DevSecOps for Cloud‑Native Apps: Setting the Stage
Cloud‑native apps move fast: microservices, Kubernetes, serverless, multi‑cloud… and attackers move even faster. A few years ago, teams tried to “bolt on” security at the end of delivery, but that doesn’t fly anymore. Today, a pipeline DevSecOps para aplicações cloud native means wiring security checks into every step of build, test and deploy, without killing developer velocity. The trick is to automate as much as possible, keep feedback loops short and make security feel like a normal part of coding, not a bureaucratic gate.
Why Security Needs to “Shift Left”

“Shift left” basically means catching issues when code is still cheap to fix. Instead of a separate security team showing up two days before release with a 40‑page PDF, you push their knowledge into tools that run on every commit. Static analysis, dependency scanning and container image checks run in CI, while runtime protections and anomaly detection protect production. When this works, devs see security findings in the same place as unit tests, and security engineers become enablers, curating policies and tuning tools instead of manually reviewing every change.
—
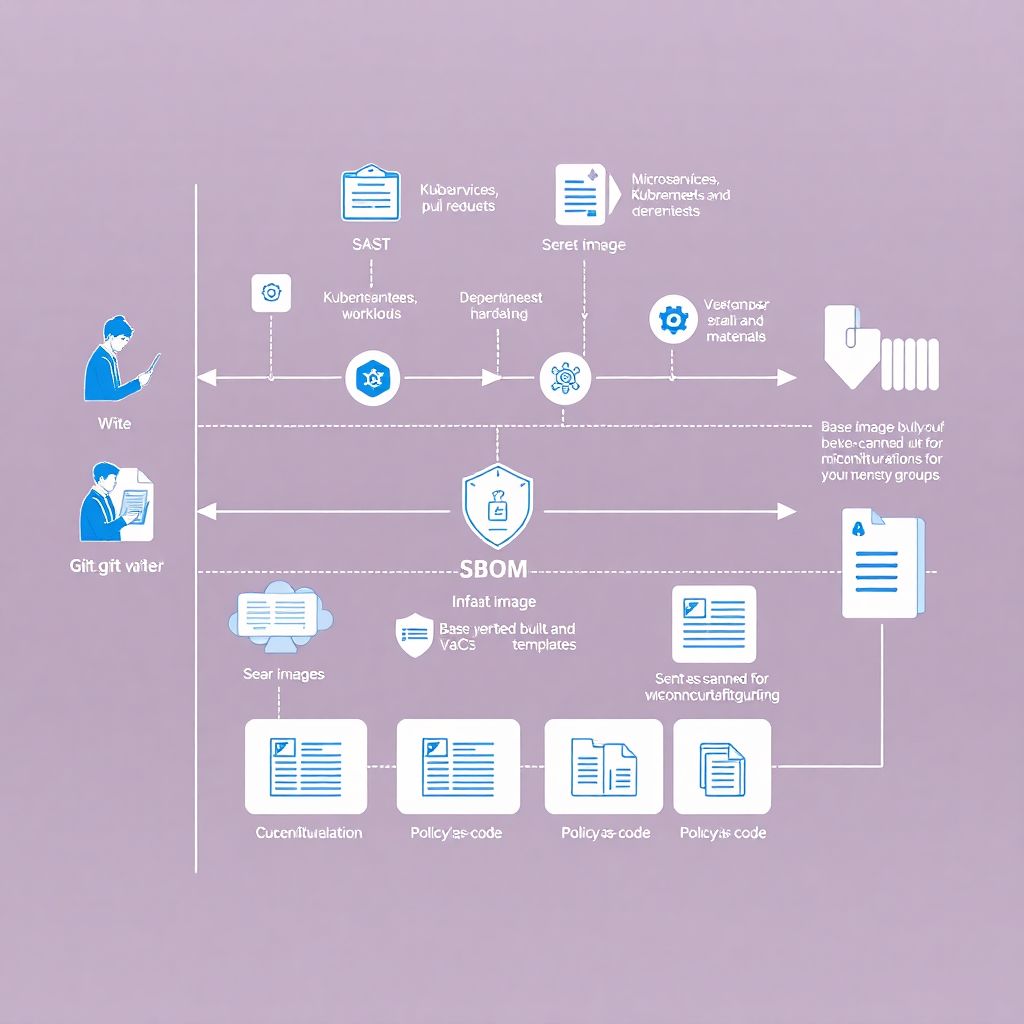
Designing the DevSecOps Pipeline
Core Stages of a Secure Cloud‑Native Pipeline
A solid pipeline DevSecOps para aplicações cloud native usually follows the classic CI/CD flow, but every stage has security hooks. You might structure it like this:
1. Code & dependencies: SAST, secret scanning, SBOM generation
2. Build & containerization: image hardening, base image policies
3. Infrastructure: IaC scanning for misconfigurations
4. Pre‑deploy: DAST, API tests, policy checks
5. Deploy & runtime: admission controllers, runtime monitoring, WAF
The point isn’t to add every possible scanner, but to cover the biggest risks with fast, reliable checks.
A Conversational View on Tooling
When teams first start, they often grab every shiny scanner they can find. After a month, the pipeline is painfully slow and nobody reads the reports. A more realistic approach is to begin with a handful of ferramentas DevSecOps para integração contínua de segurança: one for code and secrets, one for dependencies and containers, and one for IaC. Over time, you tune severity thresholds, add suppression rules and wire results into the same chat channels devs already use. The pipeline should feel like a helpful reviewer, not a passive‑aggressive gatekeeper.
—
Comparing Approaches and Technologies
Open Source vs Managed: What Really Matters
Open‑source tools are attractive: no license cost, strong communities, and deep integration with GitHub or GitLab. But they do demand maintenance: upgrades, rule tuning, scaling scanners with repo growth. On the other hand, serviços gerenciados DevSecOps para aplicações em nuvem offload much of that overhead, offering hosted scanners, dashboards and compliance reports out of the box. The trade‑off is vendor lock‑in, pricing per repo or seat, and sometimes less flexibility. In practice, many teams land on a hybrid: core scanning via open source, plus a managed platform to aggregate results and help with reporting.
Pros and Cons of Key Technology Choices
Kubernetes is still the default for cloud‑native, and it plays nicely with admission controllers, policy‑as‑code and sidecar‑based security agents. The upside is massive flexibility and ecosystem support; the downside is complexity, which often leads to misconfigurations. Serverless simplifies patching and some aspects of isolation, but observability and fine‑grained least privilege can be tricky. Whatever you choose, make sure your security controls can be expressed as code and versioned alongside the application, so your pipeline can enforce them consistently across environments.
—
Implementing DevSecOps in CI/CD on the Cloud
Practical Steps to Wire Security Into CI/CD
If you’re wondering como implementar DevSecOps em CI CD na nuvem, start small and iterate. First, pick your main CI platform (GitHub Actions, GitLab CI, CircleCI, Azure DevOps, etc.) and integrate fast, low‑noise scanners on pull requests: SAST and dependency checks. Next, extend your pipeline with container image scanning and IaC checks on main branch merges. Only after that feels stable should you add heavier tests like DAST or performance‑security combined tests. Keep everything as code: pipeline definitions, security rules and exceptions tracked via pull requests.
Best Practices for a Secure Cloud‑Native Pipeline
Over time, aim for melhores práticas de segurança em pipeline cloud native. That includes enforcing signed commits and images, generating and storing SBOMs for every build, and blocking deployments that contain known critical CVEs unless there’s an explicit, reviewed waiver. Use policy‑as‑code engines (like OPA/Gatekeeper or Kyverno) to enforce baseline security on Kubernetes: no privileged containers, no hostPath volumes, clear network policies. Finally, make sure security findings are tied back to business impact: “this vulnerable library exposes customer data,” not just “CVE‑2025‑12345 is high severity.”
—
Real‑World Style Case Studies
Case 1: SaaS Startup on Kubernetes
A mid‑stage SaaS company running on managed Kubernetes had a classic problem: fast feature delivery, zero formal security process. Initially, they only ran occasional manual pen tests. After a dependency incident, they decided to build a pipeline DevSecOps from scratch. They added SAST and dependency scanning in PRs, container scanning on main, and a simple admission controller to block images without a passed scan. Within three months, they cut “time to fix” critical vulns from weeks to days and avoided a major supply‑chain issue when a compromised open‑source package was flagged before deployment.
Case 2: Fintech Under Heavy Regulation
A fintech handling payments had strict compliance requirements and audits every quarter. They moved from a monolith on VMs to microservices on a public cloud, and their old manual security review process simply couldn’t keep up. They adopted serviços gerenciados DevSecOps para aplicações em nuvem to centralize vulnerability data from multiple tools and added IaC scanning to ensure every VPC, subnet and security group met policy. When auditors arrived, the team produced build logs, SBOMs and automated policy checks. Instead of a painful scramble, the audit became mostly about reviewing automated controls and exception workflows.
—
Tools and Selection Recommendations
How to Choose Tools Without Getting Lost
When you start evaluating ferramentas DevSecOps para integração contínua de segurança, focus on three questions: Does it integrate easily with your current repos and CI? Can it run fast enough on every PR without annoying developers? And can you manage findings at scale (deduplication, baselines, trend reports)? Avoid tools that only provide pretty dashboards but no automation hooks. Prefer those that can run as code in your pipeline and send results to your existing issue tracker, so security bugs are treated exactly like functional bugs.
Recommendations by Team Maturity
For small teams, prioritize simplicity: hosted scanners, minimal configuration and default policies that are “good enough.” As you grow, bring more controls in‑house, write custom rules that match your architecture, and invest in threat modeling and chaos engineering for security. At a certain scale, you’ll likely standardize on a central platform to aggregate data from multiple scanners, map them to services, and provide a single pane of glass to engineering leadership and compliance.
—
Trends in DevSecOps and Cloud Security in 2026
What’s Changing in the Next Few Years
By 2026, most serious engineering teams will treat DevSecOps as standard, not a novelty. AI‑assisted security is becoming mainstream: models that triage findings, suggest fixes, and even generate secure‑by‑default code snippets. For pipeline DevSecOps para aplicações cloud native, expect more emphasis on continuous software supply‑chain security: signing everything, verifying provenance and tracking dependencies in real time. At the same time, regulations are tightening, pushing organizations to prove not just that they ran scanners, but that they consistently blocked risky builds and could reconstruct exactly what code and dependencies were in production at any moment.
Looking Ahead
The most successful teams won’t be the ones with the longest tool list, but those that made security part of their culture and daily workflow. That means treating security controls like any other feature: measured, iterated and improved. With thoughtful design, the right mix of tools and a focus on developer experience, serviços gerenciados DevSecOps para aplicações em nuvem and open‑source solutions alike can help you build a resilient, auditable and fast delivery pipeline that keeps your cloud‑native applications safe without slowing innovation.