In the last five years Kubernetes quietly became the de‑facto substrate for modern apps, and only then did many teams realize how porous their clusters actually were. CNCF surveys show that from 2021 to 2023 the share of organizations running Kubernetes in production jumped from roughly 83% to above 90%, while reports from Sysdig and Red Hat indicate that more than 70% of respondents faced at least one security incident related to misconfigured containers or clusters. Against this backdrop, revisiting scanners, admission controllers and policies is less a best practice and more a survival tactic for any serious platform team.
Where Kubernetes security tooling stands today
If you look at the current wave of ferramentas de segurança para Kubernetes, three categories dominate: image and configuration scanners, admission controllers integrated with policy engines, and broader cloud‑native security platforms. Market data from 2021–2023 shows double‑digit annual growth in container security spending, with Gartner estimating that cloud workload protection, where Kubernetes sits, has been growing around 20–25% per year. Interestingly, most breaches analysed in this period were not zero‑day exploits but predictable issues: exposed dashboards, default credentials, over‑privileged service accounts and unscanned images with known CVEs that had patches available for months.
Scanners: from CVE checklists to risk context
Three years ago, image scanners were often little more than glorified CVE databases. Today’s scanner de segurança Kubernetes preço discussions revolve less around basic vulnerability counts and more around added value: reachability analysis, exploit prediction and linkage to runtime telemetry. Vendors claim that adding context cuts remediation queues by 40–60%, and independent case studies from 2022–2023 show that teams that gate registries with scanning reduced deployment of critical‑severity vulnerabilities by more than half. The economic angle is clear: every avoided incident means fewer emergency patch windows, lower downtime compensation and less time spent on incident reports for regulators and customers.
Admission controllers as policy enforcers in the control plane
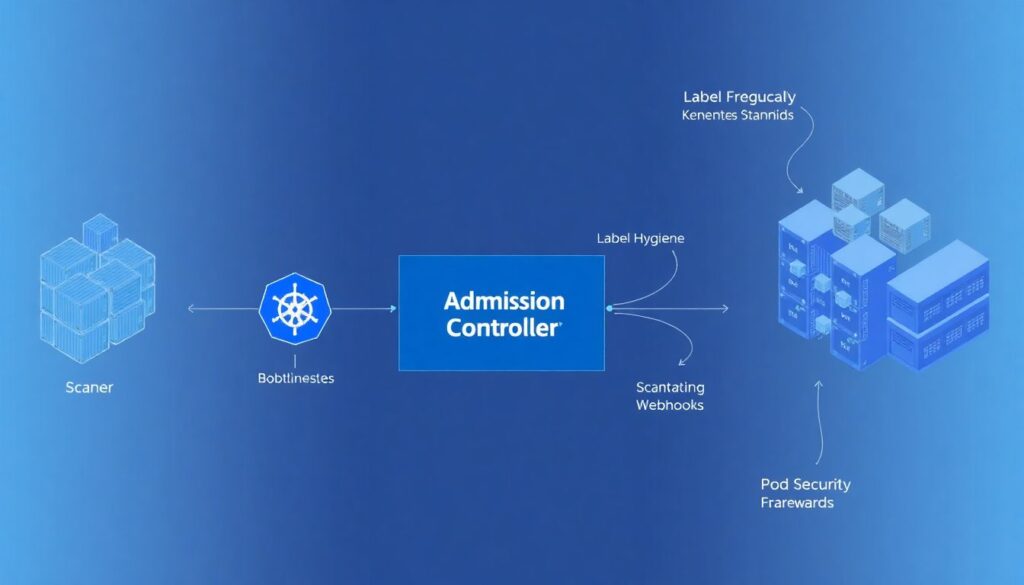
Once images are scanned, the next weak point is what actually gets admitted into the cluster. The melhores admission controllers para Kubernetes evolved from simple mutating webhooks into sophisticated policy frameworks that can encode everything from label hygiene to Pod Security Standards. Adoption data is telling: CNCF‑related surveys suggest that by 2023 more than 40% of mature Kubernetes users had at least one custom admission controller in production, up from around 20% in 2021. The business driver here is governance; financial and healthcare companies in particular use admission to hard‑block non‑compliant workloads, which in turn reduces audit findings and simplifies proving continuous compliance under regimes like PCI DSS or HIPAA.
Policies: from documents to executable guardrails
A recurring anti‑pattern is teams writing impressive PDF guidelines and then never wiring them into the cluster. The shift to “políticas de segurança Kubernetes como implementar de forma prática” is about turning those written standards into code managed alongside applications. Open Policy Agent, Kyverno and similar tools made this realistic: teams describe rules in declarative form, version them in Git and rely on admission controllers to enforce them. Over the 2021–2023 window, organizations that fully codified policies reported up to 30% faster application onboarding because security review became a repeatable, automated check instead of an ad‑hoc meeting with a security architect for every new microservice or namespace.
Economic aspects and ROI for enterprises

From a CFO’s perspective, Kubernetes security can look like yet another cost center, but recent numbers tell a more nuanced story. Analyst estimates for 2023 put average annual spend on plataformas de segurança Kubernetes para empresas mid‑market between 150–400 thousand dollars, depending on cluster scale. At the same time, Ponemon‑style studies peg the average cost of a significant cloud misconfiguration incident in the low seven figures once you combine downtime, forensics, legal work and reputational damage. That asymmetry explains why many boards now accept a 5–8% uplift in platform budget for security tooling, especially if coupled with clear KPIs such as reduced mean time to detect and fewer critical findings in external audits.
Industry impact and regulatory pressure
On the industry side, these tools are reshaping both vendor strategy and internal team structures. Cloud providers bundle more native controls, while independent vendors race to differentiate on machine‑learning‑driven anomaly detection and supply‑chain security. Meanwhile, sectors like banking and critical infrastructure increasingly demand demonstrable cluster hardening as part of procurement: RFPs now ask explicitly about admission control policies, SBOM support and runtime scanning. Over the last three reported years, this has pushed even conservative organizations to pilot modern Kubernetes security stacks, often consolidating separate container, host and network tools into fewer integrated platforms to simplify operations and vendor management.
Looking ahead: forecasts up to the mid‑2020s
Looking toward 2026, most credible forecasts expect Kubernetes‑related security spend to keep outpacing general IT security budgets by several percentage points annually. As more workloads become stateful and business‑critical, we can anticipate tighter coupling between scanners, admission controllers and runtime protection: a vulnerability discovered in an image will automatically translate into a blocking policy and a focused runtime hunt. Economically, that means security will be treated less as an insurance policy and more as part of platform reliability engineering. For teams, the practical takeaway is straightforward: invest now in composable tooling and policy‑as‑code skills, because manual gatekeeping simply does not scale with the growth trajectory of modern clusters.