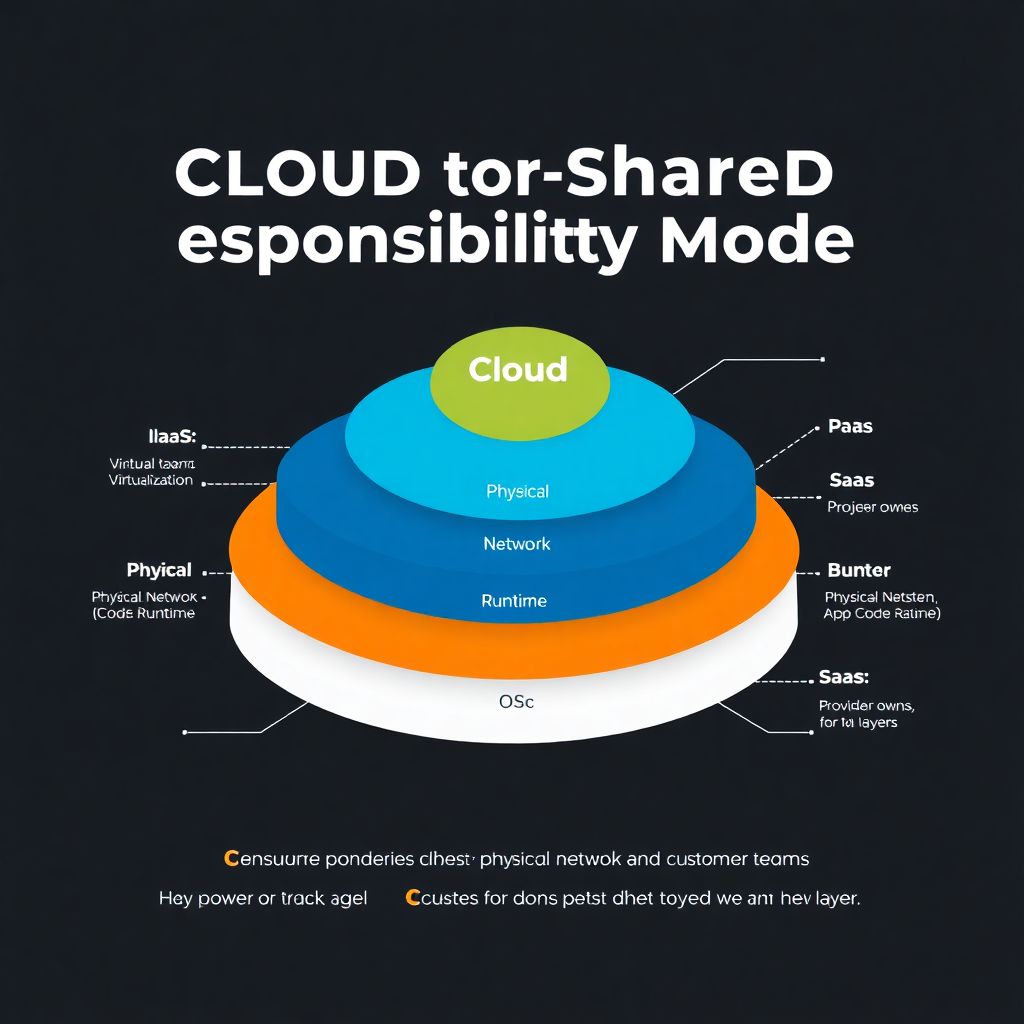
Por que o modelo de responsabilidade compartilhada importa de verdade
When teams move to the cloud, many assume “the provider takes care of security”. Then an incident happens and everyone discovers the famous modelo de responsabilidade compartilhada cloud the hard way. In practice, this model is simply an explicit contract: the provider secures the cloud, you secure what you put in it. The twist is that the border between one and the other changes depending on the service (IaaS, PaaS, SaaS). If your team doesn’t internalize this logic, you end up with well‑protected infrastructure running horribly misconfigured apps, open S3 buckets, or leaked credentials pushed to Git, all technically “in the cloud” but still entirely your fault.
Termos essenciais, sem enrolação
Let’s lock down a few terms so everyone on the team speaks the same language. “Provider” is your AWS, Azure, GCP, etc. “Customer” is your company, but concretely: Dev, Ops, Security, Data, and even Legal. “Security OF the cloud” covers physical datacenters, networking fabric, hypervisors, and the base services. “Security IN the cloud” is your configs, data, IAM, code, keys, pipelines. When people ask responsabilidade compartilhada aws o que é, they’re actually asking: exactly which layer stops being Amazon’s concern and starts being yours, and how that boundary shifts between EC2, RDS, Lambda, and fully managed SaaS products you plug in.
Diagrama mental: onde termina o provedor e começa sua equipe
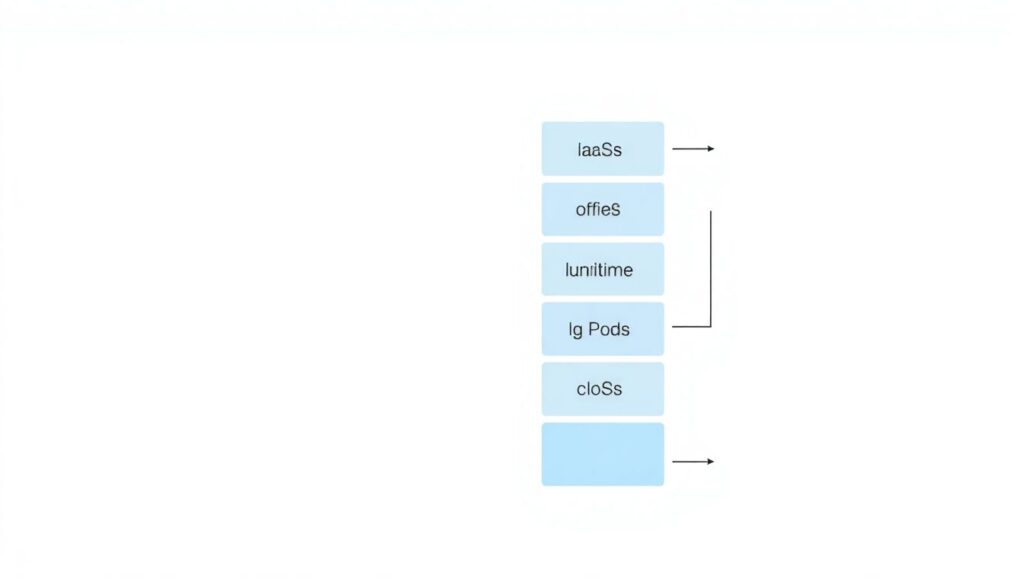
Imagine a vertical stack diagram in plain text. From bottom to top:
[Physical] → [Network] → [Virtualization] → [OS] → [Runtime] → [App Code] → [Data].
Now map it to service models. For classic IaaS, like a VM, the provider fully owns the first three layers; you own OS hardening up. For PaaS, the provider also grabs OS and runtime; you keep app and data. In SaaS, they essentially run everything; you only handle business logic, identities, and data governance. This diagram is the core of responsabilidade do provedor vs cliente na nuvem and becomes your checklist for who patches, who monitors, and who writes runbooks.
Segurança em nuvem: além da teoria do modelo
Talking about segurança em nuvem modelo de responsabilidade compartilhada without touching real‑world failure modes is just theory. The provider invests billions in hardening hypervisors, redundancy, and DDoS protection; that’s not where most companies break. Incidents almost always come from the “IN the cloud” part: overly permissive IAM roles, public storage, missing TLS, exposed management endpoints, secrets in code, or shadow IT spinning up services outside official guardrails. Understanding the shared model means accepting that “we’re on AWS” doesn’t magically encrypt your business logic, validate your JWT tokens, or rotate the service account keys some intern put in a CI variable three years ago.
Comparando com modelos on‑prem e outsourcing clássico
On‑prem, you own everything: racks, power, cooling, hypervisors, OS, apps, backups, DR. You’re the provider and the customer at the same time, and the shared model is purely internal (infra vs app teams). In a classic outsourcing setup, you push responsibility to a third party by contract, but boundaries are still fuzzy and audits painful. In the cloud, the model is industrialized: each provider publishes a clear diagram of responsibilities and compliance scope. This transparency is a step up from legacy hosting, but it also removes excuses. When a misconfiguration leaks data, there’s rarely ambiguity: it’s documented as your side of the deal.
Responsabilidade do provedor na prática: o que você pode assumir como dado
Cloud providers handle tasks that would be nearly impossible for a single company to replicate: global peering, hardware lifecycle, secure boot, tamper‑evident logs at the infrastructure level, and compliance with dozens of certifications. For your threat model, you can generally treat physical access control, hypervisor isolation, and base service availability as given, and design above that line. However, “given” doesn’t mean “unchecked”: you still need to read SOC reports, understand shared audit scope, and make sure contractual SLAs match your RPO/RTO. An unconventional move is to bring InfraSec into procurement early, so they negotiate addenda that reflect your real risk posture instead of accepting default terms.
Responsabilidade da sua equipe: onde o erro mais dói
Your team owns everything the provider calls “customer configuration”. That includes IAM policies, network segmentation, encryption choices, key management strategy, backup policies, and zero‑trust access around cloud consoles and APIs. In many incidents, root cause is boring: a wildcard allow in IAM, a forgotten security group, a missing WAF rule. To operationalize this, map each configuration domain to an owner: Security for guardrails and policies, Platform for baseline modules, Dev teams for app‑level controls. Treat cloud accounts as products with SLAs. Without explicit ownership, the gray areas of the modelo de responsabilidade compartilhada cloud become nobody’s job and everyone’s problem.
Desenho textual de responsabilidades por camada

Let’s refine that earlier diagram into a practical checklist you can paste into your runbooks:
– Provider (always): Physical datacenters, base network fabric, core identity of the platform, base logging for infrastructure events, managed control planes.
– Shared: Service configs (e.g., DB encryption flags), network edges (VPNs, Direct Connect, peering), identity federation, resource‑level logging.
– Customer (always): App logic, data classification, IAM roles and groups, client‑side security, secrets handling, CI/CD security.
Treat “Shared” as a negotiation zone: for any new service, ask explicitly “who patches this layer, who monitors it, and where do alerts land?” and document the answer in code and policy, not just in slides.
Melhores práticas que realmente funcionam
When people talk about melhores práticas modelo de responsabilidade compartilhada, they usually list generic tips. Let’s make them actionable. Start with “responsibility blueprints” per service type: EC2 blueprint, RDS blueprint, Serverless blueprint, each stating who builds, approves, and monitors what. Codify them in Terraform/CloudFormation modules, not PDFs. Second, enforce permissions via identity as code: no manual console role tinkering. Third, mandate threat modeling for any internet‑facing workload, with explicit mapping to which threat is mitigated by provider controls and which is yours. Finally, include shared‑model checks in incident post‑mortems: “Did we misinterpret the boundary?” becomes a standard question.
Comparando provedores: nuances entre AWS, Azure e GCP
The high‑level split is similar across providers, but details differ. AWS is verbose and explicit, with lots of service‑specific nuances; hence the frequent question responsabilidade compartilhada aws o que é in security reviews. Azure often blends with existing AD and corporate identity, which shifts identity boundaries subtly. GCP leans heavily on projects, folders, and org policies as the main guardrail mechanism. A non‑obvious strategy is to maintain a “provider abstraction map”: for each control (network isolation, KMS, policy engine, identity), you map the equivalent in each cloud, plus who owns which part. This keeps multi‑cloud from turning into three different security religions.
Estratégias fora do comum para reduzir risco
Beyond the usual checklists, consider some unconventional moves. First, create a “Cloud Red Team Charter” with explicit permission to exploit only customer‑side misconfigurations, assuming the provider is perfect. This forces your org to internalize where real risks live. Second, treat each cloud account or subscription as a “bounded blast radius”: design it so that, if entirely compromised, damage is still acceptable. That pushes you to isolate workloads aggressively. Third, use “security feature flags” in apps to decouple provider features (like KMS keys or private endpoints) from code, so you can rapidly re‑platform between services without rewriting access logic.
Modelo de responsabilidade compartilhada aplicado ao dia a dia
To make the segurança em nuvem modelo de responsabilidade compartilhada part of daily work, embed it into the developer experience. Onboarding to a new project should include a short, visual explanation of which parts the platform handles and which parts the team must own. CI pipelines can run “responsibility linters” that fail builds if resources violate account guardrails. Security training should be contextual: show real incidents from your org where “provider vs customer” was misunderstood, and how to spot similar patterns. Over time, the goal is cultural: developers intuitively ask “Is this my job or the provider’s?” and have a clear, documented place to find the answer.
Checklist final para a sua equipe
To operationalize responsabilidade do provedor vs cliente na nuvem, keep a lightweight internal checklist and review it quarterly:
– Identify critical services and write one‑page “responsibility profiles” for each.
– Map every profile to specific teams and on‑call rotations.
– Automate guardrails with policies as code and account vending.
– Run recurring game‑days simulating provider failures and your own misconfigs.
– Feed all lessons into your blueprints and training.
Shared responsibility only works when it’s visible, automated, and rehearsed; otherwise it’s just a nice diagram sitting in a slide deck no one opens.