Why network segmentation in VPC/VNet actually matters
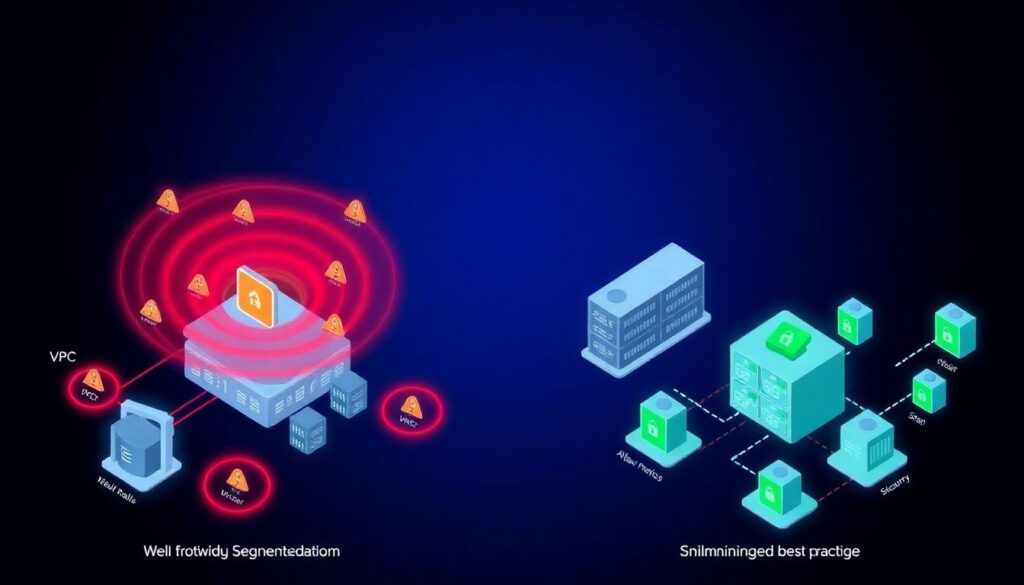
Most teams only start caring about segmentation after a nasty incident or a failed audit. In cloud, though, the blast radius grows fast: one over‑permissive security group in a VPC or an “allow any” NSG in a VNet can turn a small misconfig into a company‑wide outage. When we talk about boas práticas de segmentação de redes em VPC/VNet para reduzir superfície de ataque, we’re really talking about drawing smart boundaries: which workloads can talk to which, over what ports, and under what identity. Done well, segmentation turns each subnet, app tier, or even each pod into a kind of “watertight compartment” so that when something leaks, the whole ship doesn’t sink. That mindset is what distinguishes ad‑hoc setups from professional architectures in 2026.
For beginners, the main trap is thinking “it’s all inside our cloud account, so it’s safe anyway” and throwing everything into a single flat VPC or VNet.
Comparing segmentation approaches: coarse, fine and identity‑aware
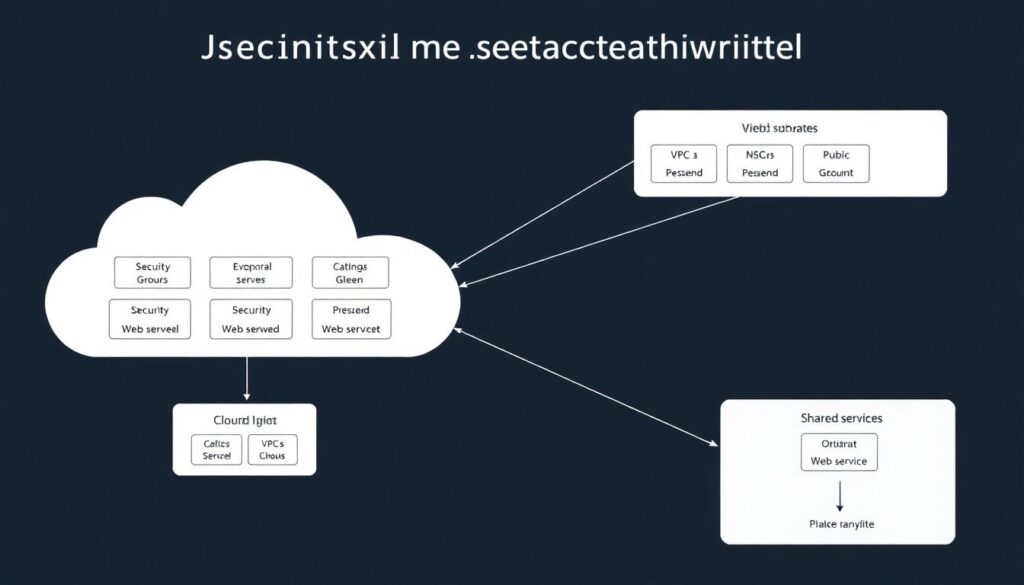
At a high level, there are three families of approaches. First, classic network‑centric segmentation: separate VPCs/VNets, subnets, security groups/NSGs, and routing rules. This is where most teams start: web in public subnets, apps and databases in private subnets, maybe a separate “shared services” VPC or hub‑and‑spoke VNet. Second, service‑centric or microsegmentation, where rules are defined per workload, VM set, container, or Kubernetes namespace, often enforced by agents or service mesh. Third, identity‑centric segmentation, where decisions rely mainly on identity (user, service principal, workload identity) and posture, using tools like Verified Access, conditional access, or Zero Trust Network Access. In practice, mature setups mix all three: coarse isolation by account/project and VPC/VNet, finer rules inside, and identity as the final gatekeeper.
Newcomers often jump straight to complex microsegmentation before they even have clear network zones, which quickly becomes unmanageable.
Classic patterns in AWS VPC and Azure VNet
In AWS, the usual starting point is a VPC per environment (prod, stage, dev) with public and private subnets spread across AZs, security groups tied to instances or ENIs, and maybe network ACLs used sparingly. In Azure, VNets plus subnets and NSGs play that same role, with extra tools like Azure Firewall and Virtual Network Manager to coordinate at scale. The implementação de segmentação de rede em aws vpc e azure vnet tends to converge on similar ideas: isolate internet‑facing tiers, keep data stores in private subnets, control east‑west traffic with SGs/NSGs, and use peering or a hub‑and‑spoke topology for shared platforms like logging or CI. The pattern sounds simple on paper, but the details—like default routes and “temporary” any‑any rules—are where many real‑world leaks appear.
One common novice mistake is relying entirely on peering and forgetting that transitive connectivity can accidentally expose internal services to partners or test accounts.
Pros and cons of network‑centric segmentation
The big selling point of subnet‑ and VPC/VNet‑based segmentation is clarity. You can show a diagram to non‑network folks and they’ll roughly understand where the dangerous edges are: this is internet, this is partner connectivity, this is crown‑jewel data. Route tables and security groups are native, well‑integrated with cloud logging, and supported by every compliance framework out there. On the downside, network‑only controls struggle with modern, fast‑moving architectures: dozens of services, ephemeral containers, autoscaling groups that come and go in seconds. Rules get bulky, and you either oversimplify (allow too much) or drown in management overhead. Also, IP‑based policies break when you add multi‑region or hybrid setups with overlapping ranges, something that tends to appear around year two of a cloud migration.
Beginners often overuse network ACLs or multiple overlapping NSGs/SGs, creating a maze that no one dares to clean up.
Microsegmentation and service‑centric models
As organizations mature, they start asking for segmentation that follows workloads, not IPs. That’s where microsegmentation and service meshes enter the picture. Instead of only saying “subnet A can talk to subnet B,” you can define that service X can call service Y over TLS, and nothing else. In Kubernetes, that might mean network policies plus service mesh authorization; on VMs, it could be host‑based firewalls managed centrally or third‑party agents. The benefit is precision: a compromised pod can’t automatically pivot to every other pod in the cluster. In effect, you’re carving the VPC/VNet into hundreds of tiny trust zones. But there’s a catch: more rules, more moving parts, and a greater need for clean naming, tagging, and automation. Without that, microsegmentation decays into chaos, and people silently bypass it.
A classic rookie error is enabling a service mesh but leaving permissive “allow all” policies, assuming the mesh magically secures everything by default.
Identity‑centric and Zero Trust approaches
Identity‑aware controls are growing fast in cloud environments. Instead of asking “what subnet is this from?” the platform asks “who is this workload or user, and how healthy is the device?” With Zero Trust solutions, private apps may be published without direct network access, relying on brokers that authenticate users and inspect traffic. For services, managed identities and workload identity federation mean an app can call a database not because it sits on a trusted IP, but because it presents a valid token with the right claims. This model scales better across multi‑cloud and remote work, and it supports fine‑grained logging and just‑in‑time access. Yet, when people skip basic segmentation and rely only on identity, a single misissued token or stolen credential can still reach too much of the network.
Beginners sometimes mix “Zero Trust” with “no network rules at all,” which is just wishful thinking with a marketing sticker on top.
How segmentation actually reduces attack surface
From an attacker’s perspective, flat networks are playgrounds: once inside, they can scan freely, move laterally, and hunt for poorly protected services. When you apply melhores práticas de segurança em vpc e vnet na nuvem, the goal is to shrink the reachable set of targets at each step of an intrusion. That’s the practical meaning of como reduzir a superfície de ataque com segmentação de redes na nuvem. For example, a compromised web server in a public subnet should not see your internal CI, AD, or finance databases at all, ideally not even at the routing level. If it must reach something—say, an API tier—that path should be tightly scoped to certain ports and identities, fully logged, and protected with IDS/IPS or WAF where appropriate. The more you compartmentalize, the harder it becomes for attackers to turn one foothold into a full takeover.
A frequent misstep is letting monitoring, backup, or “bastion” servers talk everywhere “just in case”, effectively undoing all other segmentation efforts.
Typical beginner mistakes in VPC/VNet segmentation
Most newcomers repeat the same patterns. They start with one VPC or VNet for everything, thinking they’ll “refactor later,” but later never comes. Security groups and NSGs are cloned and slightly tweaked, so nobody knows which one is authoritative. Tags are inconsistent, which kills any hope of policy‑as‑code or centralized governance. Terraform or Bicep stacks mix networking and apps in the same module, making it hard to evolve the topology. And perhaps the riskiest shortcut: wide “0.0.0.0/0” rules opened for debugging or vendor access and then forgotten. These aren’t rare corner cases; they show up in audits of very serious teams. The cost isn’t just security: troubleshooting flat, messy networks is harder, so outages last longer, and every change feels dangerous.
A good mental test is simple: if you can’t answer “who can reach this resource, from where, and why?” in a couple of minutes, your segmentation is too opaque.
Choosing the right technologies and patterns
There’s no one‑size‑fits‑all blueprint, but some decision points are stable. Smaller teams or simpler apps can lean more heavily on native VPC/VNet constructs: a handful of accounts/subscriptions, clearly named subnets (public, app, data), and well‑documented SG/NSG policies. As the environment grows, you’ll likely add a hub‑and‑spoke or “landing zone” approach, central firewalls or gateways, and policy engines like AWS Organizations SCPs or Azure Policy to enforce standards. Microsegmentation and service meshes make more sense when you have a strong platform team, automated CI/CD, and a consistent way to inject sidecars or agents. Identity‑centric access requires good IAM hygiene, SSO integration, and a realistic plan for certificate and token management. It’s less about fashion and more about whether your team can actually run these tools reliably over years.
Newcomers often chase “enterprise‑grade” gear because a slide deck looked cool, then struggle to maintain even basic rules and logs.
Practical recommendations for real‑world teams
A pragmatic roadmap usually starts with carving the cloud into clear zones: separate projects/accounts/subscriptions per environment and per major business domain. Within each, design a small, repeatable VPC/VNet pattern and treat it like a product: version it, document it, and roll out updates via IaC. Enforce least privilege in SGs/NSGs by default and use security group referencing or application security groups to avoid hard‑coding IPs. Turn on flow logs and central logging from day one; you can’t improve what you can’t see. Then layer on identity‑aware access for admins and remote workers to avoid direct VPN‑to‑everything patterns. When in doubt, prototype with a non‑critical environment and measure how often people hit denied rules; real‑world friction is the best feedback on whether your segmentation is sensibly strict or absurdly tight.
If the learning curve feels steep, serviços de consultoria em segmentação de rede vpc vnet can accelerate this phase, provided you also invest in internal skills, not just outsourced diagrams.
Trends and tooling around 2026
By 2026, cloud providers are baking more segmentation features into the platform itself. AWS is pushing managed connectivity layers like VPC Lattice and Verified Access, making it easier to expose services securely without clumsy peering webs. Azure’s Virtual Network Manager and improved policy capabilities help standardize segmentation across dozens or hundreds of VNets. eBPF‑based firewalls and observability agents provide near real‑time visibility of which workloads talk to which, feeding into automated policy suggestions. At the same time, regulations and insurance requirements are getting stricter about lateral movement controls and data residency, which makes sloppy, flat networks increasingly hard to justify. The direction is clear: more automation, more identity signals, and less blind trust in “internal” traffic.
The flip side is complexity: with so many layers, misconfigurations can hide in plain sight if you don’t continuously review and test your policies.
When to bring in specialists
Some milestones are good signals that you may need outside help. If you’re going multi‑region or multi‑cloud, connecting on‑prem, or handling sensitive data subject to strict regulations, segmentation errors become very expensive. Working with an empresa especializada em segurança e segmentação de redes vpc vnet can reveal blind spots you’ve grown used to, like overly permissive shared services, forgotten bastion hosts, or misaligned IAM and network policies. The key is to treat them as partners, not magicians: demand clear rationales, diagrams, and codified patterns you can maintain. The healthiest outcome is that your own team understands why each boundary exists and knows how to evolve it. In the long run, that shared understanding is what keeps your attack surface under control, even as your cloud footprint keeps expanding.
