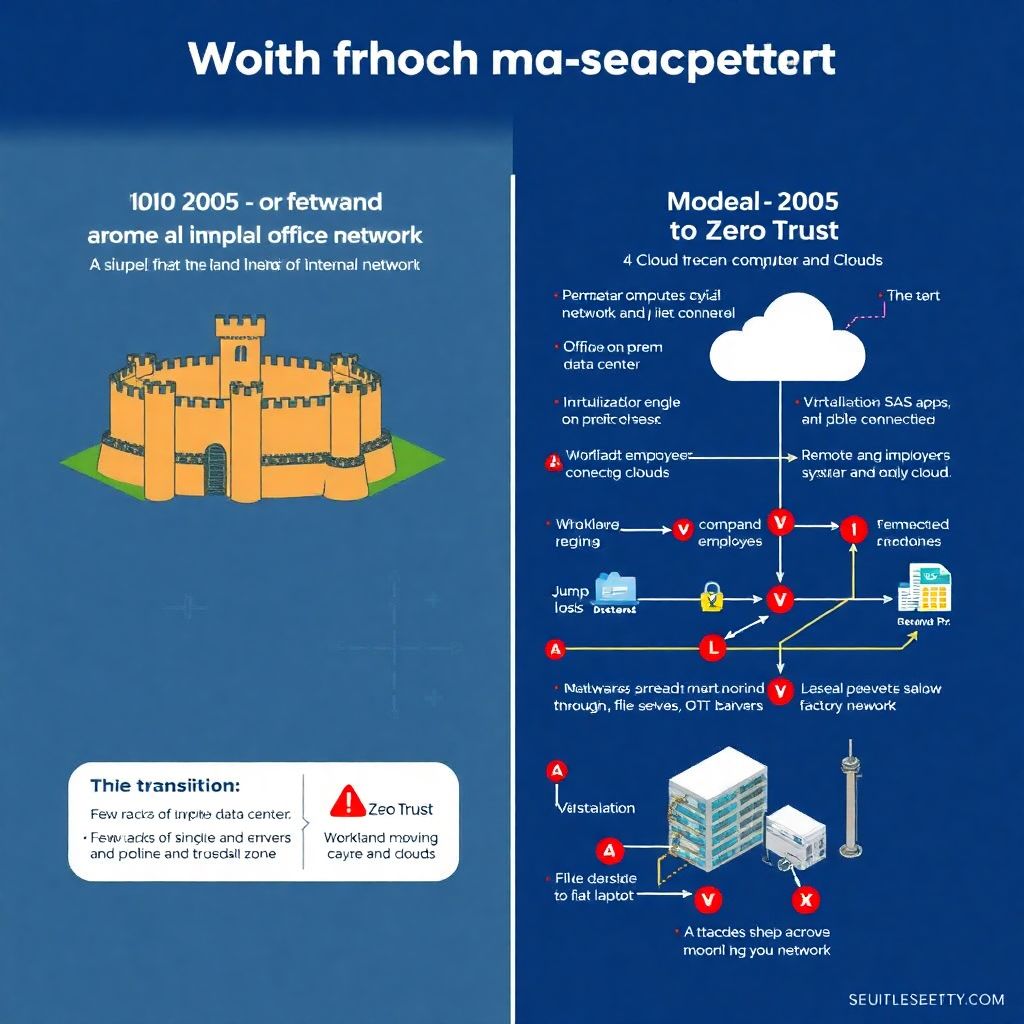
How we got here: from castle walls to cloud microsegmentation
If you look back at early corporate networks, security was basically a digital castle-and-moat. You had a big firewall at the perimeter, maybe a DMZ, and the assumption was simple: keep the bad guys out, and everyone inside is “trusted”. This worked more or less okay in the 90s and early 2000s, when apps lived in a couple of data centers and users mostly sat in the office. But as companies started adopting virtualization, SaaS, and then public cloud, that perimeter dissolved. Servers began talking across regions and clouds, developers spun up workloads in minutes, and remote access became the norm. Attackers exploited this by getting one foothold and then quietly moving laterally across flat internal networks. That lateral movement is what pushed the industry to rethink design and embrace segmentation, and later microsegmentação na nuvem soluções, as a way to shrink the attack surface instead of just thickening the outer wall.
Basic principles: what segmentation and microsegmentation really do
At its core, network segmentation is about not letting everything talk to everything. You divide your environment into logical zones and strictly control which flows are allowed between them. Classic segmentation used VLANs, subnets and firewalls between “user”, “server”, “database” and “external” zones. Microsegmentation takes that same idea and applies it at a much finer granularity: down to individual workloads, containers, or even process-level communication. The main principle is “only necessary communication is allowed, everything else is denied by default”. In practice, that means defining policies by identity and intent (this app may talk to this database over this port) instead of just IP and port. Modern ferramentas de segmentação de rede para segurança usually integrate with directories, tags, or Kubernetes labels, so that policy follows workloads as they scale or move. The result is that compromising one machine no longer gives an attacker a free pass across the entire network.
– Break the network into meaningful security zones
– Enforce least-privilege connectivity between those zones
– Design policies around applications and data, not just IP ranges
Zero Trust mindset: why cloud changes the game
Segmentation on paper is one thing; making it work in a highly dynamic cloud is another. Cloud-native architectures constantly spin resources up and down, autoscale groups, and shift traffic across regions. In such an environment, static firewall rules tied to IPs quickly become unmanageable. That’s where the Zero Trust philosophy comes in: “never trust, always verify”, whether traffic is coming from inside or outside the network. Instead of assuming that an internal subnet is safe, serviços de zero trust e microsegmentação verify user identity, device posture, workload identity and context before allowing communication. In the cloud, this often means defining policies using tags, service accounts or labels and offloading enforcement to agents or cloud-native controls close to each workload. Combined with continuous monitoring, this reduces the blast radius of any compromise and gives security teams a much more granular view of what is actually talking to what across their environments.
Real-world case #1: stopping ransomware lateral movement
Consider a mid-sized manufacturing company that got hit with ransomware. Initially, the infection came from a phishing email opened by a finance employee. Because their internal network was almost flat, the malware quickly spread from office laptops to file servers, jump hosts and even some OT systems used on the factory floor. Recovery took weeks, and the business interruption was painful. After that disaster, they decided to redesign their network. They introduced strict segmentation between office IT, production systems and management networks, along with microsegmentation around critical file servers and domain controllers. Using one of the commercial plataformas de segurança de rede em nuvem, they deployed lightweight agents on servers that enforced “allow only known-good flows” policies. Six months later, another ransomware attempt made it into the environment via a compromised VPN account. This time, the malware could only hit the initial machine and a couple of adjacent services before the unusual traffic patterns triggered alerts, and the microsegmentation policies blocked further lateral spread automatically.
– Flat networks let malware move quickly and quietly
– Segmentation plus microsegmentation can confine damage to a tiny area
– Visibility into actual flows helps tune policies without breaking apps
Real-world case #2: PCI scope reduction for a SaaS provider
A SaaS company handling payment data in the cloud faced growing pressure from auditors. Their payment processing microservice ran in Kubernetes alongside dozens of other services, and the entire cluster had effectively become part of the PCI scope. That meant heavier controls, more audits and higher costs. To fix this, they used microsegmentation na nuvem soluções that integrated with Kubernetes labels. They created a “cardholder-data” segment containing only the payment and tokenization services and restricted inbound traffic to them from a very small set of front-end pods through specific ports using mutual TLS. Outbound from this segment was limited strictly to a key management service and a logging pipeline. Everything else in the cluster was segregated into less sensitive zones. When the next audit came, the company could demonstrate, with clear policies and logs, that only tightly controlled flows touched card data. The auditor agreed to narrow the PCI scope, saving both money and operational overhead while actually improving security.
How it’s implemented: from theory to practical architecture
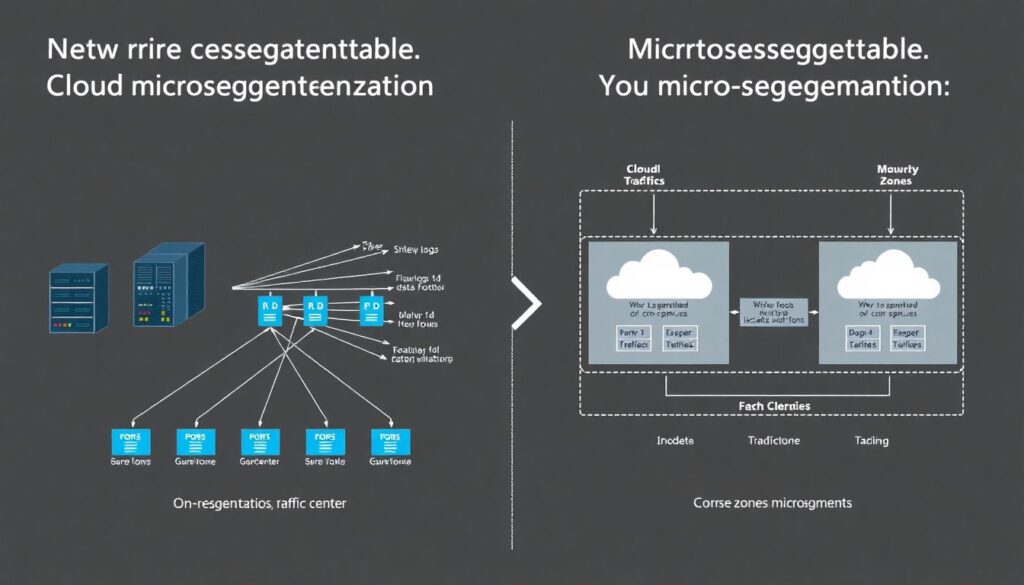
In practice, network segmentation and cloud microsegmentation are rarely built from scratch; they evolve from what an organization already has. On-prem, you often start by mapping out existing traffic—who talks to whom, over which ports—using flow logs or packet captures. Then you define coarse zones: users, application servers, databases, management, third-party connections. In the cloud, you might rely on security groups, network ACLs and virtual networks for those broader segments. Microsegmentation adds a more precise control layer on top. Some teams bake policies directly into sidecars or service meshes, while others prefer agent-based tools that sit on each workload and enforce policies locally. Whichever model you choose, the same workflow repeats: observe, model, simulate, then enforce. You first run policies in “alert only” mode to avoid breaking production traffic, then gradually switch them to blocking as confidence grows and false positives are eliminated.
Real-world case #3: cleaning up a multi-cloud “spaghetti” network
A global media company had grown fast and adopted multiple clouds without a central design. Each team created its own virtual networks, VPN tunnels and peering links, leading to a messy mesh where almost any workload could, in theory, reach almost anything else. Troubleshooting incidents was slow, and pen tests repeatedly showed easy lateral movement paths. The security team decided not to rip everything out, but to layer microsegmentation on top. They chose software de controle de acesso e microsegmentação that could pull metadata from AWS, Azure and their on-prem VMware environment. After a month of baselining, they defined a handful of logical groups: content ingestion, transcoding, editorial tools, public APIs, corporate IT and shared services like logging. Policies were written in human-friendly terms (“editorial tools may call content APIs on ports X,Y,Z”) rather than IP lists. Over time, they identified dozens of obsolete or risky connections and removed them. The result was a much clearer, more maintainable architecture that actually matched how the business worked.
– Start by discovering real traffic, not by guessing policies
– Use metadata and tags to describe business logic, not machine IPs
– Phase in enforcement gradually to avoid outages and application breakage
Common misconceptions and why they’re dangerous
One of the biggest myths is that segmentation is only for big enterprises or “high security” industries. In reality, small and medium businesses are often the ones hardest hit by breaches, and even simple segmentation can dramatically limit damage. Another misconception is that cloud providers “handle it all” by default. While major clouds offer good primitives, they do not automatically build a least-privilege model tailored to your applications; that’s still on you. Some engineers also assume that segmentation will inevitably slow everything down or make deployments painful. Done poorly, that can happen, but well-designed policies integrated into CI/CD can actually make changes safer and more predictable by documenting intended flows. Finally, people often think Zero Trust is a product you can buy, rather than a design approach. In reality, you combine multiple tools—identity, logging, policy engines, and ferramentas de segmentação de rede para segurança—to get closer to that goal of “never trust, always verify”.
Where to start and how to move forward
If your network or cloud environment feels like a black box, the first step is simply visibility. Turn on flow logs in your cloud accounts, collect them centrally, and try to answer: which apps truly need to talk to which databases or external services? From there, sketch broad segments and enforce just a few high-value controls: protecting domain controllers, critical databases, admin interfaces and jump hosts. Next, pilot microsegmentation around a contained environment—say, one Kubernetes namespace or a specific business application—before rolling it out wider. Keep developers in the loop so policies reflect real use cases, and bake security checks into pipelines so that new services come with segmentation rules from day one. Over time, with a mix of serviços de zero trust e microsegmentação, cloud-native controls, and careful monitoring, you can turn a wide-open network into one where every connection is intentional, observable and defensible, sharply reducing the attack surface without paralyzing the business.