Context and mindset for cloud incident response automation
Why SOAR and serverless fit cloud-native security
When you move most workloads to public cloud, incident response by hand simply cannot keep up with the volume and speed of events. That is where automação de resposta a incidentes em cloud becomes essential: you want playbooks that react within seconds, not humans clicking in consoles minutes later. SOAR gives you workflow logic, case management and enrichment; serverless gives you cheap, elastic execution right where your logs and workloads already live. Put together, they let security teams encode their real‑world runbooks as code, closing the loop between detection and remediation while keeping humans focused on edge cases and decision points instead of repetitive triage tasks that machines can do reliably and consistently.
Key building blocks you will actually use
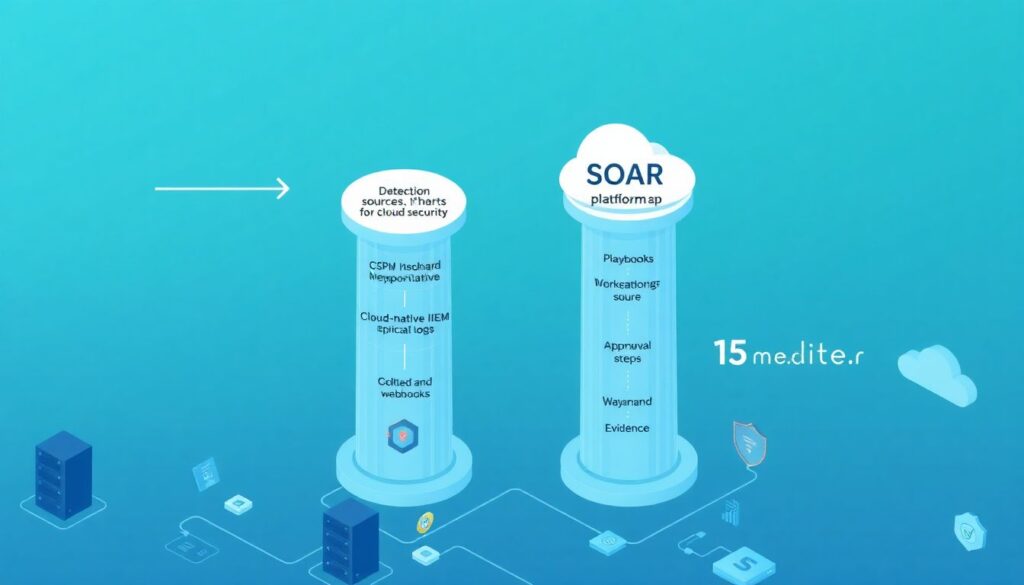
In practice, a modern cloud setup relies on four pillars. First are detection sources: CSPM, cloud-native SIEM, IDS, EDR and application logs firing alerts or webhooks. Second are plataformas SOAR para segurança em nuvem, where you model playbooks, approvals and evidence tracking. Third is the serverless layer, providing scalable functions that talk to cloud APIs to isolate resources, rotate keys or update policies. Fourth is your configuration repository where playbooks and function code live under version control. Thinking in these building blocks helps avoid overengineering: each new use case becomes “new trigger + tweaks to an existing playbook + small function update”, instead of a full bespoke integration or yet another security tool doing its own orchestration in isolation.
Comparing practical approaches to automation
Fully SOAR-centric versus serverless-first workflows
One pragmatic decision is whether your workflows live mainly inside the SOAR platform or mostly in cloud-native functions, with SOAR acting as a coordinator. A SOAR‑centric model is friendlier for analysts: low‑code playbooks, visual branching and integrated ticketing. You offload heavy logic to the SOAR engine and only call cloud functions for specific actions that need credentials or complex logic. A serverless‑first design, by contrast, uses functions as the primary place for business rules and keeps SOAR thin, mostly handling human approvals and case tracking. This works better if your engineering team is strong in code and CI/CD, since you treat response flows as software, reuse modules and test them alongside your application infrastructure.
Cloud-native versus vendor-agnostic tooling
Another comparison is between cloud‑native ferramentas de orquestração e automação de segurança na nuvem, offered by the big providers, and vendor‑agnostic SOAR plus standalone functions. Cloud‑native stacks integrate beautifully with logs, IAM and networking of that specific provider, often giving you lower latency and simpler authentication. However, they can struggle once you have multi‑cloud or large SaaS ecosystems, forcing you into brittle custom connectors. Vendor‑agnostic platforms scale better across heterogeneous environments and usually have mature case management, but sometimes feel clunky when operating deep cloud actions. Many organizations end up hybrid: cloud‑native automation for very low‑level reactions, like quarantine or snapshot, and a central SOAR to correlate alerts, drive approvals and keep a unified audit trail for compliance.
Pros and cons of SOAR and serverless for security
Strengths that matter day to day
SOAR’s biggest practical advantage is consistent execution of playbooks: every phishing alert, suspicious IAM change or anomalous API call gets handled the same way, with all evidence recorded. That drastically reduces “alert roulette”, where different analysts make different choices at 3 a.m. Coupled with funções serverless para segurança e resposta a incidentes, you get almost limitless parallelism: if 500 cloud resources show the same misconfiguration, you can remediate all of them within seconds without queuing manual tasks. Another less obvious benefit is learning: by having every decision point and data source encoded in workflows, new team members ramp up faster and you can perform post‑incident reviews on the automation itself, improving playbooks after each major security event.
Limitations, risks and hidden costs
There are trade‑offs. Over‑automating can create blast radius: a buggy function or misconfigured playbook may revoke access for an entire team or shut down critical workloads. To avoid that, you need guardrails like staged rollouts, canary runs and “simulation mode” where automations log intended actions without enforcing them. Another challenge is maintenance: integrations break when APIs change, and playbooks drift from real processes if nobody owns them. On the financial side, SOAR licensing plus function execution and log ingestion can add up; without good use‑case prioritization, you might automate low‑value events while burning your budget. Finally, cultural resistance can appear: some analysts feel automation threatens their roles, so you must frame it as augmenting humans, not replacing them, and keep humans in the loop for sensitive decisions.
How to implement SOAR with serverless in the cloud
Incremental rollout strategy that actually works
When teams ask como implementar SOAR com serverless na nuvem, the most sustainable answer is: start narrow, iterate hard, and treat everything as code. Begin with one or two high‑volume, low‑complexity scenarios, like automatic enrichment and triage of IAM anomalies or public‑S3‑bucket detections. First, wire the detection source to a serverless function that validates the alert and adds context. Next, push that enriched alert to the SOAR platform, where a playbook opens a case, attaches artifacts and, if confidence is high, calls another function to enforce a safe action such as tagging, snapshotting or isolating resources. Every new iteration should pass through code review, test in non‑prod accounts and include clear rollback paths so that security automations follow your standard engineering quality bar.
Design patterns for reliable playbooks
From an architectural angle, think of your automations as small, composable services. Use serverless functions for idempotent, side‑effect‑controlled actions: “ensure this security group has no public ingress” or “verify this token is revoked”. Let the SOAR layer orchestrate these building blocks, making decisions based on risk scores, user context and business rules. Incorporate approval gates for destructive actions, like terminating instances or rotating production database credentials, with Slack or chat integration to keep latency low. Logging is critical: every function should emit structured logs with correlation IDs that tie back to the SOAR case. Over time, this pattern gives you a catalog of reusable actions that different playbooks can combine, speeding up new automations and making debugging easier when something behaves unexpectedly in production.
Recommendations for choosing tools and scope
Selecting platforms and ownership model
When evaluating plataformas SOAR para segurança em nuvem, focus less on flashy dashboards and more on connector quality, API maturity and how easily you can embed your own code. Check whether the platform supports your cloud provider’s auth patterns, including workload identities, and whether it can call your existing CI/CD pipelines. For the serverless side, align with what your developers already use in production to reuse observability, secrets management and deployment tooling. Organizationally, define clear ownership: usually a small “SecDevOps” group maintains core playbooks and functions, while incident responders propose new use cases and tune thresholds. This prevents a situation where dozens of one‑off automations appear with nobody maintaining them, which quickly turns your security automation landscape into ungoverned technical debt.
Scoping automation and keeping humans relevant
It is tempting to try to automate every alert type, but in practice you get better outcomes by ranking candidates on three axes: volume, standardization and blast radius. High‑volume and highly standardized events with low impact are ideal starting points. For medium‑impact events, use partial automation: enrichment, correlation and suggested actions, leaving the final click to a human. Reserve full manual handling for rare, high‑ambiguity scenarios or novel attack patterns where creativity matters more than speed. Regularly review which playbooks still add value and decommission or refactor ones that no longer match your threat landscape. This approach keeps your automations aligned with risk and ensures analysts spend time on investigation and threat hunting, not just supervising scripts that could safely run on their own.
Trends shaping SOAR and serverless by 2026
More intelligence, less brittle rules
Looking toward 2026, we can expect automação de resposta a incidentes em cloud to become more adaptive and context‑aware. Instead of static thresholds, playbooks will increasingly consume risk engines that learn normal behavior for identities, workloads and APIs, adjusting actions dynamically. For example, the same anomalous login might trigger benign monitoring for a contractor but immediate MFA enforcement and session revocation for a privileged admin account. SOAR engines and serverless functions will also benefit from richer policy‑as‑code ecosystems, where security rules live alongside infrastructure definitions, enabling pre‑deployment checks and auto‑rollback of unsafe changes. As these capabilities mature, the challenge will shift from “can we automate this?” to “how do we govern, audit and explain what the automation just decided to do?”.
Closer integration with cloud-native ecosystems
By 2026, cloud providers are likely to blur the line between SIEM, SOAR and serverless even more, exposing unified event buses, declarative remediation policies and native low‑code builders. That means ferramentas de orquestração e automação de segurança na nuvem will feel less like separate products and more like extensions of the core platform, with automatic discovery of assets and policies. At the same time, multi‑cloud and SaaS sprawl will keep demand high for independent SOAR platforms that can orchestrate across environments. The sweet spot will be combining cloud‑native serverless actions with cross‑domain playbooks, letting you respond consistently whether the incident starts in your Kubernetes cluster, a SaaS CRM or an identity provider. Teams that invest early in clean playbook design and robust serverless practices will be best positioned to exploit these trends.