Why resilience in the cloud matters
From backup to full business survival
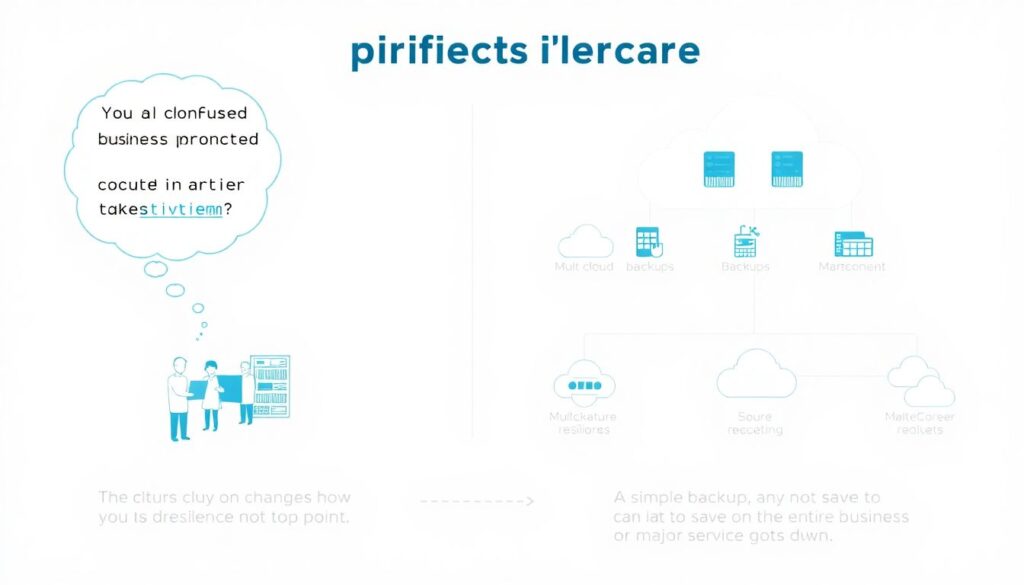
When people first move systems to the cloud, they often think “the provider takes care of everything” and stop there. In reality, cloud only changes *how* you design resilience, not *whether* you need it. A simple backup will save your data, but it will not necessarily save your business when a region goes down, a ransomware attack hits, or a human error wipes the wrong database. That’s where the trio backup, disaster recovery and business continuity comes in. Together they decide if your team spends an outage calmly following a playbook, or panicking in chat threads while revenue silently evaporates.
Key statistics and market trends
Numbers here are quite sobering. According to Uptime Institute, most serious outages now cost above 100,000 USD, and a growing share crosses the 1‑million mark, largely because so many processes have gone digital. At the same time, Gartner and other analysts observe double‑digit annual growth for serviços de disaster recovery em nuvem as companies abandon secondary data centers in favor of managed platforms. Forecasts up to 2030 point to DR and continuity as some of the fastest‑growing segments of cloud spending, driven by regulation, cyber‑risk and the simple fact that customers no longer tolerate hours of downtime.
Core building blocks: backup, disaster recovery, continuity
Backup in the cloud without illusions
Cloud backup looks deceptively easy: tick a checkbox, pick a storage tier and you feel safe. For backup em nuvem para empresas this illusion is dangerous. Data must be versioned, encrypted, tested for restoration and, ideally, stored in more than one region or provider. Newcomers often forget retention rules and discover too late that logs and snapshots older than 30 days are gone. Others store backups in the same account and region as production, so a misconfigured script or compromised key wipes both. The goal is boring reliability: automated policies, immutable copies and a documented restore process, repeated often enough that everyone trusts it.
Disaster recovery as a service

Disaster recovery is about time: how quickly you can bring critical services back and how much data you can afford to lose. Many clouds now offer soluções de recuperação de desastres na nuvem that replicate virtual machines, containers or databases to another region and orchestrate failover. The catch is that configuration details matter: DNS, networking, secrets, backups of configuration repositories and CI/CD pipelines themselves. Beginners regularly test only database failover and forget external dependencies like payment gateways or identity providers. Effective DR considers the whole system graph, not just the “obvious” core. If one missing firewall rule blocks traffic, your shiny DR plan is pure theory.
Business continuity as an ongoing practice
Business continuity looks beyond servers and storage to ask, “How do we keep serving customers under stress?” A plano de continuidade de negócios na nuvem connects technology with people and processes: communication channels, manual workarounds, decision trees for prioritizing which services to restore first. Organisations new to the topic often write a thick PDF once for an audit and never rehearse it. During a real incident nobody remembers where the document lives, let alone its content. Mature teams treat continuity like fire drills: short, frequent and realistic. They simulate cloud region outages, run “game days” and use the findings to update both infrastructure and playbooks.
Designing an arquitetura de TI resiliente em cloud
Principles and reference patterns
A solid arquitetura de TI resiliente em cloud rests on a few simple but demanding principles: eliminate single points of failure, isolate blast radius, automate recovery and observe everything. In practice that means using multiple availability zones, sometimes several regions, infrastructure as code, health checks and auto‑healing. Beginners frequently over‑engineer stateless microservices while leaving stateful layers—databases, queues, file stores—sitting in a single zone. Another trap is ignoring data consistency when replicating across regions, promising unrealistic RPO and RTO values to management. Good design starts from business impact: which systems really need seconds of RPO, and which are fine with hours if that keeps costs acceptable?
Economic dimension: cost vs risk
Resilience can look expensive until you compare it with the price of downtime. Finance, healthcare and e‑commerce players often measure lost revenue per minute; others factor in legal penalties and reputational damage. Cloud helps here by letting you scale protection gradually instead of building a full secondary data center on day one. You can keep a warm standby environment with minimal capacity, then scale it up during failover. Still, a frequent rookie mistake is turning on every high‑availability option without checking utilization, then being shocked by the bill. The sweet spot is explicit trade‑offs: tie each resilience feature to a quantified business risk.
Frequent beginner mistakes and how to avoid them
Technical traps
New teams migrating to cloud resilience repeat a small set of technical sins. Typical examples include storing backups and production in the same account, relying on manual runbooks that nobody tests, or assuming that “multi‑AZ” automatically means multi‑region. Others use snapshot‑based backups without validating application‑level consistency, discovering corruption only during a crisis. To keep it practical, watch out for these patterns:
– No automated, scheduled restore tests from backups
– DR environments that drift from production due to manual changes
– Monitoring focused on uptime, not on recovery success and data integrity
Fixing these requires discipline, not exotic tools, and should start early.
Organizational blind spots
Many failures in continuity planning are not about technology at all. A classic mistake is treating resilience as a one‑time project owned solely by IT. When a real outage hits, customer support, legal, marketing and operations suddenly discover they were never part of the plan. Another blind spot is lack of clear roles: who declares disaster, who talks to the press, who decides to fail back. To avoid this, weave resilience into everyday routines:
– Include DR and continuity scenarios in onboarding and training
– Run joint simulations with technical and business teams
– Review risks and recovery objectives at each major product change
That way, cloud resilience becomes a shared habit rather than a dusty checklist.
Impact on industries and future outlook
How sectors are changing
As more organisations rely on cloud platforms, resilience is quietly reshaping entire industries. Banks use backup em nuvem para empresas combined with strict compliance controls to modernize legacy cores without sacrificing availability. Hospitals adopt serviços de disaster recovery em nuvem to protect electronic health records and ensure life‑critical apps stay online during local outages. Manufacturers link factory systems to resilient cloud backends so production lines keep running even if one site is hit by a flood or power failure. In many regulated sectors, demonstrating robust cloud continuity is already a prerequisite for partnerships, tenders and cross‑border data flows, not just an internal best practice.
What the next decade is likely to bring
Looking ahead, resilience in cloud will increasingly lean on automation and AI‑assisted operations. Expect more self‑healing platforms that detect anomalies, trigger failover and even rehearse DR scenarios autonomously. Regulatory pressure will continue to rise, requiring auditable evidence that soluções de recuperação de desastres na nuvem and continuity plans actually work, not just exist on diagrams. Economically, the line between security, observability and DR services will blur as vendors bundle them into integrated resilience offerings. For teams starting now, the biggest advantage is cultural: building a mindset where designing, testing and improving resilience is as normal as writing code or shipping features.