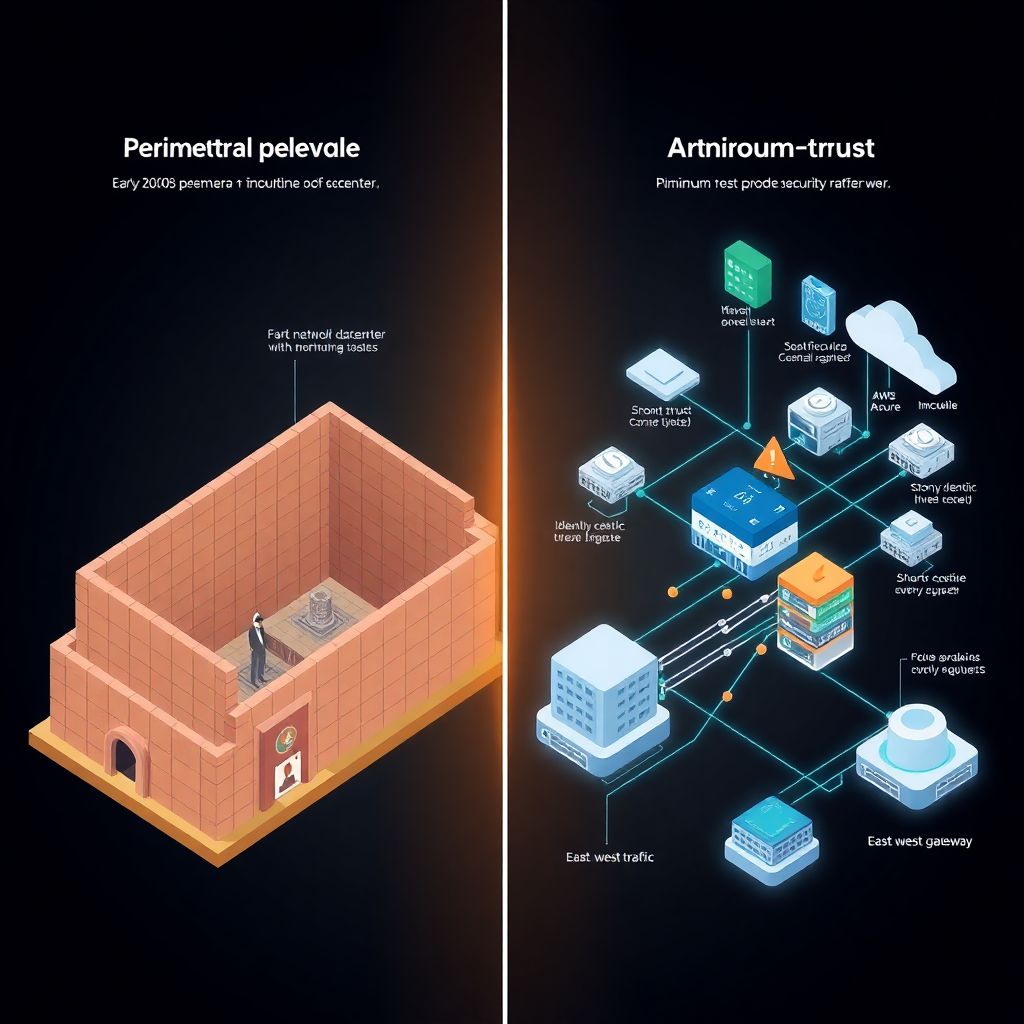
From perimeter firewalls to zero trust na nuvem
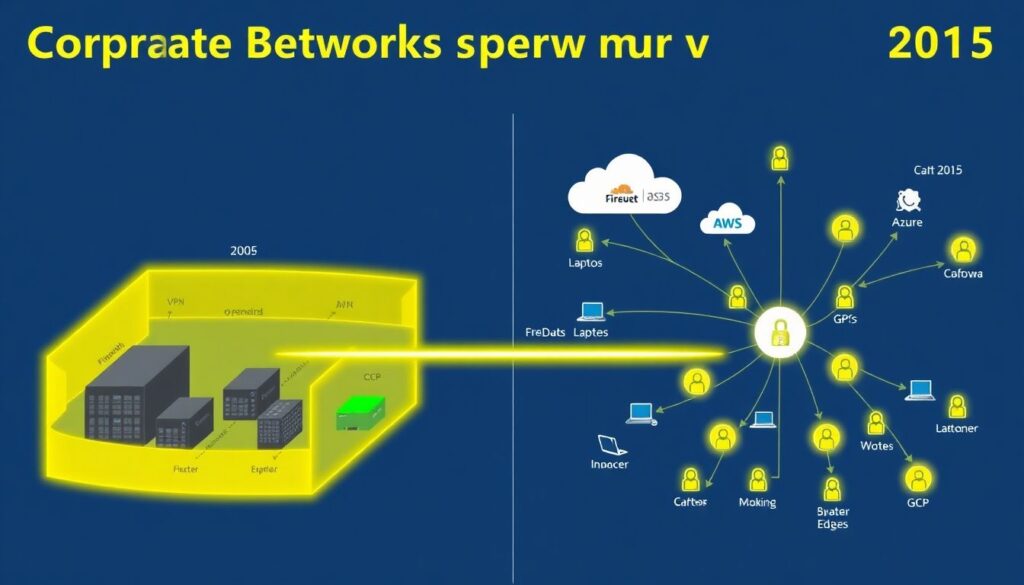
Back in the 2000s, most companies trusted anything inside the corporate LAN and distrusted only the “outside”. VPNs, firewalls and IDS formed a hard edge, while workloads stayed concentraded in one datacenter. Around 2015, as AWS, Azure and GCP gained mass adoption, attackers began targeting identity, APIs and misconfigured storage instead of the perimeter. By the early 2020s, ransomware-as-a-service, supply‑chain breaches and remote work made the old model useless, paving the way for segurança zero trust em ambientes multicloud as the default blueprint.
Core ideas behind minimum‑trust architectures
Zero Trust is often summarized as “never trust, always verify”, but in practice it is about continuous, context‑aware authorization. Every request is evaluated using identity, device posture, workload metadata and behavior analytics. Instead of flat networks and shared secrets, you rely on strong identity, short‑lived credentials and encrypted, authenticated channels between services. In 2026, compliance frameworks and regulators already assume you at least have a roadmap for como implementar zero trust na nuvem, especially if you process sensitive or regulated data across multiple clouds.
Necessary tools and building blocks
To implement a consistent model of confiança mínima, you will mix cloud‑native and third‑party controls. Identity‑centric access is anchored in an IdP with SSO, MFA and conditional access, feeding policies to gateways and proxies. You combine a platform de segurança zero trust na nuvem with CASB and SWG to broker user access to SaaS, and you rely on service mesh or API gateways to secure east‑west traffic. For visibility, you need centralized logs, UEBA, CSPM and CNAPP, so policies stay aligned with what really runs in each cloud account or subscription.
Step‑by‑step process: from inventory to enforcement
The safest way to adopt soluções zero trust para cloud e multicloud is to phase them in by domain rather than “big bang”. Start by mapping business‑critical flows, not just IP ranges: who accesses what, from where, and using which identities. Then you can incrementally replace implicit trust with explicit, machine‑readable policies. A pragmatic plan typically spans identity, network, workloads and data, with quick wins in MFA, least‑privilege IAM and secure remote access before you touch deeper application refactoring.
Practical rollout roadmap
1. Discover and classify identities, devices, apps, APIs and data across all clouds.
2. Harden identity with MFA, phishing‑resistant tokens and conditional access for admins and workloads.
3. Segment access using private access gateways, microsegmentation and service mesh for inter‑service calls.
4. Centralize policy in a unified engine and propagate it to cloud‑native controls and proxies.
5. Continuously monitor behavior, adapt policies, and automate remediation when drift or anomalies appear. This is the essence of como implementar zero trust na nuvem without paralyzing teams.
Troubleshooting and avoiding common pitfalls

When you start enforcing granular policies, the first symptom of misconfiguration is usually broken access for legitimate users or services. To troubleshoot, always check evaluation logs from your zero trust controllers, then correlate with cloud audit logs and application traces. Many outages come from mismatched identity claims, clock skew affecting token validity, or forgotten legacy dependencies bypassing proxies. In multicloud, be careful with subtle differences in IAM semantics and network constructs, otherwise segurança zero trust em ambientes multicloud turns into a patchwork that is hard to reason about and debug.
Keeping the model sustainable in 2026 and beyond
Zero Trust is not a one‑time migration, but an operating model. To keep it viable, you need strong automation, declarative policies and a culture where engineers treat identity and policy as first‑class design elements. In 2026, the most mature teams embed policy‑as‑code in CI/CD, test access paths alongside unit tests, and routinely run attack simulations against their zero trust na nuvem controls. Over time, this reduces manual exceptions, limits blast radius for new vulnerabilities, and turns your multicloud footprint into something you can actually defend at scale.