Por que vale a pena comparar WAFs em cloud agora
When you move serious workloads to the cloud, a Web Application Firewall stops being “nice to have” and quickly becomes mandatory. Instead of racking hardware, you now pick a managed WAF service glued to your cloud provider or to a global CDN. That’s where the confusion starts: which one is the melhor WAF para aplicações em nuvem in *your* scenario, not in a generic benchmark? In this article we’ll walk through how the main options work in practice, what they protect, how much friction they add to your stack, and how the bill tends to behave in real life rather than in marketing slides.
—
Conceitos básicos: o que exatamente é um WAF em nuvem
WAF, layer 7 e o papel na arquitetura moderna
A Web Application Firewall lives at layer 7 (HTTP/HTTPS). Instead of caring about IP packets, it inspects URLs, headers, cookies, JSON bodies and sometimes even session behavior. A serviço de WAF em nuvem custo benefício typically runs as a managed proxy or as an inline filter in front of your app, blocking common attacks like SQL injection, XSS, path traversal, credential stuffing and some bot traffic.
The key mindset shift versus a classic network firewall is this: a WAF understands *application* semantics. You write rules like “block POST to /login after 5 failed tries per minute per IP” instead of “block TCP port 80 from this CIDR”. Because of that, WAF para aplicações web em cloud empresariais normally sits as the first HTTP hop, often integrated tightly with load balancers, API gateways or CDNs.
—
Diagrama mental: onde o WAF entra no fluxo
Imagine a very simple request path:
Client
↓
Anycast / DNS
↓
WAF / CDN Edge
↓
Cloud Load Balancer
↓
App Servers / Containers / Functions
↓
Database / Services
In text-diagram form:
– Client → DNS → WAF/Edge → Load Balancer → App → DB
The WAF in cloud is the “bouncer” at the door of the club. It checks IDs (headers, tokens), watches for suspicious behavior, and may block or rate-limit before the request can even reach your containers or serverless functions.
—
Tipos de WAF em cloud: gerenciado vs. “faça você mesmo”
WAF gerenciado para AWS Azure e Google Cloud
In cloud environments you typically see three patterns:
– Provider-native managed WAFs
AWS WAF, Azure Web Application Firewall (on Application Gateway or Front Door), and Google Cloud Armor. These integrate intimately with the respective load balancers and IAM models. They are the classic WAF gerenciado para AWS Azure e Google Cloud, ideal when you don’t want to manage separate vendors or routing layers.
– Third-party WAFs/CDNs
Cloudflare, Fastly, Akamai and some security-focused vendors. They sit in front of *any* cloud (or even on‑prem) using DNS CNAME or BGP routes. Great when you are multicloud or when you want more edge features (e.g., global CDN, Workers/Functions at the edge, sophisticated bot management).
– Self-hosted or open source WAFs
ModSecurity/OWASP CRS in Nginx/Apache/Envoy, or commercial appliances in VM form. More flexible but you are responsible for capacity planning, patching and tuning. Feels less like “cloud native” and more like running traditional infra inside cloud VMs.
In practice, most teams that want simplicity plus good coverage end up choosing either a native managed WAF from their main provider or a big CDN-based WAF, and reserve self-hosted options for highly custom or regulated environments.
—
Critérios práticos para escolher WAF em cloud
O que realmente importa no dia a dia
When you evaluate the melhor WAF para aplicações em nuvem for your team, focus on how it behaves in production, not on the sheer size of the feature brochure. For day‑to‑day operations, the criteria that most frequently matter are:
– Accuracy of rules (false positives vs. false negatives)
– Latency overhead added by inspection and by the extra network hop
– Ease of tuning rule sets and building exceptions
– Integration with your CI/CD and IaC
– Observability and incident workflows
– And, of course, WAF em cloud comparação de preços for your specific traffic profile
—
Diagrama simples de decisão
Think of a pyramid of priorities:
Top (narrow):
– Security quality (coverage, rule updates)
Middle:
– Operability (tuning, automation, visibility)
Base (wide):
– Cost vs. traffic profile
If the base layer (cost vs. scale) is wrong, you won’t keep the WAF enabled. If the top layer fails (weak rules), you have a false sense of safety. A good choice balances all three for your application stage (MVP, scale‑up, or mature enterprise).
—
AWS WAF: forte integração com o ecossistema AWS
Recursos e modelo operacional
AWS WAF is tightly integrated with ALB, API Gateway, CloudFront and AWS AppSync. You define WebACLs and associate them with these resources. AWS provides Managed Rule Groups, including AWS Managed Rules and AWS Marketplace partner rules, updated automatically as new threats emerge.
In real usage, the biggest plus is how naturally it fits into CloudFormation, CDK and Terraform workflows. You can version-control rule definitions, attach them to new environments automatically and share common WebACLs across regions. For teams already deep into AWS, this decreases friction significantly, especially when onboarding multiple microservices.
—
Desempenho, observabilidade e custo
Performance‑wise, AWS WAF is usually limited more by the linked service (CloudFront or ALB) than by the WAF logic itself. For edge deployments with CloudFront, the latency overhead is typically modest and geographically distributed. Logs are shipped to Kinesis Firehose or CloudWatch Logs, which makes integration with existing monitoring stacks straightforward, though sometimes verbose and a bit costly at scale.
From a WAF em cloud comparação de preços perspective, AWS WAF charges per WebACL, per rule, and per million requests inspected. If you have many small services, rule and ACL counts can creep up; for fewer high‑traffic apps, request‑based pricing dominates. For predictable workloads and tight AWS lock‑in, it often yields a decent serviço de WAF em nuvem custo benefício, especially when you use managed rule groups instead of building everything from scratch.
—
Azure Web Application Firewall: foco em empresas Microsoft
Application Gateway vs. Front Door
Azure has two main WAF flavors: WAF on Application Gateway (regional, closer to your VMs/AKS) and WAF on Front Door (global edge, similar to CloudFront). Both rely heavily on OWASP ModSecurity rule sets plus Microsoft’s managed rules. For Microsoft‑centric shops (Active Directory, .NET, Windows servers), the integration into Azure Portal, Resource Manager templates and Azure Policy feels natural.
The regional WAF on Application Gateway gives more traditional “inside the VNet” vibes, whereas Front Door WAF plays the role of global reverse proxy, combining CDN, routing and protection. This choice affects not just security but also the network architecture: where TLS terminates, whether you use private links, and how you handle multi‑region failover.
—
Prática, alertas e experiência operacional
In practice, Azure WAF often requires an initial tuning phase because the default OWASP rules can be noisy for complex legacy applications. You’ll likely start in detection mode, observe hits, create custom exceptions per path or parameter, and progressively switch to prevention mode.
Operationally, logging to Log Analytics and using Azure Monitor alerts enables reasonably fast incident triage, but teams often need to invest a bit of time in Kusto queries and dashboards. When used primarily for critical line‑of‑business apps rather than huge public websites, many companies find the cost acceptable, gaining a convenient WAF para aplicações web em cloud empresariais that fits well into their existing Azure governance model.
—
Google Cloud Armor: proteção orientada a edge e APIs
Features de segurança e integração com GCP
Google Cloud Armor is Google’s managed WAF and DDoS protection service, typically fronting HTTP(S) load balancers. It shines in scenarios where you heavily use GKE, Cloud Run or serverless APIs exposed via global load balancers. Policies support preconfigured WAF rules (again OWASP‑inspired), Geo/IP restrictions, rate‑based rules and custom expressions using the CEL (Common Expression Language).
A practical advantage is how well Cloud Armor leverages Google’s global network and load balancer stack, giving you unified policies across regions. If you are already comfortable managing IAM, labels and backends in GCP, adding WAF policies feels like an extension of the same mental model rather than a bolt‑on security box.
—
Performance, logging e custos
Because Cloud Armor is embedded in the Google Cloud global HTTP(S) load balancer, performance is typically consistent and can handle large traffic bursts. Latency overhead tends to be small, but as always, you should test it in your main regions and with realistic traffic patterns. Logging goes to Cloud Logging and can be piped into BigQuery or Pub/Sub for deeper analytics or SIEM integration.
On the pricing side, you pay for policy/ rule configuration and for requests evaluated. For API‑heavy scenarios, especially with spiky workloads, scaling behavior is usually more important than raw price per million requests. Many teams appreciate that you can start with a relatively small footprint and grow, keeping Cloud Armor as a central WAF gerenciado para AWS Azure e Google Cloud–style component for your GCP estate.
—
Cloudflare WAF: multicloud, CDN e recursos avançados
Recursos e casos de uso práticos
Cloudflare’s WAF sits on top of its global CDN and reverse‑proxy network. You point your DNS records (CNAME or NS) to Cloudflare, and it becomes your public edge. Its WAF engine combines managed rules, custom rules, bot management, rate limiting, API discovery and sometimes L7 DDoS mitigation, all at the same control plane.
For teams running across several providers, Cloudflare is often the de facto melhor WAF para aplicações em nuvem when the key requirement is multicloud protection and consistent security policy. You can front AWS, Azure, Google Cloud and on‑prem apps with similar WAF rules and leverage caching and performance optimizations at the same time.
—
Operação, tunning e custo benefício real
In operation, Cloudflare’s dashboard is probably one of the easiest for security and dev teams to explore, with good filtering, quick deployment of rules and plenty of analytics. APIs and Terraform support are strong, which helps when you want to “codify” everything. That said, the more advanced features (e.g., premium bot management, advanced rules) live in higher‑tier plans, and these can become significant line items for very large traffic volumes.
From a serviço de WAF em nuvem custo benefício standpoint, mid‑size companies often get an excellent deal by combining CDN savings (offloading origin traffic) with strong WAF protection. Very small projects can even start on cheaper plans, and huge enterprises negotiate tailored contracts. Because pricing is plan‑based plus usage, it’s worth modeling different scenarios if you serve a lot of static content or video through Cloudflare as well.
—
Outros WAFs e comparação com alternativas “faça você mesmo”
Fastly, Akamai e soluções self‑hosted
Fastly and Akamai follow a similar model to Cloudflare: global edge, strong CDN, and increasingly capable WAFs with good rule tuning and API security features. They tend to be popular with media, e‑commerce and large SaaS platforms that care deeply about performance and global footprint.
On the other side of the spectrum, you have ModSecurity/Nginx or Envoy‑based WAFs running on your own clusters. The main advantage is radical flexibility: you can write custom Lua, WASM or filter logic and plug it tightly into your service mesh. However, you now have to manage scaling, upgrades and incident response fully on your own. Compared to fully managed vendors, that often means more ops toil and a steeper learning curve, unless you already run a strong platform engineering team.
—
Quando um WAF “caseiro” ainda faz sentido
A DIY approach can still be the right call in certain conditions:
– Ultra‑regulated environments where data locality and vendor risk dominate
– Highly specialized protocols or legacy apps that managed WAFs mishandle
– Situations where you already maintain a robust reverse‑proxy/mesh stack and want to reuse it
But for the majority of organizations just trying to protect standard HTTP/HTTPS apps, a WAF gerenciado para AWS Azure e Google Cloud or a CDN‑centric solution will be more straightforward and less error‑prone than maintaining a custom ModSecurity farm.
—
Comparando recursos, desempenho e custos na prática
O que olhar além da lista de features
Instead of counting how many checkboxes each vendor offers, focus on how each tool behaves for your workloads. You want to know:
– How easy it is to move from “monitor” (log‑only) to true blocking mode
– Whether your team can express business rules cleanly (e.g., protect a specific login or checkout flow)
– How quickly you can react when a false positive hits production and blocks customers
These day‑to‑day questions usually matter more than exotic features you will rarely use. A “good enough” set of managed rules that is actively updated and a clear tuning path often beats a monster feature set that no one on your team really understands.
—
Mentalidade de custo benefício por estágio de maturidade
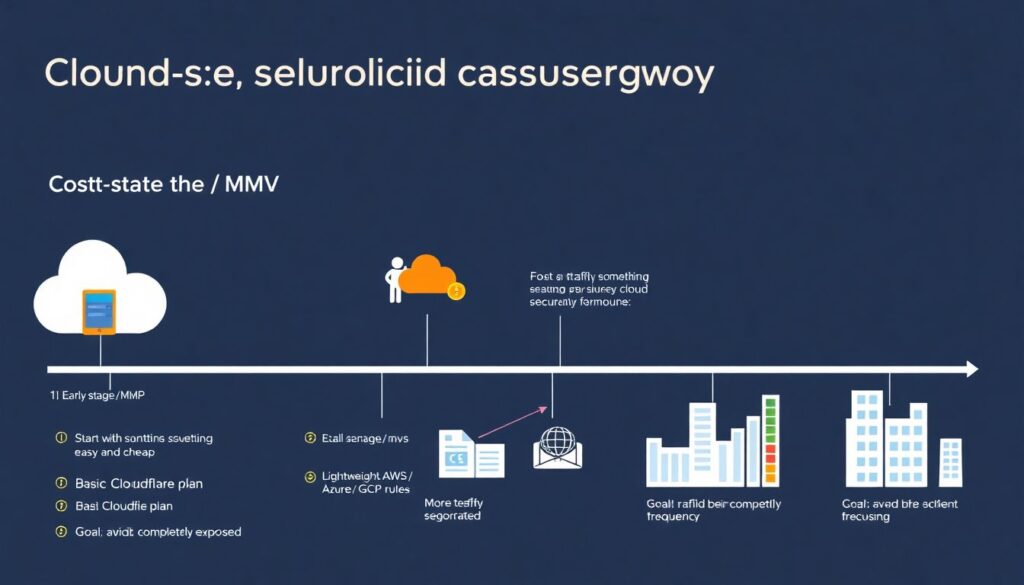
Cost-benefit changes along your cloud journey:
– Early stage / MVP: Start with something easy and cheap (basic Cloudflare plan, lightweight AWS/Azure/GCP WAF rules) just to avoid being completely exposed.
– Growth / scale‑up: As traffic grows and incidents become more frequent, invest in better tuning, custom rules, maybe upgrade to stronger plans or add dedicated security engineers.
– Enterprise: Focus on consistent policies across regions and clouds, strict compliance, deep observability and integration with SOC workflows and SIEM, even if that means paying more per request.
In all stages, think of WAF em cloud comparação de preços not as a simple “who is cheapest per million requests” exercise, but as a trade‑off between reduced incident impact, dev productivity and long‑term maintainability.
—
Dicas práticas para implementar um WAF em cloud sem dor
Estratégia de rollout seguro
A practical, low‑drama rollout typically follows these steps:
– Start in detection mode only, with managed rules enabled
– Observe logs for a few days or weeks, find noisy rules and typical false positives
– Add exceptions for specific endpoints/parameters that are legitimately “weird”
– Switch to blocking incrementally, starting with low‑risk paths or lower severity rules
This phased approach drastically reduces the chance that your first deployment of a WAF para aplicações web em cloud empresariais will suddenly block payments or logins in production.
—
Boas práticas de operação contínua
Once you’re live, keep these habits:
– Integrate WAF rule definitions into IaC (Terraform, CloudFormation, ARM, etc.)
– Feed WAF logs into a central observability stack and define actionable alerts
– Review hit statistics regularly with both dev and security teams, not in isolation
– Re‑evaluate rule sets when you release major application features or new APIs
By treating WAF as part of your deployment pipeline rather than as a separate “security island”, you get more predictable behavior and quicker recovery when something goes wrong.
—
Conclusão: escolhendo o WAF certo para o seu cenário
There isn’t a single universal melhor WAF para aplicações em nuvem. If you’re mostly on one cloud and want minimal friction, a native WAF gerenciado para AWS Azure e Google Cloud will probably be the most natural choice. If you are multicloud, heavily internet‑facing and care a lot about edge performance, Cloudflare, Fastly or Akamai may be a better fit. If you have highly specialized constraints, a self‑hosted stack might still make sense.
What really defines the serviço de WAF em nuvem custo benefício in your context is not only the price per million requests, but how much protection, stability and operational simplicity you gain per hour of engineering effort. Pick something you can actually operate, start small, tune it, and evolve the setup as your traffic and threat model grow. That pragmatic, iterative approach will usually serve you better than any one‑size‑fits‑all recommendation.
