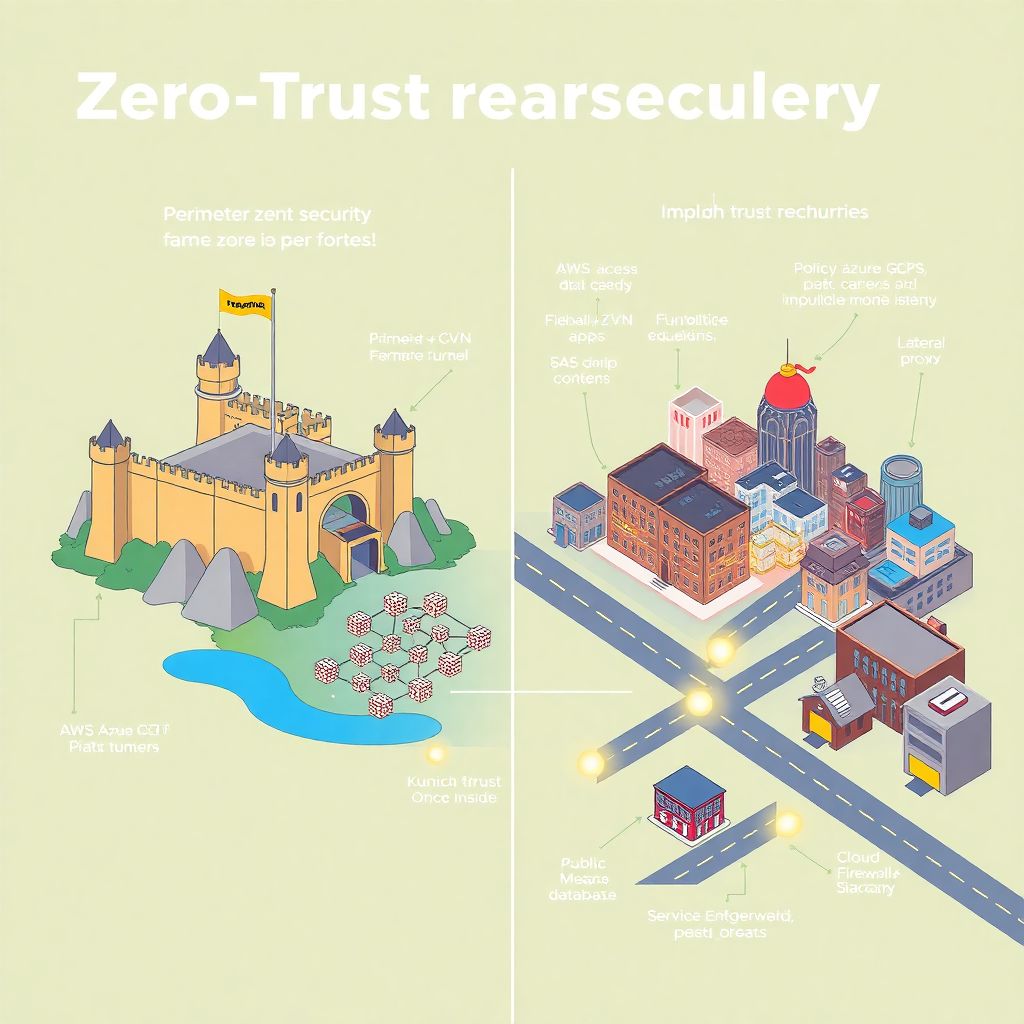
Why Zero Trust in the Cloud Is Different From On‑Prem
Zero Trust in cloud environments looks familiar at first glance—“never trust, always verify” and all that—but in practice, zero trust na nuvem is a different beast from on‑prem. Instead of one well‑guarded data center, you now juggle AWS accounts, Azure subscriptions, GCP projects and maybe a SaaS zoo on top. The old perimeter—firewall + VPN—was like a castle wall; cloud is more like a city with many buildings connected by public streets. That’s why access policies must follow the user, the device, the workload and the data, not just an IP range. A good mental model: you’re replacing “inside vs outside” with “continuous proof that this request deserves this exact action, right now, under these conditions”, no matter which cloud or network segment is involved.
Core Concepts: Clear Definitions Before We Build
What “Zero Trust” Actually Means in Practice
In plain terms, Zero Trust is about killing implicit trust. No user, device, workload or network segment gets a free pass just because of location or prior authentication. Instead, each request is checked against identity, device posture, context (time, geolocation, behavior) and sensitivity of the target resource. Technically, you define a “trust policy” layer that sits between everything and everything else. [Diagram: User/Device → Policy Engine → Policy Enforcement Point → App/Data]. In multi‑cloud, those Policy Enforcement Points (PEPs) live in many places: identity proxies in front of SaaS, sidecars on Kubernetes, cloud firewalls in VPCs and access gateways for admin consoles. The job is to keep decisions consistent even when infrastructure is fragmented.
Multi‑Cloud: Why It Complicates Zero Trust
Multi‑cloud adds two hard problems: identity sprawl and network heterogeneity. Every provider has its own IAM flavor, its own API gateways and its own security primitives. You might have fine‑grained roles in AWS IAM, Azure AD groups driving Microsoft 365 access and local accounts lurking in a forgotten GCP project. For segurança zero trust em ambiente multi cloud, you can’t afford 3–4 separate “sources of truth” for who a user is. That’s why a modern Zero Trust strategy usually starts with a central identity and device plane and then “projects” that to each cloud. Think of it as one directory, many adapters. The more you normalize, the easier it gets to express one coherent policy like “Finance analysts can access reports only from managed laptops with disk encryption turned on”.
Zero Trust vs Traditional Perimeter Models
Classic VPN and Firewalls: The Old School Approach
Traditional approaches relied heavily on perimeter firewalls, site‑to‑site VPNs and network‑centric rules. Access control was: “If IP is from our VPN, assume good; if from internet, assume bad.” It works reasonably well in a monolithic data center but fails badly in cloud where workloads move, autoscale and get replaced by managed services. Classic VPNs tend to grant a wide network slice once you’re “in”, so lateral movement is trivial for an attacker. Also, network ACLs can’t easily express conditions like device health or user risk score. In contrast, Zero Trust evaluates each session and often each request; a compromised VPN password doesn’t automatically yield blanket access. That said, VPNs can still play a role as encrypted transport, but not as the primary security control.
Network‑Centric Zero Trust vs Identity‑Centric Zero Trust
Even within Zero Trust, there are different flavors. A network‑centric approach focuses on micro‑segmentation, firewalls, service meshes and traffic policies. It’s closer to “virtual perimeters” around micro‑services. Identity‑centric Zero Trust starts from users, groups, roles and device posture, then applies conditional access everywhere. In multi‑cloud, identity‑centric models usually scale better because you can standardize on SSO and OIDC/SAML even when underlying networks differ wildly. Network‑centric controls still matter, but become enforcement details rather than the primary policy language. A strong design mixes both: identities determine “who can talk to what”, while network segmentation reduces the blast radius if something is misconfigured or compromised at the identity layer.
Architecture of Zero Trust in a Multi‑Cloud World
High‑Level Reference Architecture (Text Diagram)
A typical reference architecture for como implementar zero trust na nuvem across several providers looks like this: [Diagram: Central Identity Provider + Device Management → Policy Engine (risk, context, labels) → PEPs: (1) Cloud Access Proxy for SaaS, (2) API Gateway / WAF in front of apps, (3) Service Mesh sidecars inside clusters, (4) Just‑in‑Time Bastion for admin access]. Underneath, each cloud keeps its native tools—AWS Security Groups, Azure NSGs, GCP VPC Firewall—but they are fed consistent identity attributes and labels. The architecture must also handle telemetry: logs and signals flow back into a central analytics layer that updates risk scores and may trigger step‑up authentication or session revocation when behavior becomes suspicious or device posture degrades.
Control Planes vs Data Planes
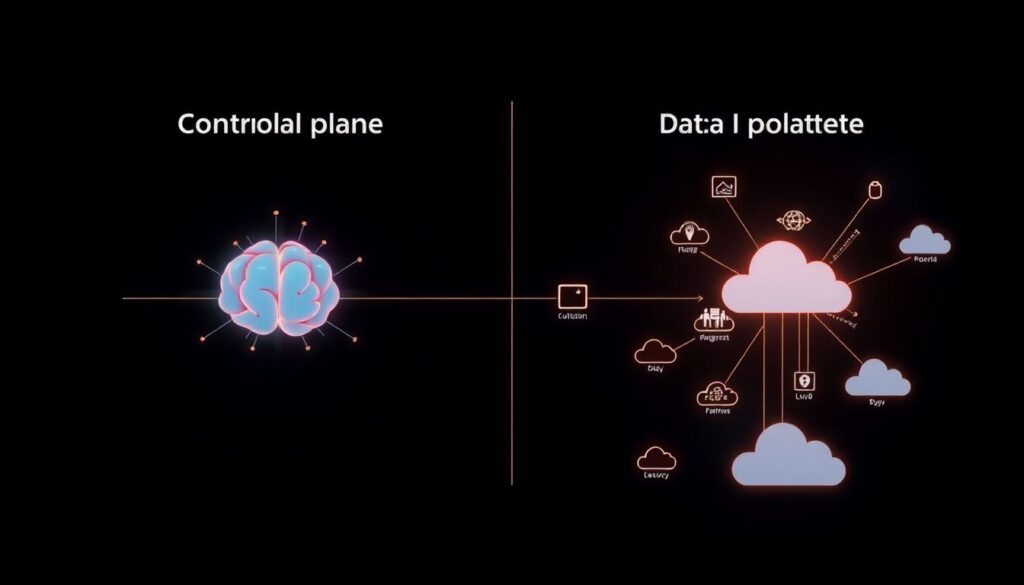
It’s helpful to distinguish the control plane (where you make decisions) from the data plane (where you enforce them). In multi‑cloud Zero Trust, the control plane is ideally unified: one policy engine, one language, one automation pipeline. The data plane is inevitably fragmented: different proxies, agents and gateways embedded in each cloud or on‑prem site. When comparing approaches, platforms that centralize the control plane usually win on consistency and auditability but might require agents or connectors in every environment. Purely cloud‑native approaches that rely only on each provider’s own IAM and networking are lighter and cheaper at first, but policies drift over time and you end up rewriting the same rule N times. The trade‑off is between integration effort today and complexity tax tomorrow.
Identity and Access: The Real Foundation
Central Identity, SSO and Conditional Access
The first practical step in como implementar zero trust na nuvem is consolidating identity: adopt one primary IdP (e.g., Azure AD / Entra, Okta, Ping) and tie as many apps and clouds as possible to it via SSO. Each human and service gets a unique identity; shared accounts are phased out. On top you layer conditional access: rules that say “if user is in Role X and device is compliant and risk score is low, allow; otherwise require MFA or deny.” [Diagram: User → IdP (risk + device check) → Token with claims → App/Gateway]. This beats static VPN whitelists because every login is evaluated in context. Compared to legacy RADIUS or LDAP setups, this approach gives a single place to revoke access, enforce MFA and monitor sign‑ins across your entire multi‑cloud estate.
Just‑in‑Time and Just‑Enough Access
Admin access in multi‑cloud is where many Zero Trust journeys fail; too often, admins sit in “God mode” 24/7. Just‑in‑Time (JIT) access means privileges are granted only when needed and expire automatically. Just‑Enough Access limits what can be done during that window. Instead of a permanent “Cloud Admin” role in AWS or Azure, an engineer requests elevation for a specific task, with an approval workflow and logging. Comparing this to static IAM roles and local root accounts, the JIT model drastically reduces the attack window and makes insider threats easier to detect. Yes, it adds friction, but integrated tools and chat‑based approvals can keep the experience smooth. The gain is that even if a laptop is compromised, dormant over‑privileged tokens won’t be lying around for weeks.
Network and Workload Segmentation in Multi‑Cloud
Micro‑Segmentation vs Macro‑Segmentation
Segmentation comes in two main flavors. Macro‑segmentation splits environments into big islands: prod vs dev, finance vs marketing, EU vs US. This is relatively simple to implement with separate VPCs/VNets and high‑level firewall rules. Micro‑segmentation goes much deeper: every service, pod or VM has tightly scoped rules defining who can talk to it and on which ports. In a multi‑cloud Zero Trust design, you usually start with macro‑segmentation to break up the flat network, then introduce micro‑segmentation in your most sensitive zones and new Kubernetes‑based workloads. Compared to a flat VPN‑backed network, this layered model dramatically reduces lateral movement. The downside is operational complexity, which is why strong automation and good labels for workloads (owner, data type, environment) are non‑negotiable.
Service Mesh, Proxies and Cloud‑Native Firewalls
For east‑west traffic between workloads, service meshes like Istio or Linkerd can enforce mTLS, authorization policies and telemetry without touching each application’s code. [Diagram: Service A → Sidecar → Encrypted Channel → Sidecar → Service B]. For north‑south traffic entering from the internet or from user devices, you rely on reverse proxies, WAFs and cloud load balancers that integrate with your IdP. Cloud‑native firewalls then narrow exposure to only authorized origins or tags. Compared with traditional appliance‑based firewalls, these cloud‑native controls scale better and integrate with labels and identity, but they differ per provider. This is where soluções zero trust para multi cloud help by wrapping those primitives behind a more uniform policy engine so your security engineers don’t need to memorize three different DSLs.
Data, SaaS and Shadow IT
Protecting Data Across Clouds and SaaS
Data rarely stays in one place: S3 buckets, Azure Blob, GCS, SaaS storage, internal DBs. A Zero Trust mindset says “protect data, not only systems”. That means classifying data, tagging resources and applying access based on sensitivity plus business role. Access to a sensitive bucket might require corporate device posture and strong MFA, while a public marketing asset can be open. DLP and CASB‑like capabilities add another filter: they inspect content and user behavior across SaaS, flagging exfiltration attempts. Compared with purely perimeter‑oriented DLP appliances in data centers, cloud‑aware DLP can act at the API and identity layer, independent of the underlying network. That’s crucial in multi‑cloud, where much access to data never goes through your traditional network perimeter at all.
Shadow IT, BYOD and Browser‑Based Access
Employees often adopt SaaS tools without formal approval, and bring‑your‑own‑device has blurred lines even more. A strict VPN‑only model either blocks everything or becomes riddled with exceptions. Zero Trust, by contrast, embraces browser‑based access with strong identity, device checks and isolation where necessary. Remote browser isolation and SASE‑style secure web gateways can force risky apps into sandboxed sessions. Compared with banning everything, this approach acknowledges reality while still enforcing guardrails. The Zero Trust twist is that policies look at the app, the data category and the device state, not only URLs. This way you can allow a contractor to use a niche SaaS from their own laptop, but only in a contained session with download and copy‑paste controls enforced.
Tooling and Platforms: Build, Buy or Mix
Security Platforms vs DIY with Cloud‑Native Tools
Organizations often have to choose between assembling their own Zero Trust stack from cloud‑native pieces or adopting a more integrated plataforma de segurança zero trust na nuvem. DIY means heavier use of AWS IAM, Azure Conditional Access, GCP IAM, security groups, plus open‑source proxies and meshes. It’s flexible and reduces license costs, but you pay in engineering time and cross‑cloud complexity. Integrated platforms—think identity providers plus Zero Trust Network Access (ZTNA), secure web gateways and posture management—offer a single console, unified telemetry and pre‑built connectors. Comparing the two, smaller teams or highly regulated orgs tend to benefit more from a platform; very large tech‑savvy enterprises sometimes prefer DIY to avoid vendor lock‑in. In practice, many land in the middle: a core platform, tuned with cloud‑native add‑ons.
Comparing ZTNA, SASE and Legacy VPN Solutions
Zero Trust Network Access (ZTNA) focuses on application‑level access: users authenticate to a broker, which then connects them to specific apps, not networks. SASE extends this with secure web gateway, CASB/DLP and often SD‑WAN. Legacy VPN simply exposes an IP‑level tunnel. In multi‑cloud, ZTNA/SASE let you publish an internal app hosted anywhere—AWS, on‑prem, GCP—behind the same user experience. From a security perspective, ZTNA enforces per‑app, per‑session context checks; VPN essentially assumes that once you’re on, you’re trusted. On the flip side, VPN is simpler to bootstrap and may be enough in small, homogeneous setups. As your environment gravitates to hybrid and multi‑cloud, though, VPN‑only quickly hits scaling and security limits, making modern Zero Trust access a more sustainable path.
Implementation Roadmap and Common Pitfalls
Phased Rollout: From Quick Wins to Deep Integration
A realistic roadmap for segurança zero trust em ambiente multi cloud avoids “big bang” rewrites. Phase one usually targets identity: central IdP, MFA everywhere, basic conditional access and phasing out standing admin accounts. Phase two addresses remote access: replace or frontload VPN with ZTNA for web apps and SSH/RDP, focusing on high‑risk users and third parties first. Phase three moves deeper into workloads: micro‑segmentation, mTLS, service mesh and automated policy generation from existing traffic patterns. Throughout, automation and infrastructure‑as‑code are your best allies; without them, policy drift will undo your progress. Compared to a one‑shot migration of every rule and firewall, this incremental strategy lets you learn from early rollouts and adjust patterns before touching crown‑jewel systems.
Typical Mistakes When Adopting Zero Trust
Common pitfalls repeat across companies. One is treating Zero Trust as a product you can buy rather than an architecture and operating model; tools help, but design and governance matter more. Another is ignoring developer experience—if policies are opaque and block legitimate work, engineers will find workarounds and the security team earns a bad reputation. Also, many teams underestimate the importance of telemetry: without good logs and analytics, you can’t tune policies or prove value. Finally, some organizations copy‑paste on‑prem access models into the cloud instead of rethinking who really needs what. Compared to traditional perimeter upgrades, Zero Trust demands more collaboration between security, cloud, networking and identity teams, but the payoff is a security posture that actually matches how your business uses cloud today.
Choosing an Approach That Fits Your Reality
Balancing Security, Complexity and User Experience
There is no single “right” answer for como implementar zero trust na nuvem; the best path depends on team skills, regulatory constraints and how chaotic your current multi‑cloud sprawl is. If you already have strong identity governance, leaning into identity‑centric conditional access and ZTNA will feel natural. If your pain is lateral movement between services, investing early in micro‑segmentation and service meshes may deliver bigger wins. When comparing different soluções zero trust para multi cloud, look beyond feature checklists and focus on: how policies are expressed, how well they integrate with your CI/CD and how clearly you can explain them to ops and dev teams. In the end, the most “effective” Zero Trust setup is the one your organization can actually operate and evolve, not the one that looks coolest in a vendor demo.