Por que IAM em cloud virou assunto sério de vez
If you look back to the late 2000s, cloud identity was almost an afterthought: one root account in AWS, a few shared passwords, maybe a basic SSO. As attacks got more sofisticated and compliance tightened, gestão de identidades e acessos em cloud iam went from “coisa de segurança” to a board‑level concern. From 2020 to 2026, every major breach report repeats the same pattern: over‑privileged accounts, keys forgotten in code, and no visibility. Modern cloud IAM is about treating identity as the new perimeter, with roles, policies and least privilege baked into how you design workloads instead of added later as a patch.
Conceitos fundamentais: identidades, papéis e políticas
At the core of IAM you always have three elements: who, what and how. “Who” are identities: human users, service accounts, workloads, CI/CD pipelines, even serverless functions. “What” are resources: buckets, databases, secrets, queues. The “how” is determined by roles and policies. When you study como definir papéis e políticas iam em cloud, you’re essentially deciding which actions a given identity can perform on specific resources under which conditions, like network origin or MFA. Getting this vocabulary straight is crucial: if your team still confuses user, role and group, your authorization model will quickly become inconsistent and hard to audit.
Ferramentas necessárias para uma boa arquitetura IAM
To run IAM seriously in 2026, you need more than the default console. The core ferramentas de iam para segurança em cloud are the native services (AWS IAM, Azure AD/Entra ID, Google Cloud IAM), but you should layer them with identity providers, secret managers and policy engines. Think of providers like Okta, Auth0, Azure AD or Keycloak for SSO and federation, plus tools such as Vault or AWS Secrets Manager for credentials. On top of that, policy‑as‑code engines (Open Policy Agent, AWS Verified Permissions, Azure Policy) help you keep rules versioned and tested. Finally, you’ll likely add a cloud security posture management platform to continuously scan for misconfigurations and over‑privileged roles before attackers find them.
Ferramentas nativas dos provedores
Each hyperscaler ships its own toolbox. For implementação de least privilege em aws azure gcp, you start with core services: IAM roles, groups and policies in AWS; Entra ID, Azure RBAC and managed identities in Azure; Cloud IAM, service accounts and resource hierarchy in GCP. Complementary pieces like AWS Organizations, Azure Management Groups and GCP Folders help you segment environments by business unit, compliance domain or sensitivity level. Logging tools such as CloudTrail, Azure Activity Logs and Cloud Audit Logs are essential for tracing who did what and when. By combining these primitives carefully, you avoid duplicating identities across projects and keep a consistent access model even as the number of accounts and subscriptions grows.
Desenhando papéis: do caos à arquitetura limpa
Designing roles starts with understanding real workflows, not copying vendor defaults. A common anti‑pattern is granting broad “admin” or “contributor” roles because they “just work” in the beginning. Instead, break down activities: who deploys code, who rotates keys, who reads logs, who touches production data. From there, derive role types: platform operator, app owner, auditor, data analyst, incident responder, and so on. Align those with your organizational structure but keep them slightly more generic so they’re reusable entre equipes. Every time you design a new role, ask which resources it truly needs and which risky actions (delete, change network, modify IAM) should be strictly limited to a smaller SRE or security group.
Como definir papéis de forma sustentável
Sustainable role design means treating roles as products with owners and lifecycle, not as one‑off exceptions. Start with a minimal role catalog and evolve it based on evidence from logs and requests, rather than guesswork. When new projects appear, try first to reuse existing roles; if you must create a new one, document its scope and owner right away. Tie roles to job functions instead of individuals, then use groups to bind people to these functions. The phrase como definir papéis e políticas iam em cloud usually scares teams because they imagine a huge upfront project, but in practice you can iterate: launch a small set of well‑scoped roles, collect feedback, and refine permissions constantly, deprecating unused ones to avoid sprawl.
Políticas: linguagem, condições e versões
Policies are where theory turns into enforcement. JSON‑based document formats in AWS and GCP, and Azure RBAC role definitions, can be verbose and intimidating; yet they’re just structured statements of “allow” or “deny” with conditions. Treat them like code: keep them in Git, review with pull requests, and test in staging. Use conditions aggressively: IP ranges, time of day, required MFA, resource tags or environment labels. This lets you reuse generic policies while still keeping strict boundaries between dev, test and prod. Versioning is non‑negotiable: when an incident happens, you must answer exactly which policy was in effect, who changed it, and which review it went through before deployment.
Melhores práticas de escrita de políticas
To apply melhores práticas least privilege na nuvem, write policies that are narrowly targeted and easy to understand in a single read. Avoid wildcards like “*” in actions or resources unless you’re absolutely sure the blast radius is acceptable and documented. Group related permissions under a single custom role instead of piling multiple built‑in “contributor‑like” roles on one identity. Reference resources by path and tag strategy that matches your resource hierarchy, like folders, projects and environments. Finally, build a small internal library of policy snippets for common patterns (read‑only logs, deploy‑only pipelines, key rotation), so teams stop reinventing the wheel and accidentally granting more than they should.
Implementando least privilege em ambientes multi‑cloud
Least privilege used to be a security slogan; now it’s a compliance requirement. Implementação de least privilege em aws azure gcp begins with visibility: you can’t trim permissions you don’t understand. Use access analyzer tools, IAM recommender features and usage reports to see which permissions are actually used over time. Then, iteratively tighten roles, starting with machine identities, which usually tolerate reduction better than humans. Align privilege levels across clouds conceptually, even if the technical constructs differ. For example, map a “prod‑read‑logs” role in AWS to equivalent Azure and GCP roles. Document these mappings so teams migrating workloads aren’t tempted to temporarily grant full admin “until things stabilize”, which often becomes permanent.
Melhores práticas least privilege na nuvem aplicadas a times
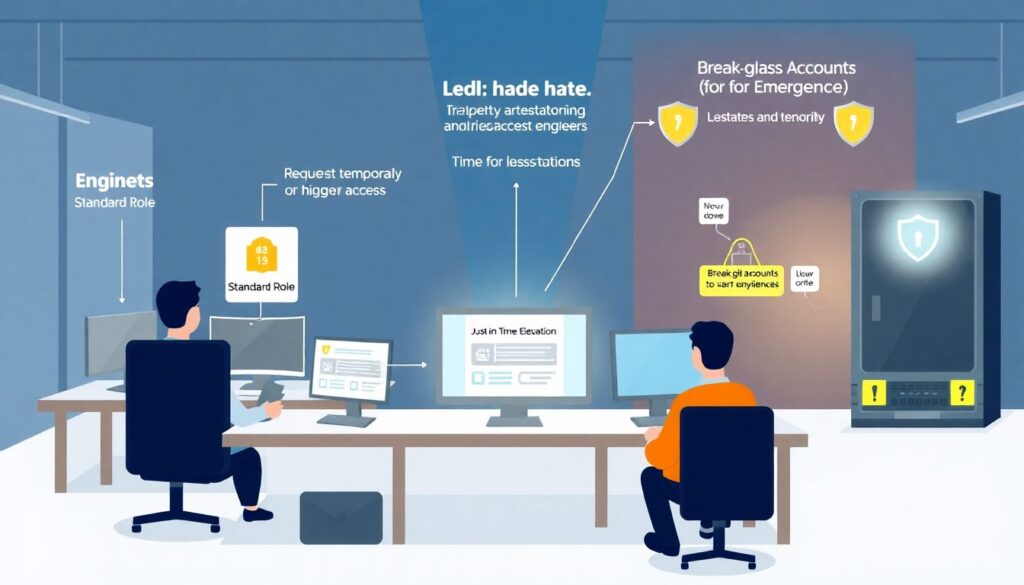
Least privilege is as much about people and process as it is about APIs. Encourage just‑in‑time elevation: engineers work with standard roles most of the time and request temporary higher privileges through an approval workflow with automatic revocation. Use break‑glass accounts for emergencies, stored in secure vaults and monitored heavily. Make sure contractors and temporary staff have expiration dates on their access by default. Regularly run entitlement reviews where managers confirm who still needs which roles. Over time, this becomes routine hygiene rather than a special project, and your access surface stays lean even as your team and footprint grow.
Processo passo a passo para estruturar IAM em cloud
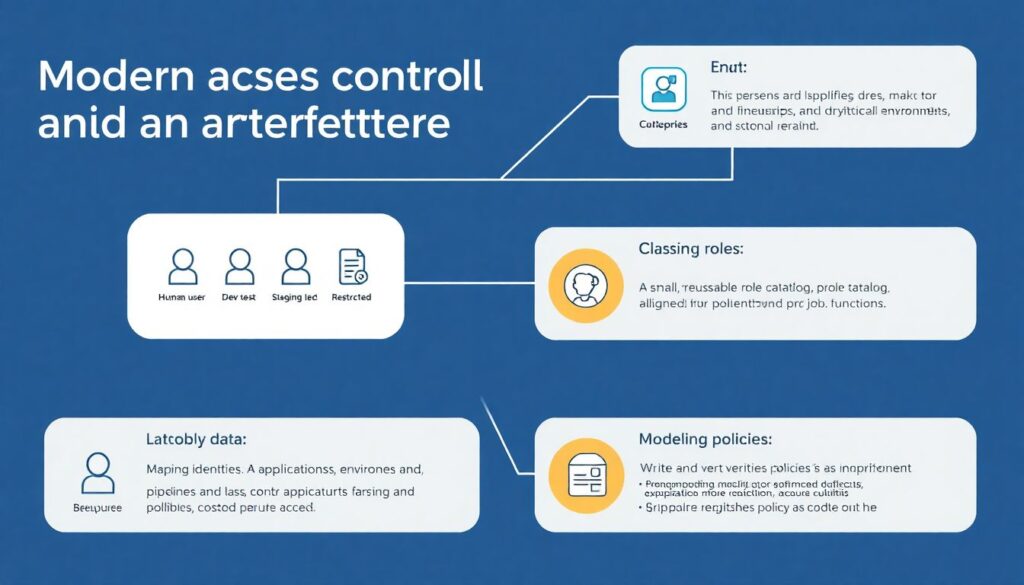
1. Map identities: list human users, applications, pipelines and external partners.
2. Classify data and environments: dev, test, staging, prod, restricted.
3. Definir papéis: design a small, reusable role catalog aligned to job functions.
4. Modelar políticas: write and version policies as code with review gates.
5. Integrar autenticação: connect SSO, MFA and federation with corporate identity.
6. Automatizar concessão: use groups, workflows and tickets instead of manual grants.
7. Monitorar uso: log every access, analyze anomalies and refine permissions.
8. Auditar e revisar: schedule periodic access and policy reviews with clear owners.
Monitoramento e detecção de abusos de acesso
Even the best design won’t survive without monitoring. Turn on audit logs in every account, subscription and project, and centralize them in a security data lake or SIEM. Correlate IAM changes (new roles, trust relationships, key creation) with network and workload telemetry to flag suspicious behavior, such as a low‑privileged service suddenly creating powerful tokens. Build alerts for risky patterns like disabling MFA, modifying logging settings or granting admin roles. Track failed authentication and authorization spikes; they often signal misconfigurations, scripted attacks or leaked credentials. Over time, this observability lets you distinguish between normal operational noise and the early stages of a real incident.
Resolvendo problemas comuns em IAM
Troubleshooting IAM usually starts when someone says “it doesn’t work” without context. First, capture the exact error message and timestamp, then check audit logs for denied actions tied to that identity. Many incidents are due to role assumption not happening as expected, or to a missing condition like a required tag. Another frequent issue is circular trust: roles allowed to assume each other unintentionally, creating escalation paths. When debugging, use temporary diagnostic policies that add granular logging but still follow least privilege, and remove them afterwards. Document every tricky case you solve; these become internal runbooks that shorten future outages and help new team members understand past design decisions.
Erros de design que viram incidentes
Some IAM mistakes are subtle until they explode. Granting a CI/CD pipeline broad admin in the name of speed can turn a compromised build server into a full account takeover. Allowing external identities to assume internal roles without strict conditions on source and audience opens the door to confused‑deputy attacks. Forgetting to restrict access to secret managers and KMS keys effectively nullifies encryption at rest. When investigating incidents, look not only for the immediate misconfigured policy but also for systemic issues: missing peer review, lack of testing environments for IAM, or pressure to “just grant access” without proper analysis. Fixing these root causes raises your baseline security far more than any single patch.
Conclusão: IAM como disciplina contínua
By 2026, nobody serious in cloud treats IAM as a one‑time setup. Robust gestão de identidades e acessos em cloud iam means ongoing engineering work: new services appear, teams change, regulations evolve. If you invest early in clear role design, strong policies, automation and monitoring, IAM stops being a bottleneck and becomes an enabler: developers ship faster, audits run smoother and incident response gets sharper. The key is to keep the system small, observable and adaptable, revisiting assumptions regularly instead of waiting for the next breach or compliance deadline to force rushed and risky changes.