If you’re moving fast with serverless functions and microservices in the cloud, your APIs have quietly become your new perimeter. The bad news: attackers noticed that before many engineering teams did. From 2023 to 2024, multiple industry reports (Verizon DBIR, Akamai, Salt Security) converged on one uncomfortable trend: API‑related issues show up in well over half of web application incidents, and the share has grown a few percentage points each year. Exact values differ per study, but the direction is crystal clear: as we modernize architectures, we also concentrate risk on APIs that are often badly inventoried, inconsistently authenticated and over‑permissive by design.
What “serverless”, “microservices” and “API security” really mean
Let’s sync on terms before diving into controls. Microservices are small, independently deployable services that each own a specific capability — think “payments”, “catalog”, “recommendations”. Serverless typically means functions‑as‑a‑service (FaaS) like AWS Lambda, Azure Functions or Google Cloud Functions, where you deploy code and the platform hides the servers. In both cases, components talk mainly via APIs: HTTP/REST, gRPC, event payloads or message queues. API security, in this context, is not just TLS and a token; it’s the discipline of ensuring only the right identities call the right operations with the right data, that calls are observable, rate‑limited, validated and resilient against abuse, and that secrets, configs and data flows are properly governed across the whole topology.
Why cloud‑hosted APIs became the primary attack surface
A big shift over the last three years is simple: traffic moved. Between 2023 and 2025, CDN and WAF vendors consistently reported that API calls represented 60–80% of all HTTP traffic they saw, growing a few percent year over year. I don’t have 2025 final numbers yet, but early 2024 data already showed APIs surpassing traditional web pages in volume by a wide margin. Attackers go where the traffic and the data are, which is why segurança de apis em nuvem shows up as a dedicated chapter in recent guidance from OWASP, NIST and several cloud providers. Instead of SQL injection against a monolith’s login form, you now see automated abuse of “internal‑only” endpoints that accidentally got exposed, or token replay against poorly scoped OAuth clients tying together dozens of microservices.
Textual diagram: from monolith to microservices and serverless
Imagine two diagrams side by side. On the left, a classic monolith:
[Diagram A: A single “Web App” box connected to “DB” and “Users”. A WAF sits in front. The threat arrows from the Internet mostly hit one external URL surface.] On the right, a cloud‑native system:
[Diagram B: Many small boxes labeled “User‑Service”, “Order‑Service”, “Billing‑Service”, plus several “Lambda Functions”. An API Gateway and an event bus sit in the middle. Arrows from “Mobile App”, “Partner App” and “Admin Portal” hit the gateway, then fan out to dozens of internal APIs.] In Diagram B, every box has an HTTP or event interface, and each arrow is a potential attack path. You didn’t eliminate complexity by adopting microservices; you redistributed it into the network. That redistribution is why naïve lift‑and‑shift of old security models fails.
How this changes the definition of “perimeter”
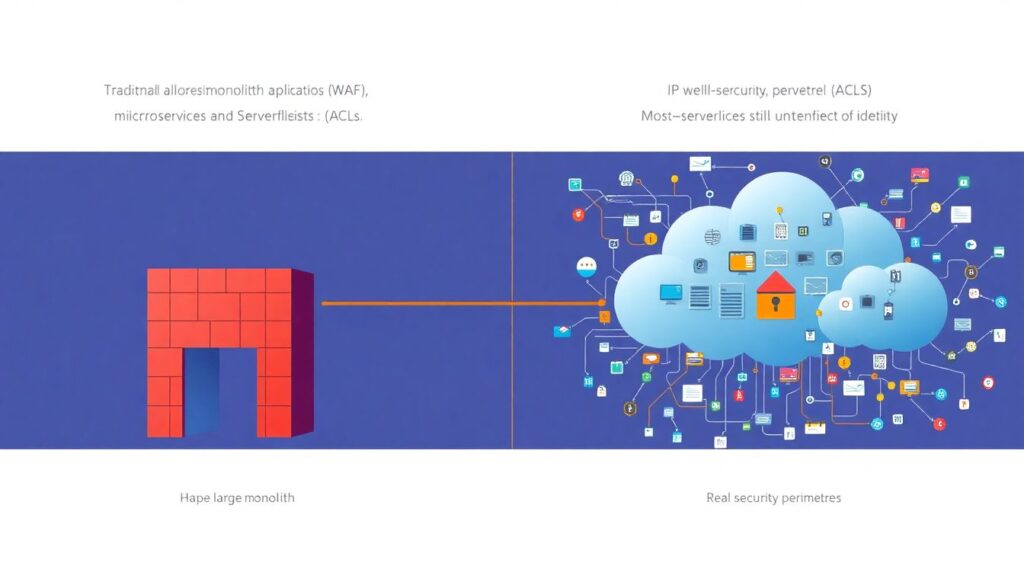
In the monolith world, you could put a sturdy WAF and some IP‑based ACLs in front of a few endpoints and call it a day. With microservices and serverless, most traffic is east‑west inside your cloud. You still need the north‑south gateway, but it’s absolutely not enough. The real perimeter becomes identity and authorization — which workload called which API, which user or machine identity is behind it, and under which policy. That’s why modern architectures lean on mTLS between services, short‑lived tokens, and centralized policy engines, instead of just network zones. Think of it less like a fence around a building and more like badge readers on every door and detailed logs of who opened what and when.
Core pillars of API security in serverless and microservices
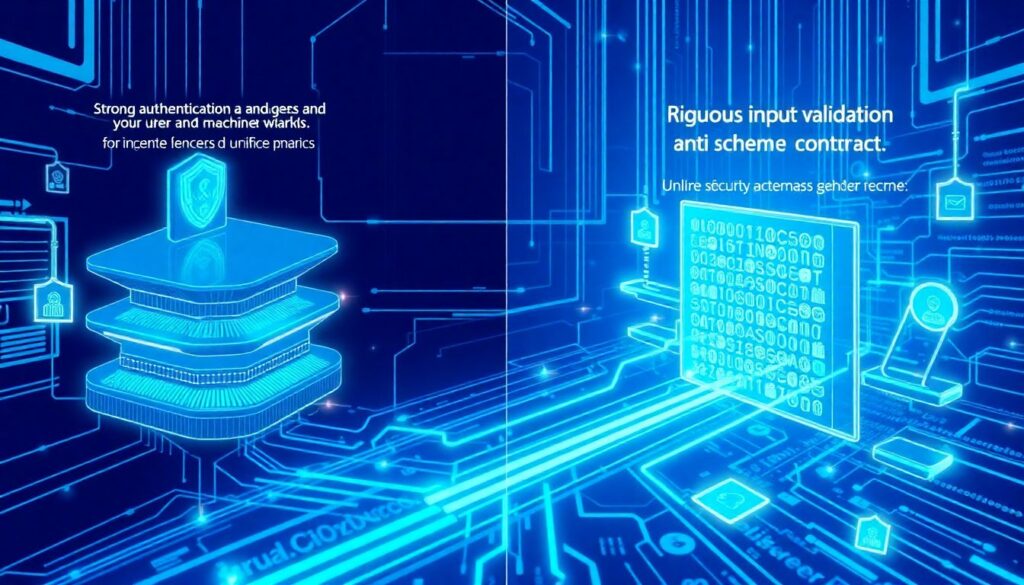
If we strip marketing down to fundamentals, four pillars keep showing up. First, strong authentication and granular authorization — not only for end users but also for workloads. Second, rigorous input validation and schema enforcement so that the only traffic allowed is exactly what your contracts say. Third, observability and anomaly detection: rich, structured logs, traces and metrics correlated per identity and API operation. Fourth, lifecycle governance: you discover, classify, version and retire APIs intentionally instead of letting them multiply unchecked. Over the last three years, the organizations that fared best in breach reports weren’t those with the fanciest tools, but those that operationalized these pillars consistently across teams and environments.
Comparing traditional web app security with API‑centric security
Traditional app security practices still matter, but they shift focus. Classic WAF rules target patterns in HTML forms, URLs and query strings. In API‑first systems, the attack comes in JSON bodies, deeply nested objects, or subtle abuse of “legitimate” flows such as mass enumeration through verbose search endpoints. Instead of inspecting raw text for signatures, you start validating against OpenAPI or gRPC definitions. Instead of static roles like “admin/user”, you move to attribute‑based access control that considers tenant, resource ownership and context. The main difference is that the unit of control is the API operation itself, with its input and output contracts, not an entire “page” or “screen”.
Serverless specifics: short‑lived compute, long‑lived risk
Serverless functions give you fantastic elasticity and operational simplicity, but they also complicate security reasoning. A function may live for milliseconds, yet its permissions against data stores and other APIs are typically very broad and long‑lived via IAM roles or service principals. Over the 2023–2024 period, multiple AWS and Azure post‑mortems showed the same pattern: a misconfigured function with wild‑card permissions gets compromised through an injection bug, then used as a pivot into internal APIs and data lakes. That’s why soluções de segurança para serverless na aws emphasize least‑privilege IAM roles per function, environment‑specific config, strict event validation and consistent secrets management, not just code scanning.
API gateways and service meshes as enforcement points
Architecturally, you need choke points where you can consistently apply security logic. In cloud‑native setups, the first such choke point is an API gateway at the edge; the second is a service mesh in the cluster or VPC. The gateway handles external concerns: authentication with OAuth2/OIDC, global rate limiting, header normalization, coarse routing. The mesh focuses on internal traffic: mTLS between services, fine‑grained traffic policies, retries and circuit breaking. Done right, this duo becomes your de‑facto plataforma de proteção de apis na nuvem, because they see every call, can enrich it with identity context, and can emit uniform telemetry that security teams actually manage to consume at scale.
Tools vs. practices: what really moves the needle
Vendors love to pitch ferramentas de segurança para microserviços as if they were silver bullets: API discovery with fancy graphs, anomaly detection powered by machine learning, policy‑as‑code frameworks, and more. They all have value, but empirical data from 2023–2024 audits shows something more mundane: teams that enforced basic hygiene — complete API inventory, authenticated by default, no unauthenticated admin endpoints, input validation tied to schemas, and automated tests for broken access control — saw far fewer critical findings than those with expensive tools but chaotic processes. Use tools to amplify good practices, not to replace architecture and discipline you haven’t built yet.
Managed security services in the cloud
Most teams don’t have enough in‑house specialists to keep up with the pace of change. That’s where serviços gerenciados de segurança para microserviços e apis come in: cloud‑native WAFs, managed API gateways, cloud provider security hubs, and third‑party SOCs that specialize in API abuse patterns. Over the last three years, adoption of managed runtime protection and continuous posture management roughly doubled among large enterprises, according to public cloud earnings calls and analyst notes. The trade‑off is obvious: you gain operational coverage faster, but you must invest time into tuning, integrating and reviewing their alerts so they fit your architecture instead of drowning you in noise.
Data from the last three years: what changed in practice
Let’s condense the numbers. From 2023 through late 2024, API‑related issues (broken access control, exposed endpoints, missing auth, excessive data exposure) consistently appeared in the top three root causes of web application breaches across several major reports. Many studies put them in the 30–50% range of app‑layer incidents, with a noticeable uptick year over year as more workloads moved to microservices and serverless. While I don’t have final 2025 statistics as of my knowledge cutoff, analysts were already projecting that API‑centric attacks would continue to climb, simply because the underlying driver — rapidly growing API surface area — hasn’t slowed down. Unless teams change how they design and operate APIs, that projection is unlikely to be wrong.
Putting it all together
To secure modern cloud‑native systems, you’re essentially trying to make a complex graph of services behave like a well‑governed single system. That means giving every API a clear owner, contract and policy; letting identity rather than IP define who can talk to whom; centralizing enforcement in gateways and meshes; and feeding rich telemetry into security operations that can spot abuse before it becomes a headline. If you combine those architectural moves with careful use of cloud‑native controls and selectively chosen security tooling, segurança de apis em nuvem stops being a reactive firefight and starts looking like an engineering problem you can reason about, iterate on and steadily improve.