with VPNs and broad trust relationships multiplies blast radius. Modern multi‑cloud security architecture is closer to zero‑trust plus micro‑segmentation than a traditional DMZ model.
Practical best practices for 2026 (that people actually follow)
Theory is fine, but security teams are usually bandwidth‑constrained. Let’s focus on a short list that organizations actually manage to adopt and maintain.
– Standardize on one identity layer for humans and services
Use a single IdP for workforce access. For services, adopt short‑lived credentials (OIDC, workload identities) where possible and remove long‑lived keys from code and CI.
– Codify your landing zones and guardrails
Define once, roll out everywhere. Baseline logging, network patterns, encryption, IAM structures – all implemented as code, with unit tests and security reviews.
– Use posture management tools, but don’t outsource thinking
Platforms de gestão de segurança multi cloud para 2026 will flag misconfigurations, but you still need a risk model to decide what matters, how fast to fix it, and when to accept or transfer a risk.
In practice, melhores práticas de segurança em multi cloud para empresas вырастают из десятков таких мелких, но систематичных решений, а не из одного волшебного фреймворка.
How to start (or restart) your secure multi‑cloud journey
If you’re already in multi‑cloud chaos, you don’t need a five‑year program before you can sleep again. Start with a focused, 90‑day sprint.
1. Inventory and classify
Map critical applications, data stores and identities across providers. Even a rough but honest map beats a perfect diagram that never arrives.
2. Stabilize identity and access
Enforce MFA for all admins. Eliminate shared accounts. Introduce just‑in‑time access where feasible.
3. Normalize logging and detection
Make sure all clouds send security‑relevant logs to one place. Add basic detections for high‑risk actions (new admin roles, public buckets/databases, key changes).
4. Design or refine landing zones
Pick one provider and harden its baseline. Then replicate concepts (not code) into the others, respecting their native idioms.
From there, you can iterate: stronger data protection, consistent key management, deeper automation, and continuous testing through red‑team exercises and chaos engineering.
When and how to bring in external help

Multi‑cloud security is a moving target. New services land every month, regulations shift, and attackers learn faster than compliance frameworks do. It’s rarely realistic for an in‑house team to master three major clouds plus dozens of SaaS platforms and keep up with day‑to‑day operations.
That’s where serviços de consultoria em arquitetura multi-cloud segura, specialized MSSPs, and independent auditors can play a useful role. The trick is to use them as force multipliers, not as a crutch:
– Have them stress‑test your reference architectures instead of writing them entirely without your input.
– Ask for knowledge transfer and reusable artifacts – policy as code modules, runbooks, playbooks.
– Make sure their recommendations fit your team’s actual capacity to maintain and monitor.
If you get this balance right, your arquitetura segura em multi‑cloud stops being a one‑time project deck and becomes an evolving capability that can survive 2026’s changes – new cloud services, new regulations, and unfortunately, new attack techniques as well.