Why cloud cyber‑security is about to get even messier
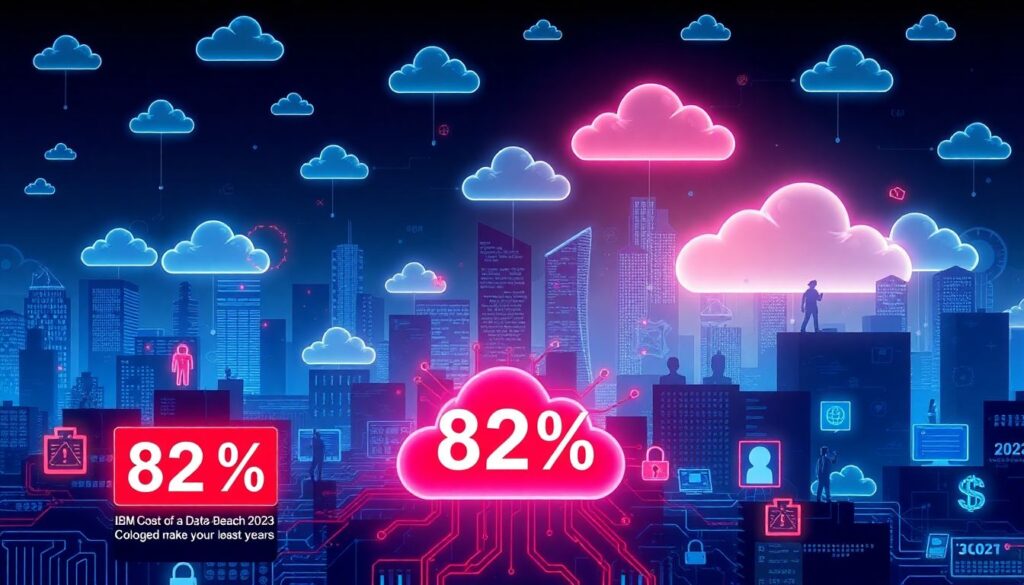
Cloud isn’t a “future trend” anymore, it’s the default. Over the last three years, that shift radically changed the threat landscape. IBM’s Cost of a Data Breach 2023 report shows that breaches now involve cloud‑hosted data in 82% of cases, up from clearly lower levels in 2021, and the average breach costs 4.45 million dollars. At the same time, more small and mid‑sized companies rushed to SaaS and public cloud during and after the pandemic, often without a mature security strategy. This mix of massive adoption, patchy governance and hungry attackers sets the stage for the next year: more automation, more identity abuse, and much more pressure on teams that already feel overloaded.
Over 2021–2023, ransomware shifted hard into cloud and hybrid environments, hitting backups, object storage and virtual machines rather than only on‑prem servers. Industry incident reports show that cloud misconfigurations remain one of the top root causes of breaches, repeatedly responsible for exposed databases and storage buckets. At the same time, supply‑chain attacks have grown: compromise one software vendor or managed provider and you may quietly reach hundreds of customers at once. Going into 2026, the cloud story is no longer just “put a firewall in front of your VPC” but a combination of identity protection, data‑centric controls and continuous monitoring that understands how each cloud service is actually used.
Emerging cloud threats for the coming year
The first big wave to watch is identity‑centric attacks. As more workloads move to serverless and containers, classic network perimeters blur, and identity becomes the real entry ticket. Attackers increasingly steal OAuth tokens, abuse service principals and exploit overly permissive IAM roles instead of brute‑forcing passwords. Over the last three years, several major breaches started with a single compromised cloud admin account, then snowballed through lateral movement between SaaS, IaaS and on‑prem AD. Expect the next year to bring more attacks that never touch a VPN or traditional firewall, but live entirely inside legitimate cloud APIs and admin consoles.
Another fast‑maturing threat is AI‑assisted intrusion. By 2023, red teams were already using large language models to speed up phishing content, triage loot from compromised accounts and generate exploit scripts. Attackers do the same, but with fewer guardrails. We’re seeing more convincing multilingual phishing that references real internal projects, faster discovery of misconfigured storage, and automated scoping of exposed Git repositories. Looking ahead, the real danger is not “superhuman” AI but the way basic capabilities at scale lower the barrier to entry. That means more mid‑level criminals can run campaigns that once demanded skilled specialists, pushing overall attack volume up even when each individual incident feels routine.
Supply‑chain risk in cloud services will stay in the spotlight. Organizations now rely on dozens or hundreds of SaaS platforms, many tied directly into their identity provider or finance systems. The 2020–2023 wave of high‑profile software supply‑chain incidents pushed vendors to improve, but it also taught attackers that compromising a single widely used integration platform can silently expose thousands of tenants. For the next year, expect more focus on malicious packages in public repositories, tampered update mechanisms and abused third‑party support portals. Every new connector that makes life easier for your operations team can also become a ready‑made bridge for an intruder if its security posture is weak or poorly monitored.
Key numbers from the last three years (and what they imply)
Even without precise global figures for 2024–2025 yet, some trends are clear. IBM reports that the average breach cost has climbed for thirteen years in a row, reaching 4.45 million dollars in 2023, with incidents involving cloud environments slightly above that average. Public breach reports over 2021–2023 consistently show that misconfiguration and credential theft dominate as initial vectors in cloud incidents, together accounting for a large share of cases. Meanwhile, organizations with mature automation and AI‑driven detection cut breach lifecycles by around 100 days and reduce costs by over a million dollars compared with less automated peers, a pattern unlikely to reverse in the near term.
Ransomware data from multiple incident‑response firms between 2021 and 2023 shows both good and bad news. On the upside, some sectors reported fewer successful encrypt‑and‑extort events thanks to better backups and law‑enforcement pressure. On the downside, attackers shifted tactics toward double and triple extortion: stealing data from cloud storage or SaaS first, then threatening leaks even if recovery is possible. At the same time, business email compromise tied to cloud mail and collaboration platforms steadily grew, with median losses per incident often outpacing classic ransomware payments. Going into 2026, many analysts expect this blend of data theft, extortion and subtle financial fraud in cloud services to remain more profitable than “loud” destructive attacks.
Projections from major cloud providers and security vendors suggest that by 2025, a strong majority of new enterprise applications will be built “cloud‑native first”, leveraging managed databases, message queues and serverless functions instead of self‑hosted components. That accelerates innovation, but it also magnifies the impact of a single misconfigured template or vulnerable open‑source dependency reused across dozens of microservices. At the same time, spending on soluções de cibersegurança cloud has grown steadily year over year, driven by demand for integrated platforms that cover identity, network, data and posture in one place. The paradox is that higher spending does not automatically mean lower risk unless governance and skills keep pace with tool adoption.
New defense models: from perimeter to continuous context
The dominant strategic trend is the shift from perimeter security to continuous, identity‑aware protection. Zero trust is no longer just a buzzword in slide decks; in practical terms, it means every request to a cloud resource is evaluated based on user identity, device health, location, behavior and sensitivity of the data involved. Over the last three years, this approach moved from experimental pilots into mainstream roadmaps for segurança em nuvem para empresas of all sizes, though smaller organizations often adopt it gradually via their identity provider rather than full‑blown custom architectures. The next year will likely see more fine‑grained policies that adapt in real time instead of static rules written once and forgotten.
At the same time, security is getting closer to the development and operations lifecycles. “Shift‑left” ideas like embedding policy checks into CI/CD and Infrastructure as Code templates are now common in cloud‑native teams. Practical examples include scanning Terraform or CloudFormation for dangerous default configurations, enforcing encryption at rest by policy, and blocking deployments if public exposure is not explicitly approved. Over 2021–2023, organizations that combined these automated controls with strong incident‑response playbooks reported significantly fewer “wide‑open” storage buckets and exposed admin interfaces. In the coming year, this integration should deepen as developers rely more on pre‑approved modules and guardrails rather than one‑off manual fixes after audits.
Automation and managed services will play an even greater role. Many teams are already leaning on serviços gerenciados de segurança em nuvem to run 24/7 monitoring, threat hunting and compliance checks they simply do not have the staffing to handle internally. Cloud‑native SIEM and XDR offerings can ingest logs from multiple providers, correlate suspicious patterns and raise high‑quality alerts faster than traditional tools. For 2026, expect more organizations to combine internal expertise with external “eyes on glass”, letting their own analysts focus on understanding business context and response decisions while providers handle the heavy lifting of data collection, correlation and first‑line triage across sprawling multi‑cloud estates.
Necessary tools for modern cloud defense
To translate strategy into daily practice, you need a coherent toolkit rather than a random pile of dashboards. At the foundation sits a strong identity and access management system integrated with single sign‑on and multi‑factor authentication across your main clouds and SaaS platforms. On top of that, cloud‑security‑posture‑management tools continuously scan for misconfigurations, while data‑loss‑prevention and encryption services protect sensitive information wherever it lives. Network‑level visibility from cloud‑native firewalls and micro‑segmentation still matters, but it is now complemented by behavioral analytics and threat‑intelligence feeds. Finally, platforms de segurança cloud para negócios aim to bring these capabilities into one console, reducing alert fatigue and helping smaller teams actually act on what they see instead of drowning in logs.
For many organizations, the “tool” question is also about architecture choices. Wherever possible, rely on native controls from your primary cloud and SaaS providers before layering third‑party solutions. This reduces integration complexity and often improves signal quality, because providers see low‑level events outsiders cannot. However, native tools can be biased toward a single ecosystem, so if you run multi‑cloud you may still want a unifying layer to normalize telemetry and policies. Over the last three years, some of the most effective environments combined cloud provider features, a central identity provider, and a carefully chosen detection and response platform instead of chasing every niche product that claims to solve a hypothetical problem.
Step‑by‑step process to raise your cloud security game this year

First, map your actual cloud footprint. Many teams underestimate how many SaaS applications, shadow accounts and experimental projects they have. Spend time discovering which providers hold critical data, which admin roles exist, and how they authenticate. Next, prioritize what matters: crown‑jewel data stores, key production workloads and the identities that can change or delete them. Once you know this, you can design layered proteção contra ataques cibernéticos em cloud that focuses effort on real impact zones instead of treating every minor sandbox like a top‑secret environment, which quickly becomes unmanageable and wastes scarce security bandwidth.
After that, harden identity and access. Enforce strong MFA on admin accounts and high‑risk actions, review stale privileges and adopt least‑privilege principles for both human and machine identities. Then address configurations systematically: use policy‑as‑code to declare what “secure” looks like, and have CI/CD pipelines and posture‑management tools block or flag deviations. Parallel to this, set up central logging and monitoring that covers API calls, authentication events and key data access. Over the next months, iterate by running tabletop exercises and red‑team simulations to validate that alerts fire as expected, that runbooks are clear, and that business stakeholders understand their role in decisions during real incidents.
Finally, bake security into how you build and buy. For new development, standardize on secure templates and libraries, and require threat modeling for any feature that touches sensitive data or new third‑party integrations. For procurement, include clear security requirements and incident‑handling obligations in contracts with cloud and SaaS vendors. Over the last three years, many companies learned the hard way that unclear responsibilities during a shared‑responsibility dispute cost time and money during crises. In the coming year, treat new providers as extensions of your own attack surface; vet their architectures, ask about independent audits and ensure they support the logging and integrations your detection stack needs.
Troubleshooting and avoiding common pitfalls
When organizations struggle with cloud security, it is rarely because of a missing feature; it is usually about visibility, ownership or overload. One frequent issue is conflicting configurations across multiple accounts and providers, leading to confusing alerts and gaps. To troubleshoot this, start by consolidating identity where possible, then standardize baseline policies and naming conventions. If your analysts cannot quickly tell which environment or sensitivity level an alert refers to, you will waste precious incident‑response time. Another recurring pain point is noisy detection rules that bury important signals. Here, work iteratively: tune or disable low‑value rules, focus on high‑risk behaviors like new global‑admin assignments or unusual data exfiltration patterns, and review effectiveness monthly.
Skills and communication gaps also cause subtle but serious problems. Cloud engineers may see security teams as blockers, while security staff feel overwhelmed by the pace of change in services and APIs. To fix this, embed security champions inside product and platform squads, give them time and training, and measure success by reduced misconfigurations and faster remediation rather than by the number of tickets opened. If an incident does occur, treat it as a learning opportunity: conduct blameless post‑mortems, look at which defenses worked and which failed, and update runbooks and automations accordingly. Over the next year, organizations that treat troubleshooting as a continuous improvement loop, not a one‑off fire drill, will be far better positioned to handle whatever new threats emerge.
Looking ahead: making cloud security sustainable
The direction of travel is clear: more cloud, more complexity and more professionalized attackers. Yet the past three years also show that disciplined, well‑instrumented environments can dramatically reduce both breach frequency and impact, even without gigantic budgets. The focus for the next year should not be chasing every new buzzword, but consolidating around a few well‑integrated soluções de cibersegurança cloud, strengthening identity, and aligning developers, operations and security around shared guardrails. With realistic priorities, careful use of automation and, where it makes sense, trusted managed partners, segurança em nuvem para empresas can evolve from a constant source of anxiety into a predictable, manageable part of doing digital business at scale.
