Entendendo o jogo: compliance em cloud sem pânico

Preparing your cloud for audits like LGPD, GDPR, ISO 27001 and PCI-DSS doesn’t need to be a fire drill every quarter. Think of it as designing an environment where being audited is just another Tuesday. Instead of running after evidences at the last minute, you build your cloud so logs, configs, approvals and risk decisions are always ready to show. That’s where a mix of automation, good architecture and some unconventional tricks can turn a stressful “auditoria” into a structured routine, even em ambientes multi-cloud complexos.
Mapeando requisitos: traduza normas para controles práticos
Conectando LGPD, GDPR, ISO 27001 e PCI-DSS ao mundo real
Before touching any console, you need a requirements map. Take each framework and translate articles and clauses into tangible cloud controls: encryption, IAM policies, key rotation, data retention, incident response, vendor management. For LGPD and GDPR, focus on data subject rights, legal bases and data minimization. For ISO 27001, think Annex A controls applied to cloud. PCI-DSS, por sua vez, exige segmentação rigorosa, hardening e monitoração de ambiente de pagamento. This mapping becomes your “control matrix” tied to specific services and configs in each cloud provider.
Usando consultoria de forma inteligente, não cega
If you work with consultoria lgpd para ambientes em nuvem, use the consultants as translators and challengers, not as “document writers”. Ask them to help you design a reusable control set: one policy for encryption that already covers LGPD, GDPR and ISO. Push for cloud-native interpretations instead of generic on‑prem templates. For PCI, bring in an empresa especializada em pci dss em nuvem to validate unusual patterns like serverless payments or tokenization services, so you avoid redoing your architecture right before the formal audit window.
Ferramentas essenciais: vá além do básico
Ferramentas de governança e inventário
You can’t pass an audit if you don’t even know what you have. Cloud-native asset inventory plus CMDB integration is mandatory. Use ferramentas de governança e compliance em cloud (CSPM, CNAPP, policy-as-code) to maintain a live map of resources, tags, data locations and ownership. Turn “shadow” workloads into first-class citizens by forcing every new project through an automated landing zone that already includes baselines for logging, IAM guardrails and network segmentation. This turns your cloud into an environment where “non-compliant by design” simply cannot be provisioned.
Monitoring, logs e gestão de riscos
Combine SIEM, cloud-native monitoring, DLP and vulnerability scanners into one narrative: detect, correlate, respond. For serviços de compliance cloud para gdpr e lgpd, centrally manage data discovery and classification so you can prove which workloads process personal data, at what level of sensitivity and in which region. Tie risk registers directly to technical findings: each critical misconfiguration should link to a risk entry with owner, deadline and mitigation. That way, during an auditoria de segurança em cloud para iso 27001, you show a living risk treatment plan, not a pretty but dead spreadsheet.
- Use policy-as-code (OPA, AWS Config, Azure Policies, GCP Policies) to encode controls directly in infrastructure.
- Enable immutable logging with centralized retention and legal hold, covering admin actions, API calls and data access.
- Automate tagging standards (owner, data type, criticality, jurisdiction) at deployment time to support compliance scoping.
Processo passo a passo: do caos ao ambiente auditável
Passo 1: Desenhe uma “baseline de compliance” por tipo de dado
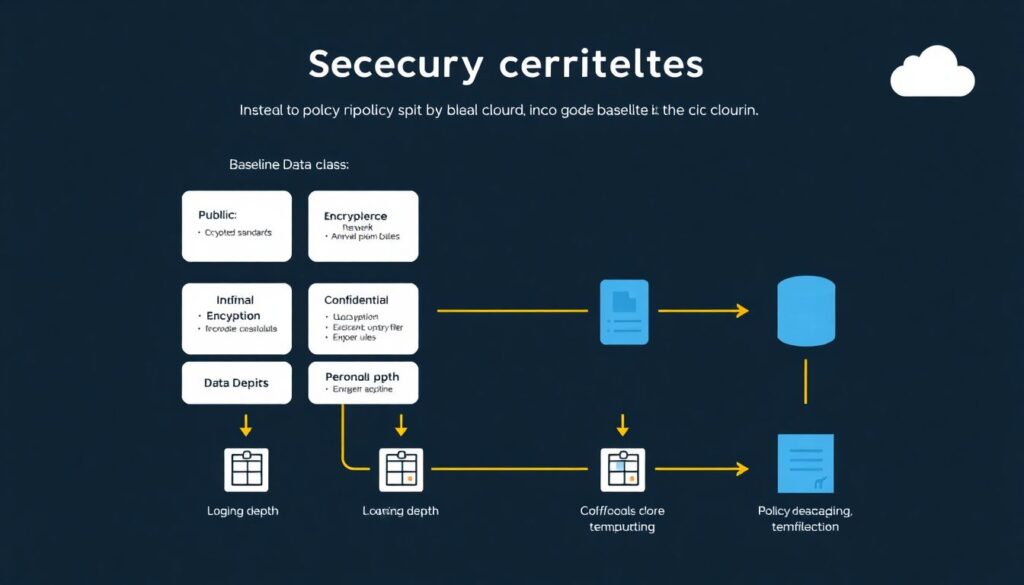
Instead of creating one giant policy for the whole cloud, split your baseline by data class: public, internal, confidential, personal, payment. For each class define mandatory encryption standards, network exposure rules, logging depth and approval flows. Then encode this in templates (Terraform, CloudFormation, Bicep) and reusable landing zones. New workloads pick a data class, and the baseline is applied automatically. This approach drastically reduces the effort to prove LGPD and GDPR controls, because each workload inherits documented, versioned security defaults.
Passo 2: Crie uma “rota de auditoria” para cada fluxo de dados
Auditors always end up asking: “Where does this data come from, where does it go, who can see it, and why?” Build “audit trails” as diagrams plus live queries. For each critical data flow (onboarding, billing, payment, support), maintain a short design doc mapping services, regions, encryption keys, IAM roles and third parties. Link those docs to dashboards that show real metrics (access logs, failed logins, DLP alerts). This hybrid of architecture-as-document and metrics-as-proof turns theoretical policies into demonstrable evidence in minutes, not days.
Passo 3: Ensaios de auditoria e simulações de incidentes
Run dry‑runs of audits twice a year. Simulate a full LGPD data subject request: “delete my data”, across microservices, analytics and backups. Time the process and capture gaps. For ISO 27001, execute a mock risk review focusing only on cloud changes made in the last six months. For PCI-DSS, simulate a key compromise and walk through rotation in your KMS plus re-encryption of test data. These exercises give you ready-made evidence and make the real audit feel like a replay of what the team already practiced, not an improvised show.
Nestandard solutions: pense como produto, não como projeto
Transforme compliance em um “produto interno”
One unconventional but powerful move is to treat compliance as an internal product. Crie um “Compliance Cloud Platform”: a self‑service portal where squads can request new environments, choose data classification and automatically receive network, IAM, keys and monitoring aligned with all frameworks. The “product team” (security, legal, privacy) manages the backlog: new regulatory requirements become features and policies released in sprints. This mindset shifts the conversation from “security blockers” to “platform capabilities” and lets you scale governance without micro-managing each team.
Use gamificação e métricas públicas entre times
Another non-obvious trick: expose compliance metrics per team, not to punish, but to spark healthy competition. Dashboards show time-to-fix critical misconfigs, coverage of encryption, number of successful privacy drills. Offer rewards for squads that keep zero criticals for a full quarter or that improve PCI hardening the fastest. This culture hack makes developers care about passing audits before the security team even asks. Auditors often perceive this maturity when they realize that alert reduction and remediation are owned by product teams, not only by security.
- Provide a “golden path” repo: reference microservices pre-configured with logging, tracing, privacy controls and key rotation.
- Offer ready-made Terraform modules that are “audit friendly”: documented variables, built‑in tags and evidence links.
- Integrate privacy-by-design checklists into pull requests using bots that comment when risky patterns appear.
Preparando documentação e evidências sem sofrimento
Automatize coleta de evidências
Manual screenshots are a trap. Instead, script evidence generation: commands to export IAM policies, security group rules, KMS key states, last rotation dates, DLP policies, backup configurations. Store these outputs in a version-controlled “audit artifacts” repository with timestamps. Link artifacts to specific controls in your control matrix. When the auditor asks “prove that only certain roles access production”, you simply point to a pre-generated report plus the script that produced it, which dramatically increases confidence and reduces back-and-forth.
Crie narrativas curtas para cada requisito crítico
Auditors respond well to clear, repeatable stories. For each group of controls (access control, logging, incident management, privacy rights), create one-page narratives: context, approach, tools, main dashboards and where evidences live. Avoid marketing fluff; be precise: “Admin access uses SSO + MFA + privileged access management; all actions are logged in X; alerts route to Y; evidence scripts are Z.” This structure transforms a complex cloud into a comprehensible system, even when you’re dealing with multiple providers and hybrid workloads.
Resolução de problemas: quando algo quebra perto da auditoria
Diagnóstico rápido de gaps e desvios
Unexpected gaps will appear days before an audit: an unencrypted bucket, a missing backup, a rogue admin role. Instead of panic, run a “last mile scan” using your CSPM plus targeted scripts focused on the auditors’ scope. Classify findings as “fix now”, “compensating control” or “accept with plan”. Document each decision in your risk register with justification and timeline. Many frameworks accept well-documented exceptions with mitigation; what hurts you is pretending everything is perfect and being caught by basic questions during the sessions.
Planos de contenção e melhorias contínuas
When you can’t fully fix an issue before the audit, design a containment plan: temporary tighter monitoring, manual checks, or additional approval flows. Present this transparently to auditors with clear milestones. After the audit, run a retrospective: which evidence took longest, which questions surprised you, where automation failed. Turn each pain point into a backlog item for your compliance platform. Over a couple of cycles, your cloud evolves from “barely ready” to “always on audit mode”, where new regulations or standards feel like configuration changes, not existential crises.
Conclusão: faça da nuvem um ambiente auditável por padrão
Compliance como consequência do bom design
Preparing your cloud for LGPD, GDPR, ISO 27001 and PCI-DSS is less about memorizing clauses and more about engineering: predictable baselines, automated controls, clear ownership and evidence on tap. With the right mix of serviços de compliance cloud para gdpr e lgpd, cloud-native security tools, and partnerships como uma empresa especializada em pci dss em nuvem, compliance becomes a built-in characteristic of your architecture. Over time, audits stop being extraordinary events and turn into checkpoints confirming that your day‑to‑day operations already match what the regulations expect.
