Context: why federated identity got so hard
Hybrid and multi‑cloud blew up the old idea that “everything is on one AD domain behind a VPN”. Today the same user jumps between on‑prem apps, Azure, AWS, SaaS, Kubernetes clusters and mobile APIs. Each stack ships its own login model, token format and session rules. Without a coherent layer of gerenciamento de identidades federadas, you end up with duplicated accounts, inconsistent roles and messy access reviews. The good news: SSO, SAML and OIDC form a workable toolbox, as long as you treat identity like a shared platform, not a side feature of each product.
Core concepts: SSO, IdP, federation in a nutshell
Single sign‑on means a user authenticates once against a trusted service and reuses that identity across multiple applications, without re‑entering credentials. Federation is the agreement between domains to accept each other’s identities using standard protocols. The identity provider (IdP) issues tokens; service providers or relying parties consume them. In practice, gerenciamento de identidades federadas aligns IdPs, directories, MFA, token lifetimes and attribute mapping so that “who you are” and “what you can do” stay consistent across clouds and datacenters.
Standards: SAML vs OIDC vs OAuth2
SAML is XML‑based, designed for browser SSO in enterprise scenarios, and still dominates legacy SaaS integrations. OpenID Connect (OIDC) rides on top of OAuth2 using JSON and JWT, and fits modern APIs, SPAs and mobile apps. OAuth2 alone covers authorization delegation, not authentication, which is why “login with X” flows should be OIDC, not bare OAuth. In hybrid environments, both SAML and OIDC will coexist for a long time; robust gateways and identity brokers become crucial to bridge protocols and normalize claims across providers.
Text diagram: basic SSO federation flow
Imagine the simplest web SSO pattern:
[Diagram: 1) User accesses app.example.com (Service Provider). 2) App redirects to idp.corp.com with a SAML/OIDC request. 3) IdP authenticates the user with password + MFA, then issues a signed token. 4) Browser posts or redirects that token back to the app. 5) App validates the signature, checks audience and expiry, builds a session and enforces authorization. 6) For another app, steps 1–2–5 repeat without re‑auth, reusing the existing IdP session to avoid constant password prompts.]
Why hybrid and multi‑cloud complicate identity
In a single cloud, you can often lean on a native IdP and uniform policies. Hybrid and multi‑cloud fracture that simplicity: on‑prem AD, Azure AD, AWS IAM, GCP IAM, plus dozens of SaaS vendors. Each has its own roles, groups and policies that rarely align. A solução de single sign-on SSO para ambiente híbrido e multi-cloud precisa orquestrar these silos, often via an authoritative corporate IdP that federates outward and a set of connectors that synchronize attributes, groups and lifecycle states to every target platform in near real time.
Key building blocks of a federated identity architecture
The foundational layer is your corporate directory (often AD or LDAP), serving as the source of truth for people, service accounts and basic group membership. On top of that, an IdP or broader plataforma IAM com suporte a SSO SAML OIDC para nuvem híbrida provides authentication, MFA, conditional access and token issuance. Then come connectors for HR systems, cloud directories and SaaS apps. Finally, governance components handle approvals, recertifications and audit. Skip one of these and you get either fragile integrations or uncontrolled access sprawl.
IdP as the “identity control plane”
Experts increasingly describe the IdP as an “identity control plane” for the enterprise. It terminates all user authentication, enforces MFA and risk checks, and then emits standards‑based tokens to everything else. This approach is more sustainable than hard‑coding LDAP or database logins into each app. Tools like Azure AD, Okta, Keycloak or similar can play this role, but they must be configured to issue consistent claims (emails, roles, groups) across SAML and OIDC, and to support both modern OAuth‑based APIs and older web SSO patterns cleanly.
Architectural diagram: hybrid / multi-cloud
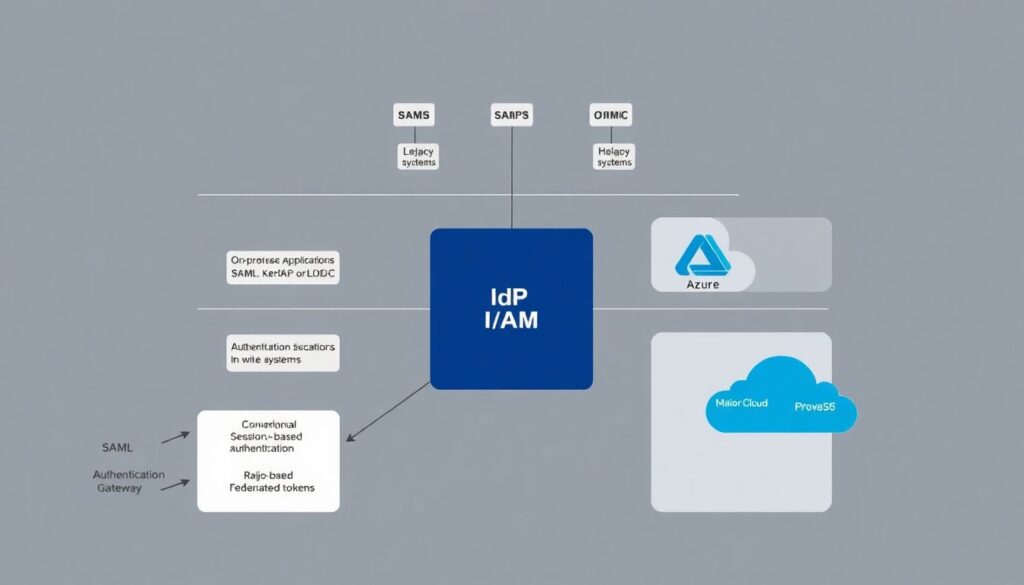
[Diagram: At the center sits Corporate IdP/IAM. Upwards: connections to SaaS apps via SAML and OIDC. To the left: on‑prem apps and legacy systems using SAML, Kerberos or LDAP, fronted by a gateway that converts session or header auth into federated tokens. To the right: cloud providers (Azure, AWS, GCP) trusting the central IdP for workforce login. Downwards: HR system feeding joiner‑mover‑leaver events into IAM. Around everything: logging, SIEM and identity governance, consuming events and producing alerts and certifications.]
Comparing SAML and OIDC in practical deployments
From a day‑to‑day operations perspective, SAML offers mature support in many enterprise SaaS products, including extensive admin UIs, attribute mapping wizards and documentation. However, SAML is verbose, harder to debug by hand and cumbersome for native apps or SPAs. OIDC is far more developer‑friendly, uses compact JWT tokens and aligns with API gateways, microservices and mobile SDKs. When architects design new services, they should prefer OIDC; SAML remains the pragmatic choice for integrating existing vendors that do not yet support modern OAuth2‑based flows.
When to standardize, when to tolerate diversity
In real hybrid environments, you won’t eliminate protocol diversity overnight. The goal is to standardize where you control the stack—internal APIs, greenfield projects, new SaaS purchases—while tolerating SAML for legacy and third‑party constraints. Many ferramentas de gerenciamento de identidades federadas SAML OIDC para empresas act as protocol brokers, translating SAML assertions into OIDC tokens or vice versa, so apps and clouds don’t need to understand every legacy detail. Centralizing that complexity helps security teams audit flows and rotate keys more easily.
Security fundamentals: MFA, tokens, and session control
Federated identity concentrates risk: compromise the IdP account, and you potentially compromise dozens of apps at once. That is why strong MFA, phishing‑resistant methods (FIDO2, WebAuthn, smartcards) and conditional access policies are non‑negotiable. Token security matters as much as passwords: set reasonable expirations, validate audiences, check signatures using known keys, and store refresh tokens securely. In multi‑cloud setups, ensure every relying party actually validates tokens against the correct issuer to avoid accepting forged or replayed credentials from untrusted endpoints.
Access governance in a federated world
Once you decouple authentication using SSO, you still need a strategy for authorization and governance. Relying exclusively on local app roles breaks consistency and complicates audits. Mature designs centralize entitlements using groups, attributes or roles from the IAM platform. Workflow engines handle approvals, while periodic recertifications force business owners to re‑validate who needs which access. A serviço gerenciado de identidade e acesso federado multi-cloud should also publish logs and entitlement inventories so risk teams can correlate identity changes with security events.
Expert recommendations for designing your SSO strategy
Experienced architects suggest starting with a clear identity authority model: pick one primary IdP for workforce identities and avoid proliferating independent login silos. Map every major app and cloud to that authority, even if it means using federation chaining for some providers. Define three to five standard access patterns—web SSO, API access, machine‑to‑machine, privileged admin—and design repeatable blueprints. Document token lifetimes, MFA rules, and required claims for each pattern, so developers and cloud engineers stop improvising authentication on a per‑project basis.
Protocol and token strategy: what experts actually do
Practitioners often standardize on OIDC + OAuth2 for new apps and APIs, using SAML only where vendors require it. They adopt a single signing key per environment (dev, test, prod) with automated rotation and well‑defined issuer URLs. JWT access tokens are kept short‑lived; refresh tokens live longer but are tightly guarded and revocable. Admin and CI/CD pipelines often use client credentials or workload identity, never shared passwords. This discipline keeps the gerenciamento de identidades federadas manageable instead of a patchwork of incompatible token formats.
Role of consulting and external expertise
For complex organizations, bringing in consultoria em implementação de SSO e federation (SAML OIDC) em ambientes híbridos can save months of trial and error. External experts help untangle political ownership, define future‑state diagrams, and choose where to place federation boundaries between business units or subsidiaries. They also spot subtle pitfalls, like misaligned NameID formats, unsanitized attributes, or token bloat that breaks older proxies. The best consultants leave behind reference architectures, pattern libraries and runbooks, rather than just one‑off configurations nobody fully understands.
IAM platforms and tooling in hybrid / multi-cloud
A robust plataforma IAM com suporte a SSO SAML OIDC para nuvem híbrida should integrate with your HR system, main directory and every critical cloud provider. Key features include SCIM or similar for account provisioning, adaptive MFA, step‑up authentication for sensitive actions, and policy‑based access control. Look for identity brokering capabilities so the platform can expose one consistent OIDC endpoint to internal apps, while federating behind the scenes to Azure AD, social providers or partners. Logging and API‑level management are essential for automation and auditability.
Choosing tools: practical selection criteria
When evaluating ferramentas de gerenciamento de identidades federadas SAML OIDC para empresas, prioritize standards conformance, automation APIs and vendor ecosystem over shiny dashboards. Ask vendors to demonstrate protocol traces, key rotation workflows, failover across regions, and integration with your SIEM. Validate how they handle multi‑forest AD, multiple Azure tenants or multi‑account AWS organizations. Test complex edge cases: nested groups, large JWTs, non‑ASCII identities, and conditional access tied to device posture. Tools that collapse under these real‑world patterns will cause pain in production later.
Operational best practices for day‑two success
Once the initial SSO rollout is done, the real work begins. Treat your IdP and federation components like any other critical infrastructure: high‑availability clusters, tested disaster recovery, versioned configuration as code and regular security reviews. Establish runbooks for certificate expiry, metadata changes and app onboarding. Encourage developers to use standard SDKs for SAML or OIDC rather than custom parsing. Maintain a catalog of all relying parties, their contact owners and security requirements, so changes in token format or claims can be coordinated without last‑minute emergencies.
Logging, monitoring and incident response

Federated identity produces a rich stream of logs: successful and failed logins, MFA prompts, token issues, consent grants and provisioning events. Centralize these into a SIEM and build specific alerts, such as impossible travel, abnormal client types, or sudden spikes in failed SSO attempts for a high‑value app. When an incident hits, the ability to trace which tokens were issued, from which IPs, to which apps, is invaluable. Integrate revocation and emergency access removal into your incident response playbooks, with rehearsed drills across security and operations teams.
Future trends: beyond classic SSO
The industry is steadily moving toward passwordless, continuous and context‑aware access. Device posture, network signals and user behavioral analytics increasingly factor into federated authentication decisions. Workload and machine identities are also converging into the same IAM platforms as human identities. Your gerenciamento de identidades federadas strategy should anticipate more dynamic grants, short‑lived credentials and just‑in‑time access, rather than static, long‑lived roles. Designing now for flexible, standards‑based SSO and federation across hybrid and multi‑cloud environments will make that evolution far less disruptive later.