Why Zero Trust in the cloud needs a different mindset
Zero Trust in 2026 is less about buying one more security box and more about desmontar velhos hábitos. In a corporate multi-cloud reality, every app, identity and API behaves like a moving target. Classic perimeter controls melt away when workloads jump between AWS, Azure, GCP and on‑prem. Adopting zero trust na nuvem multi cloud means you stop assuming that “internal” equals “trusted” and start validating every request, every time, with strong identity, context and continuous monitoring. Instead of building a giant wall, you design guarded corridors where each step is checked. The upside: attacks become noisy and expensive for the attacker; the downside: you need discipline, automation and ruthless simplification of access paths.
Comparing core approaches to Zero Trust in multi‑cloud
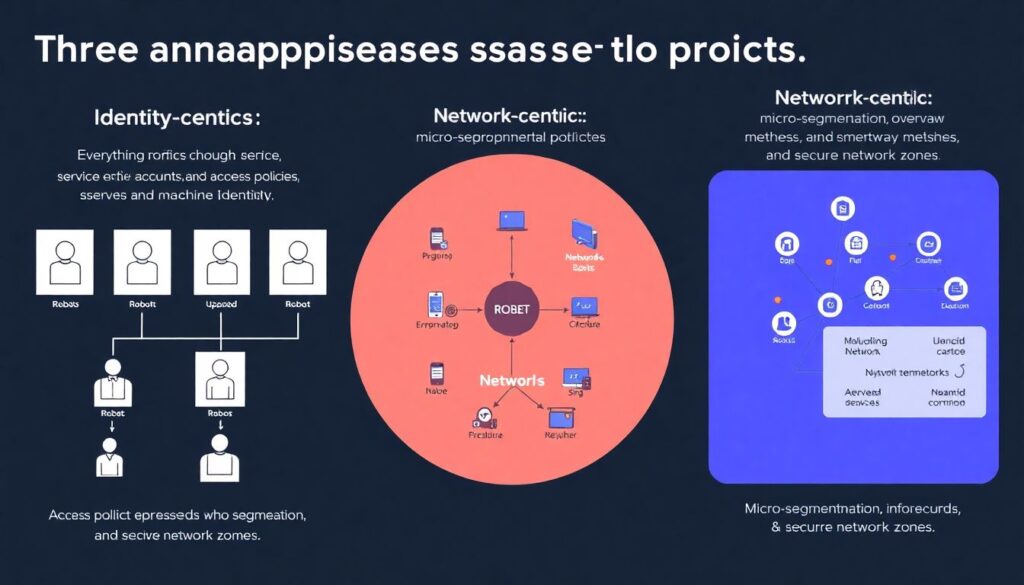
In practice, companies tend to follow three linhas principais. The first is identity‑centric: everything revolves around users, service accounts and machine identities, with policies expressed in terms of “who can do what where”. The second is network‑centric: micro‑segmentation, overlay meshes and software‑defined perimeters that wrap each app in its own mini‑fortress. The third is application‑centric: strong authentication at the app edge, API gateways enforcing fine‑grained policies and secure-by-default development practices. None of these wins alone. In multi‑cloud, identity‑centric controls give you consistency, network‑centric tools reduce blast radius, and app‑centric approaches protect where data is actually used.
Pros and cons of key Zero Trust technologies
Every tecnologia de segurança comes with trade‑offs. Identity providers with conditional access are powerful, but depend heavily on clean IAM hygiene and strong device signals. Micro‑segmentation shrinks lateral movement, yet can be painful to maintain when DevOps teams constantly redeploy services. Zero Trust Network Access (ZTNA) replaces VPNs and simplifies user access, but may struggle with complex legacy protocols. Service meshes deliver per‑request encryption and mTLS between microservices, at the cost of operational complexity. The art is to mix these components so that no single failure opens a broad gap, while keeping the policy model comprehensible for security and platform teams.
How to implement Zero Trust in a messy multi‑cloud world
A practical way to decide como implementar zero trust em ambiente multi cloud is to start from data flows instead of from tools. Map three things: where critical data lives, which identities touch it, and through which applications or APIs. From there, design “trust zones” that are smaller than a VPC but larger than a single pod, and define policies as code around them. Introduce one enforcement layer at a time: first strong identity and MFA, then device posture, then network segmentation and finally continuous behavioral monitoring. Automate policy deployment using CI/CD, so that every new environment inherits the same guard‑rails without manual heroics.
Non‑obvious and unconventional Zero Trust tactics

To go beyond padrão, treat every cloud account as disposable. Instead of one massive shared account per provider, create short‑lived project accounts with tightly scoped roles, nuked after the initiative ends. Another hack: use “negative space” analytics. Instead of only looking for anomalies, also flag flows that are mysteriously quiet; an attacker who disables logging or health checks becomes visible by absence. Consider building an internal “security broker” service: apps never talk directly to cloud APIs, they ask this broker, which enforces Zero Trust policies centrally. This flips the model from chasing each new service to guarding one critical gateway.
When to choose managed Zero Trust platforms vs DIY
Choosing soluções zero trust para empresas na nuvem usually oscillates between buying a managed stack and assembling your own from open components. Managed offerings reduce integration pain and give you unified logs and policy UI, great for teams without deep platform skills. However, they can become expensive and may not support every exotic protocol or legacy workload. A do‑it‑yourself mix of identity provider, ZTNA, service mesh and custom automations yields maximal flexibility, but requires stronger architecture governance. A hybrid path often works best: managed identity and access management for users, plus curated open‑source for internal service‑to‑service protection.
Key building blocks to prioritize first
In a multi‑cloud rollout, not everything needs Zero Trust re‑engineering on day one. Focus initially on three pilares: identity, visibility and least privilege. Ensure all human and machine identities converge on a strong provider with centralized policies. Standardize logging and telemetry before you add more controls; you can’t protect what you can’t observe. Finally, aggressively prune excessive permissions in cloud roles and Kubernetes service accounts. Quick‑win examples include:
– Replacing shared admin accounts with just‑in‑time, time‑bound elevation
– Forcing device checks for privileged actions, not only at login
– Segmenting management planes from workloads with separate identities and networks
Zero Trust and the reality of corporate cloud culture

Purely technical designs fail when they ignore como as pessoas realmente trabalham. Developers hate fragile tunnels and opaque error messages. Operations teams fear policies that break production at 3 a.m. To make segurança zero trust em cloud corporativa sustainable, bake security into developer workflows: policy‑as‑code in Git, templates that already include sidecars, identities and logging. Give product teams self‑service “safe paths” instead of long approval chains. Run game days where you simulate insider abuse or credential theft and tune your policies based on what actually happens, not only on what is written in architecture diagrams.
Trends and experiments shaping Zero Trust in 2026
By 2026, three tendências ganham força. First, identity becomes richer, powered by continuous signals: behavioral biometrics, keystroke patterns and fine‑grained device telemetry steer real‑time risk scores. Second, AI‑assisted policy generation learns from existing flows, proposing guard‑rails that match typical behavior while flagging risky new paths. Third, “local first” security pushes pieces of your policy engine closer to apps via WebAssembly filters and smart SDKs. A plataforma zero trust para multi cloud corporativo increasingly looks like an adaptive fabric rather than a static gateway, able to reconfigure routes and permissions as business processes evolve.
Evaluating vendors without losing control
When evaluating external partners, avoid encantamento com dashboards brilhantes. Ask how their controls map to your identity provider, CI/CD pipelines and incident workflow. Demand open standards: OIDC, OAuth, SAML, SPIFFE/SPIRE, and integration with your existing observability stack. Vendors that trap policies in a closed UI will slow you down later. Look for strong support of infrastructure‑as‑code so you can version and review security changes like application code. Above all, require clear escape hatches: the ability to export policies, logs and configurations if you decide to move away. Zero Trust is a long‑term journey; vendor lock‑in should not be.
Practical checklist to get started this quarter
To move from slideware to prática em poucos meses, work through a short but focused checklist. Start by defining the critical business scenarios you must protect this year, not an abstract “everything”. Then:
– Centralize identity for users and services, with MFA and basic device checks
– Standardize logging across all clouds and route to a single analytics stack
– Introduce ZTNA for admin and developer access, retiring legacy VPNs stepwise
– Pilot micro‑segmentation or service mesh in one non‑critical workload
From there, iterate: review incidents, adjust policies, and slowly widen Zero Trust coverage without derailing delivery deadlines.