Por que falar de segurança com Infrastructure as Code agora?
Security automation with Infrastructure as Code (IaC) stopped being a “nice-to-have” the moment attackers começaram a versionar os próprios ataques. If your cloud, network and Kubernetes clusters are still configured “by hand” while the rest of the pipeline is automated, you’re basically leaving the front door open and then investing in a fancy vault inside the house. Terraform and Ansible give us a way to treat security like code: repeatable, testable, reviewable. The twist is doing this in a way that is actually practical, not just pretty slideware.
Automating security with Terraform and Ansible means turning security policies, hardening rules and compliance controls into files that live in Git, pass through CI, and are enforced every time you apply or run a playbook. Instead of “someone” remembering a checklist, the code never forgets.
Definindo os termos sem enrolação
Let’s align on a few core concepts before we start wiring explosives to our old processes:
Infrastructure as Code (IaC)
IaC is the practice of describing infrastructure (networks, VMs, containers, firewalls, policies, identities) in code-like files, usually declarative. The goal is that `git clone + terraform apply` (or an Ansible run) can recreate the same environment from scratch, including its security posture.
Terraform
Terraform is a declarative IaC tool focused on provisioning and managing infrastructure across providers (AWS, Azure, GCP, Kubernetes, etc.). You describe “what should exist” (resources and their attributes), and Terraform figures out “how to get there”. In our context, security is modeled as resources as well: security groups, IAM roles, key policies, WAF rules.
Ansible
Ansible is a configuration management and automation tool. It’s imperative-ish: you describe tasks and roles that Ansible executes over SSH or APIs. For security, we typically use Ansible for OS hardening, application-level policies, agent installation, and continuous drift correction inside VMs, containers and even network devices.
Security automation with IaC
This is the discipline of encoding security baselines, policies, and checks into Terraform modules and Ansible roles, and then wiring them into CI/CD so they run on every change. It’s less about “tools” and more about treating security as a first-class citizen in the pipeline.
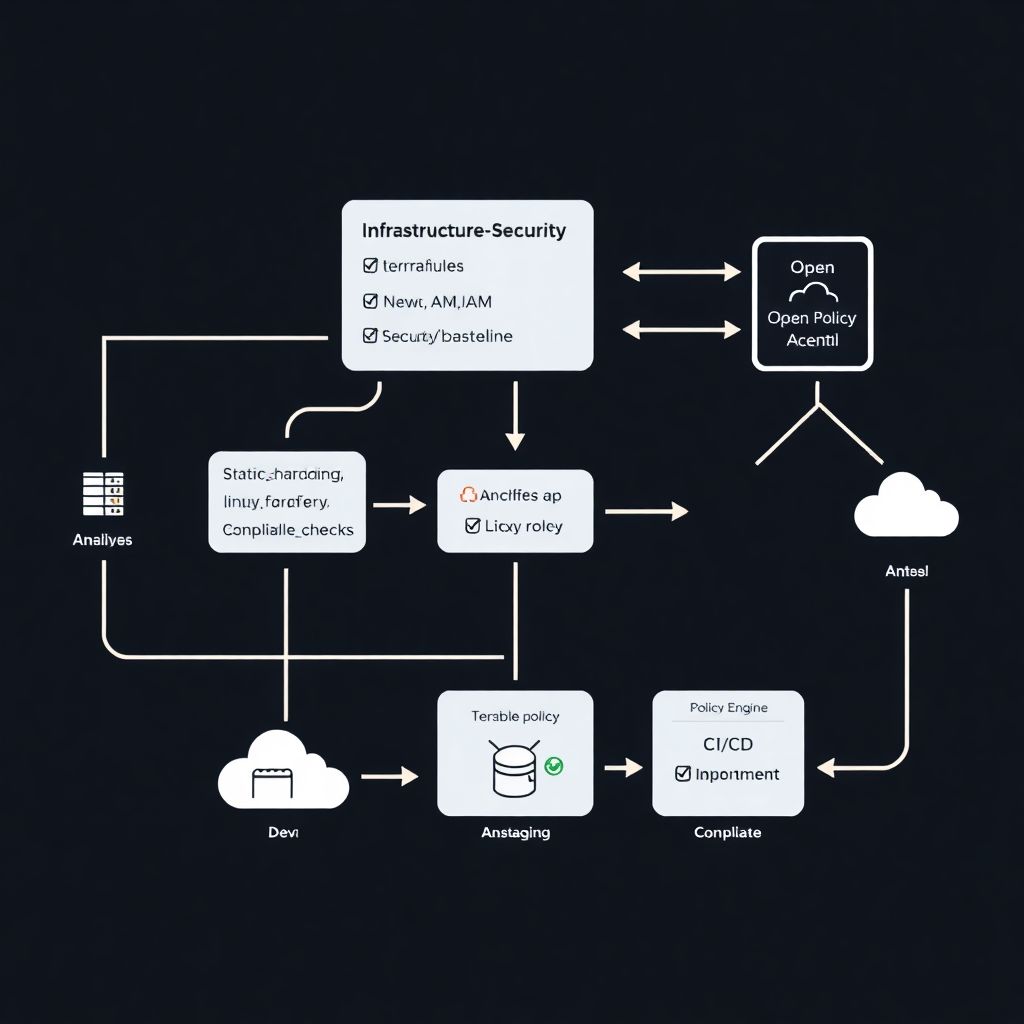
Um diagrama mental: onde a segurança entra no fluxo IaC
Imagine a simple architecture diagram described in text:
– On the left, a Git repo called `infrastructure-security` with:
– Terraform modules (network, IAM, logging, security-baseline)
– Ansible roles (linux_hardening, app_firewall, compliance_checks)
– Above the repo, a CI pipeline box:
`Static analysis -> Security policy checks -> Terraform plan -> Ansible dry-run`
– To the right, three boxes labeled “Dev”, “Staging” and “Prod” clouds.
– Arrows go from Git to CI to each environment, passing through a “Policy Engine” box (Open Policy Agent / Sentinel / custom) that either approves or blocks changes.
In this mental map, security is not a separate, lonely SIEM box. It’s baked into the path that any infrastructure change must travel.
Terraform vs Ansible para segurança: quem faz o quê?
People often ask, “Should I use Terraform or Ansible for security?” That question is like asking if you should use a blueprint or a toolbox. They solve different layers:
– Terraform secures the infrastructure shape:
– Network segmentation and security groups
– Encryption settings for S3 buckets, disks, databases
– IAM roles, policies and trust relationships
– Logging, audit trails and key management resources
– Ansible secures the content and behavior:
– OS hardening (sysctl, file permissions, SSH config)
– Application-level firewalls and services
– Installation and configuration of EDR/AV agents
– Local compliance checks and remediation
Compared to alternatives like CloudFormation + SSM or Pulumi + Chef, Terraform + Ansible win on ecosystem, neutrality and learning curve. That’s why so many empresas investem em cursos de terraform e ansible para automação de segurança: the combination is powerful but still approachable.
Políticas como código: do PDF para o Git
Most companies still keep security policies in PDFs, Confluence pages or SharePoint. That’s documentation, not enforcement. Policies as code means:
– The rule “all data at rest must be encrypted with customer-managed keys” becomes:
– Terraform code that rejects non-encrypted resources
– A policy engine rule that fails the pipeline if someone tries
– The rule “only bastion hosts can access the database” becomes:
– Security group rules and network ACLs coded in Terraform modules
– Periodic Ansible checks to ensure firewall rules haven’t drifted
A practical pattern is to create a dedicated repo or directory specifically for policy modules:
– Terraform modules:
– `network_secure_vpc`
– `secure_s3_bucket`
– `baseline_iam_roles`
– Policy engine rules (e.g. OPA/Conftest, Terraform Cloud Sentinel)
– Ansible roles:
– `cis_linux_hardening`
– `logging_and_auditing`
– `compliance_report`
This is also where specialized consultoria em infraestrutura como código com terraform e ansible costuma atuar: transforming vague guidelines into reusable modules and policy bundles rather than one-off scripts.
Desenhando a arquitetura de políticas em texto
Picture another text-based diagram:
1. Dev opens a pull request changing Terraform code.
2. CI pipeline triggers:
– Step 1: `terraform fmt` and `terraform validate`.
– Step 2: Static analysis by ferramentas de segurança para infrastructure as code terraform ansible (e.g., Checkov, tfsec, Terrascan, Ansible-lint).
– Step 3: Policy engine (OPA/Sentinel) evaluates rules like “no public S3”, “no 0.0.0.0/0 on SSH”.
– Step 4: `terraform plan` is generated and attached to PR.
3. Only after human review + green policy checks the plan can be applied.
4. After `terraform apply`, an Ansible job runs:
– Apply hardening roles
– Run compliance checks
– Send a report to a security dashboard
In this diagram, “security” appears three times: static analysis, policy evaluation, and post-deployment validation. That’s where real defense-in-depth appears in IaC.
Exemplos práticos: Terraform impondo segurança por padrão
Let’s look at a simplified example of a “secure by default” Terraform module for S3. The idea is: even if an app team tries to be lazy, the module makes it hard to be insecure.
“`hcl
variable “bucket_name” {
type = string
}
resource “aws_s3_bucket” “secure” {
bucket = var.bucket_name
tags = {
“owner” = “security-team”
“purpose” = “secure-data”
}
}
resource “aws_s3_bucket_public_access_block” “this” {
bucket = aws_s3_bucket.secure.id
block_public_acls = true
block_public_policy = true
ignore_public_acls = true
restrict_public_buckets = true
}
resource “aws_s3_bucket_server_side_encryption_configuration” “this” {
bucket = aws_s3_bucket.secure.id
rule {
apply_server_side_encryption_by_default {
sse_algorithm = “aws:kms”
kms_master_key_id = var.kms_key_id
}
}
}
resource “aws_s3_bucket_versioning” “this” {
bucket = aws_s3_bucket.secure.id
versioning_configuration {
status = “Enabled”
}
}
“`
Now, instead of letting each team reinvent the wheel, you just say: “If you want an S3 bucket, you must use our `secure_s3_bucket` module.” You’ve encapsulated multiple melhores práticas de segurança devops com terraform e ansible in one reusable building block.
Ansible como fiscalizador: hardening e testes
Where Terraform stops, Ansible starts. A basic yet powerful pattern:
– Terraform:
– Creates VMs, sets tags, security groups and IAM roles
– Ansible:
– Reads tags and applies correct security role according to environment and application
For example, your Ansible inventory might be dynamic, based on AWS tags. Then you run a playbook like:
“`yaml
– name: Apply security baseline to all Linux servers
hosts: “role_app & env_prod”
become: yes
roles:
– linux_cis_hardening
– configure_auditd
– install_edr_agent
“`
Nonstandard but effective idea: treat your Ansible security roles as ephemeral enforcers. Instead of running them only once at provisioning time, schedule periodic runs (via AWX/Tower, GitHub Actions, or a cron-triggered job) that:
– Check for insecure changes (e.g., someone added a weak SSH cipher)
– Automatically revert them
– Open a ticket in your ITSM system with a diff of what was corrected
That way, configuration drift becomes self-healing instead of a quarterly incident.
Fugindo do óbvio: soluções menos convencionais
Most teams stop at “lint + plan + apply”. Let’s raise the bar with a few less mainstream approaches:
– Simulated breaches as code
Write Ansible playbooks that simulate common misconfigurations and attempted attacks in a test environment: opening SSH to the world, removing logging, dropping firewall rules. Then confirm that:
– Your IaC scanners detect the misconfigurations.
– Your policies block the changes.
– Your monitoring alerts when anomalies happen.
– Blueprints for secure experiments
Create Terraform “lab modules” designed specifically to test security hypotheses. Example: a module that deploys a honeypot environment with deliberately weakened services but isolated networks. Then you run red-team exercises against it regularly—and automate its creation and teardown. This encourages continuous testing without risking production.
– Security as a service in the pipeline
Instead of each team wiring its own checks, build internal serviços de implementação de políticas de segurança com terraform e ansible:
– A shared pipeline template (GitHub Action, GitLab template, Jenkins library) that:
– Runs standard security scans
– Enforces global OPA policies
– Publishes results to a central dashboard
– Teams just include the template; they don’t have to reinvent governance.
– Policy drift detection via “shadow plans”
Once a day, CI runs `terraform plan` against production using the latest code from the main branch, but without applying. If the plan shows changes that no one requested (e.g., manual console changes), it flags policy drift. Ansible can do similar checks at config level, comparing expected vs actual state and logging discrepancies instead of fixing them immediately.
Ferramentas de segurança para Terraform e Ansible que realmente ajudam
You don’t need an extravagant stack. A lean yet effective combo of ferramentas de segurança para infrastructure as code terraform ansible usually includes:
– For Terraform:
– `terraform validate` + `terraform fmt` (sanity checks)
– `tflint` for quality and provider-specific pitfalls
– `tfsec`, Checkov or Terrascan for security misconfigurations
– OPA/Conftest or Sentinel for policy-as-code
– For Ansible:
– `ansible-lint` for playbook quality and basic security hints
– Molecule for testing roles in containers or ephemeral VMs
– Custom Ansible tasks to check for CIS controls, then report metrics
The smart move is not just running these once, but wiring them into every stage: dev machines (pre-commit hooks), CI (on every PR), and scheduled jobs against “as-is” environments.
Comparando com outras abordagens de segurança
Traditional security workflows for infrastructure usually look like:
– Manual change requests
– Post-hoc scans (quarterly, maybe monthly)
– Security teams discovering misconfigurations long after deployment
– A backlog of “please fix this firewall” tickets
Scattered scripts (Bash, PowerShell, ad-hoc Python) are a small improvement, but they don’t scale and are hard to audit. Compared to that, an IaC-centric approach:
– Centralizes intent and implementation in Git
– Makes changes auditable by diff
– Allows PR-based security review before impact
– Integrates with CI/CD instead of being an external bottleneck
If you compare Terraform+Ansible with cloud-native only solutions (CloudFormation + SSM, ARM/Bicep templates + Azure Policies), the main advantage is portability and convergence. You can maintain one security baseline across multiple clouds and on-prem, adjusting only the provider-specific details inside modules and roles. That’s also why many companies seek consultoria em infraestrutura como código com terraform e ansible: they want a cloud-agnostic backbone for security.
Como transformar tudo isso em fluxo do dia a dia
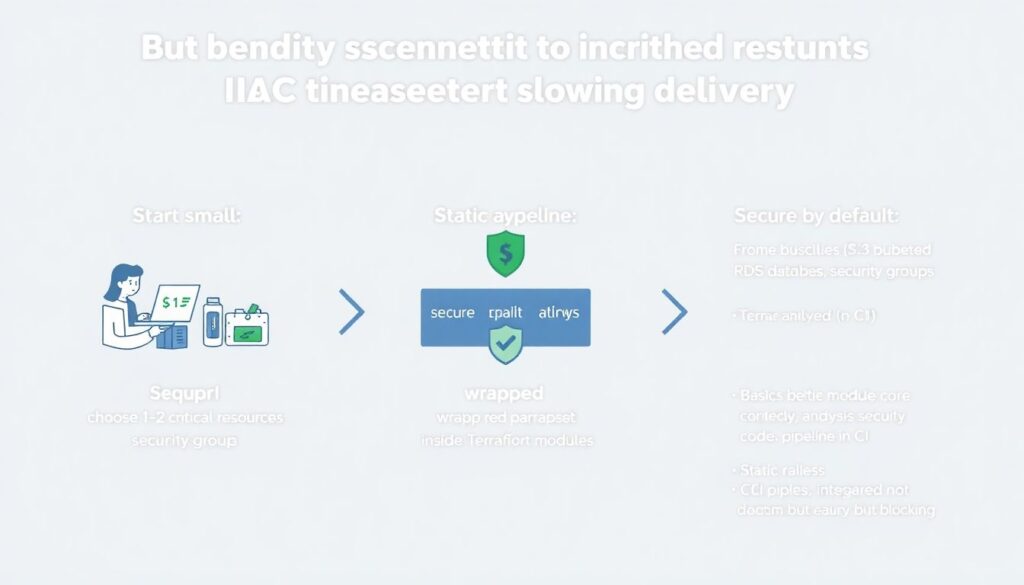
Let’s outline a practical step-by-step to embed security into your IaC practice without paralyzing delivery:
– Start small:
– Choose 1–2 critical resources (e.g., S3 buckets, RDS databases, security groups).
– Wrap them in “secure by default” Terraform modules.
– Introduce basic static analysis in CI.
– Then extend:
– Add Ansible hardening roles for your main OS flavor.
– Integrate ansible-lint and a minimal Molecule test.
– Create one “golden baseline” environment using only these modules and roles.
– Mature:
– Introduce OPA or Sentinel with a handful of high-value policies.
– Build a central dashboard aggregating:
– IaC scan results
– Terraform/Ansible pipeline status
– Drift detection indicators
– Scale:
– Offer internal cursos de terraform e ansible para automação de segurança, not as a one-time training but as recurring sessions with real repo examples.
– Provide ready-to-use pipeline templates and base modules so teams adopt standards without friction.
Here’s a short checklist you can adapt:
– [ ] All new Terraform repos use security modules by default
– [ ] Every CI pipeline runs Terraform/Ansible lint + security scans
– [ ] At least a minimal policy-as-code layer is enforced
– [ ] Ansible hardening is executed not just once, but periodically
– [ ] Drift is detected at infra and config levels
Boas práticas que valem mais do que mais uma ferramenta
A few principles make the difference between “we installed a scanner” and “we actually automated security”:
– Security ownership lives with product teams, not only with the security team.
– The secure path must be the easiest path: modules, roles and pipelines that “just work”.
– Everything is versioned: policies, baselines, exceptions.
– Exceptions to security policies have expirations and clear justifications.
– Metrics track adoption: % of infra deployed via approved modules, % of servers with hardening applied, mean time to fix misconfigurations.
To support teams, some organizations create internal serviços de implementação de políticas de segurança com terraform e ansible: a small expert group that:
– Curates official Terraform modules and Ansible roles.
– Maintains shared CI/CD templates and policy libraries.
– Helps projects migrate legacy infra to the new approach.
Conclusão: segurança automatizada como parte natural do código
Automating security with Terraform and Ansible isn’t about turning everyone into a security engineer. It’s about moving security controls to where developers already work: in code, in Git, in CI. When you model policies as Terraform modules, enforce them with a policy engine, and harden systems with Ansible roles that run repeatedly, security stops being a separate road and becomes the guardrail on the only road.
The nonstandard edge comes from going beyond basic linting: simulating attacks as code, using shadow plans for drift detection, building “security as a service” pipelines, and educating teams with real, project-based training rather than abstract slides. With this mindset, IaC is not just about spinning up servers faster; it’s about ensuring that every environment you create is at least as secure as the best one you’ve ever built—and ideally, more secure the next time you run `terraform apply`.