Why Continuous Cloud Security Posture Monitoring Matters
Continuous cloud security posture monitoring sounds like marketing jargon, but in practice it’s your early‑warning radar. Instead of checking configs once a quarter, CSPM keeps an eye on every new resource, policy tweak and deployment in near real time. That matters because most incidents in cloud come from boring misconfigurations, not elite zero‑days. A well‑tuned plataforma de monitoramento contínuo postura de segurança cloud will flag drift from best practices, highlight risky identities and catch public exposures before attackers start probing. Think of it as automated guardrails for messy, fast‑moving cloud environments.
Core Concepts Behind CSPM
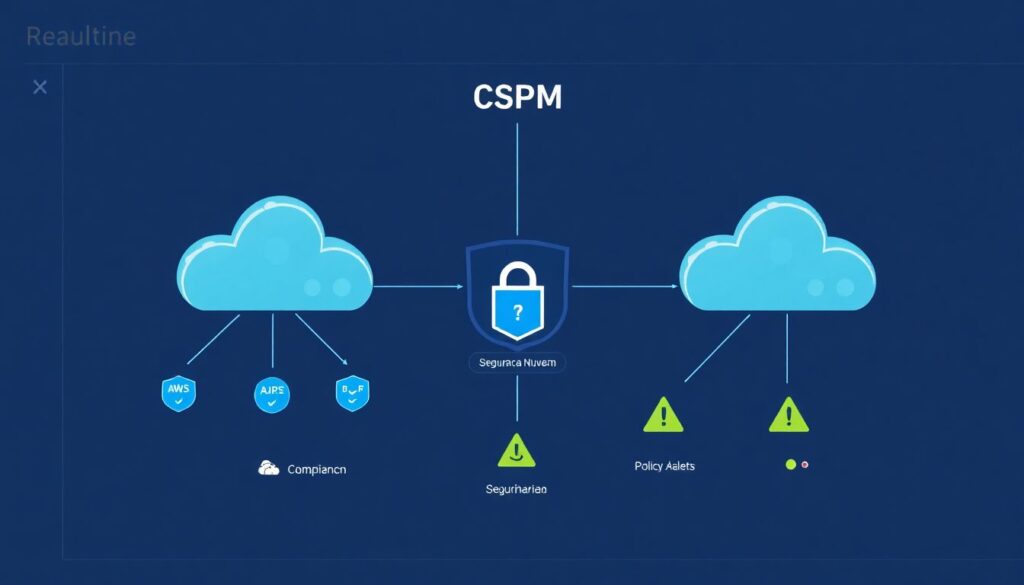
Before picking tools, it helps to clarify what CSPM actually does. At its core, it connects to your cloud providers through APIs, inventories assets, checks them against policies and regulations, then raises alerts or even auto‑fixes. Good software cspm compliance segurança em nuvem doesn’t just scan once; it re‑evaluates constantly as resources appear, tags change or networks evolve. It should also correlate issues by risk, so your team focuses on the few misconfigurations that could really hurt. When this loop runs continuously, CSPM becomes less of a project and more of a background safety net.
Essential Tools and Building Blocks
To set up effective monitoramento contínuo de postura de segurança em cloud, you’ll combine native and third‑party components. Cloud providers already ship basic CSPM‑like checks, but often you’ll want cross‑cloud depth and consistent policies. The melhores ferramentas cspm aws azure gcp use read‑only permissions, graph analysis and attack‑path modeling to show how issues link together. Around that, you’ll plug in ticketing systems, SIEM or XDR for correlation, and secret scanners for code repositories. The goal is a single set of findings that bridge configuration, identity, network and data exposure, instead of isolated dashboards nobody opens.
Must‑Have Capabilities in CSPM Tools
When evaluating ferramentas cspm monitoramento contínuo cloud, don’t get distracted only by dashboards. Focus on capabilities that you’ll actually live with daily. You’ll want broad asset discovery, context‑rich alerts and the ability to map findings back to owners through tags or accounts. Baseline policies for CIS, NIST and cloud provider benchmarks save tons of time. Finally, look for flexible APIs and webhooks so your CSPM can push data into whatever workflow tools your teams already use, instead of forcing people to log into yet another portal.
- Automated asset inventory across all accounts, regions and subscriptions
- Policy engine with built‑in and customizable rules, including exceptions
- Integrations with CI/CD, ITSM, SIEM and messaging tools for alert routing
Balancing Features and Cost
Sooner or later someone will ask about solução cspm segurança em nuvem preço, and this can get tricky. Vendors price by assets, accounts, data volume or a mix of them, so cheap pilots can quietly turn into expensive rollouts. To avoid surprises, estimate future growth: more dev accounts, more ephemeral workloads, more regions. Push vendors to show how licensing behaves under bursty workloads like short‑lived containers. Also weigh what you can offload to native tools versus premium features. A lean deployment that’s actually used is better than a luxurious shelfware platform.
Step‑by‑Step CSPM Implementation
Rolling out CSPM works best in deliberate phases instead of a big bang. Start with a single cloud and a few representative accounts: one production, one staging and a “chaotic” dev account. Connect your plataforma de monitoramento contínuo postura de segurança cloud using least‑privilege roles and verify every permission. Then run in “observe‑only” mode for a couple of weeks. Collect findings, sit with dev and ops teams, and label alerts as useful, noisy or irrelevant. Use this feedback to tune policies, name conventions and tagging before expanding coverage.
Detailed Rollout Process
To make the process concrete, treat CSPM as its own mini product. Define owners, success metrics and a simple roadmap. Start by importing a baseline ruleset, such as a CIS benchmark, and then prune or adjust it to match your risk appetite. Next, wire CSPM into your ticketing system so high‑risk issues automatically create tasks assigned to the right team. Only after this loop feels smooth should you enable auto‑remediation on a very small set of low‑risk, high‑volume misconfigurations, like public S3 buckets with no data or unused open security groups.
- Phase 1: Connect limited accounts, run read‑only scans, understand the noise
- Phase 2: Tune policies, integrate with workflows, pilot auto‑remediation
- Phase 3: Roll out to all environments, expand metrics and executive reporting
Key Metrics That Actually Matter
It’s tempting to obsess over the raw number of findings, but that metric alone is almost useless. Focus on coverage first: what percentage of your accounts, projects and subscriptions are monitored? Then track mean time to remediate for high‑risk issues, broken down by team or business unit. Rate of re‑occurring misconfigurations shows where you lack guardrails or training. Finally, measure how many critical incidents were detected by CSPM before they became real outages. Over time, aim for fewer high‑severity alerts, not just fewer total alerts.
Turning Metrics into Action
Metrics should drive behavior changes, not just decorate slides. Share CSPM stats with engineering in plain language: “we closed 90% of public storage findings in 24 hours, but database exposure lingers for a week.” Use this to prioritize enablement, like Terraform modules that bake in good defaults. You can even gamify it: publish a monthly leaderboard of teams with the fastest remediation, but pair it with help, not blame. Over a few quarters, these simple feedback loops usually shift the culture from reactive security reviews to proactive design.
Unconventional (But Practical) CSPM Use Cases
Beyond basic compliance, CSPM can power some surprisingly creative workflows. One idea is using CSPM findings as a “social graph” of your cloud: which teams own which resources, where unknown accounts appear, how services actually talk to each other. This graph helps during mergers or carve‑outs, when you must quickly isolate or move workloads. Another twist is using CSPM to validate cost‑optimization: many risky patterns, like zombie IPs or untagged storage, also waste money. Fixing security and cost together makes it easier to get engineering buy‑in.
Embedding CSPM in CI/CD and Feature Flags
A more radical approach is to treat CSPM as a deployment gate, but do it gently. Instead of blocking every high‑risk issue, start by tagging builds with the CSPM “risk score” of their target environment. If a release pushes production over a defined threshold, you flag it to the release manager rather than auto‑blocking. Over time, as confidence grows, you can introduce feature flags that automatically disable certain risky options when CSPM detects drift, such as turning off public endpoints in non‑approved regions. This keeps control dynamic, not rigid.
Choosing and Combining Tools Wisely
You don’t have to bet everything on a single vendor. Many teams mix a central enterprise CSPM with lightweight native tools. For example, combine melhores ferramentas cspm aws azure gcp with built‑in security centers for each cloud and specialized scanners for containers or Kubernetes. Your “system of record” can still be one CSPM, but enrichment may come from elsewhere. When assessing any new tool, run a short proof of value using real, messy accounts and measure how many critical issues it finds that others missed, and how quickly teams can act on its output.
Troubleshooting Common CSPM Problems
CSPM projects often stumble not on tech, but on people and process. A classic issue is alert fatigue: thousands of findings, very little action. If that sounds familiar, start by brutally disabling low‑value rules and focusing on 10–20 high‑impact checks. Another headache is missing coverage due to misconfigured roles or newly created accounts that aren’t onboarded. Automate account discovery and role creation as part of your cloud account factory. Regularly run “canary” misconfigurations in test accounts to confirm the platform still detects what you expect.
Debugging Technical Glitches
On the technical side, sync failures and inconsistent inventories can quietly undermine trust in your CSPM. When something looks off, first verify cloud API limits and throttling; noisy environments can hit rate caps. Next, check whether someone changed the CSPM role or reduced permissions. For multi‑cloud deployments, be wary of subtle differences in how services map across providers; what looks like a simple firewall rule in one cloud may be a different object in another, leading to gaps. Maintain a small lab environment where you can reproduce issues without production noise.
- Regularly validate permissions for CSPM roles and service principals
- Monitor CSPM health dashboards and error logs, not just security alerts
- Schedule quarterly “fire drills” to test detection and remediation flows
Making CSPM a Habit, Not a Project
To keep value high and costs sane, treat CSPM as an evolving capability. Revisit solução cspm segurança em nuvem preço annually with fresh asset counts and new optimization ideas, like disabling unused modules or offloading some checks to native tools. Keep an eye on emerging ferramentas cspm monitoramento contínuo cloud that experiment with graph databases and attack‑path analysis; they often reveal toxic combinations of “medium” findings that together form real risks. Above all, embed CSPM outputs into everyday workflows so engineers see it as a helpful safety net, not an external auditor.
