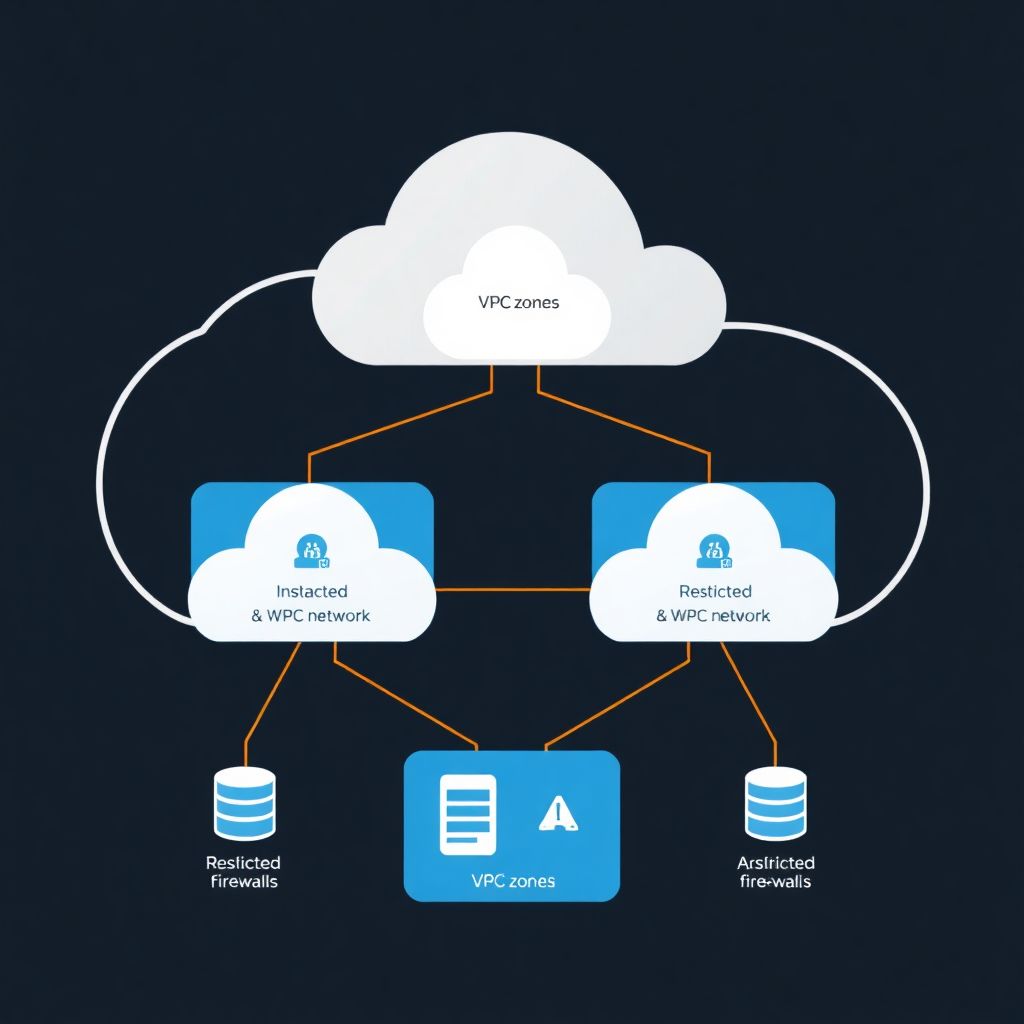
Secure virtual networking in cloud means designing VPC/VNet layouts that isolate tenants and environments, using strict subnet zoning, least-privilege routing, layered firewalls, and microsegmentation to control east-west traffic. For pt_BR teams, focus on simple patterns: clear IP plans, default deny policies, minimal public exposure, and automated, auditable rules.
Security snapshot: core VPC/VNet controls
- Use separate VPCs/VNets per environment (prod/stage/dev) and per tenant when compliance or risk justifies it.
- Apply subnet tiers (public, private, restricted) with explicit routing; avoid direct internet access from workloads.
- Enforce default deny with layered firewall rules: perimeter, subnet-level and host-based controls.
- Adopt microsegmentation for sensitive workloads to limit lateral movement inside the cloud.
- Centralize logging (flow logs, firewall logs, DNS) and continuously review anomalies.
- Automate policy deployment via IaC (Terraform, ARM/Bicep, CloudFormation) and CI/CD validations.
- Regularly test segurança em redes virtuais na nuvem through scans, misconfiguration checks and tabletop exercises.
Designing a secure VPC/VNet topology for multi-tenant clouds
This setup fits intermediate teams running multiple environments, SaaS platforms or multi-business-unit workloads in AWS, Azure or GCP. It is ideal when you must separate tenants, comply with regulations or reduce blast radius in case of compromise.
Do not adopt a very fragmented multi-VPC/VNet architecture if:
- Your team is small and has limited network expertise, and you lack tooling for centralized management.
- Your workloads are simple, with only one or two applications and no strong isolation requirements.
- You cannot maintain consistent routing, DNS and identity policies across many network boundaries.
Typical topology for как como configurar vpc segura na aws and melhores práticas de vnet segura no azure:
- Use one landing zone per organization, with shared services (logging, identity, security tools).
- Create separate VPCs/VNets per environment: prod, stage, dev, sandbox.
- For multi-tenant SaaS, choose:
- Per-tenant VPC/VNet for high isolation; or
- Shared VPC/VNet + strict microsegmentation for many small tenants.
- Standardize IP ranges to avoid overlap (e.g., non-overlapping RFC1918 blocks per VPC/VNet).
- Use centralized connectivity (Transit Gateway, Azure Virtual WAN, Cloud Router) instead of full mesh peering.
Subnet zoning, routing and least-privilege segmentation
Before applying segmentation, ensure you have the right prerequisites, access and tools.
Prerequisites: accounts, roles and baseline
- Cloud accounts/subscriptions for each environment, organized in an AWS Organization or Azure Management Groups.
- IAM roles for network/security engineers with least-privilege permissions to manage VPC/VNet, routes and firewalls.
- Baseline landing zone with centralized logging, identity provider and configuration management in place.
Network design inputs you must define
- IP plan: CIDR ranges per VPC/VNet and per subnet, documented and reviewed.
- Security zones:
- Public (only load balancers, bastions, edge proxies).
- Private app (application servers, services exposed via internal load balancers).
- Data (databases, caches), often with more restrictive ACLs.
- Management (backup, monitoring, jump hosts).
- Trust matrix: which zones can talk to which, on which ports (e.g., app→db on 5432 only).
Core tools per cloud provider
- AWS:
- VPC, subnets, route tables, Internet/NAT Gateways.
- Security Groups and Network ACLs.
- Transit Gateway (central routing), AWS Network Firewall or third-party NGFW.
- Azure:
- Virtual Network (VNet), subnets, route tables (UDR).
- Network Security Groups (NSG) and Application Security Groups (ASG).
- Azure Firewall, Azure Virtual WAN, and optionally third-party appliances.
- GCP:
- VPC, subnets (regional), custom routes.
- VPC firewall rules and hierarchical policies.
- Cloud Firewall, Cloud Armor, and hub-and-spoke via VPC peering or Network Connectivity Center.
Access and automation requirements
- IaC tooling: Terraform, AWS CloudFormation, Azure Bicep/ARM, or GCP Deployment Manager.
- CI/CD pipeline able to:
- Plan and preview network changes.
- Run policy-as-code checks (e.g., Open Policy Agent, Checkov).
- Require approvals for production changes.
- Read-only access for auditors and security teams to review routing and firewall configurations.
Firewall strategy: perimeter, distributed and host-based rules
This section provides a safe, step-by-step plan to design and implement firewall controls for segmentação de rede na nuvem across AWS, Azure and other providers.
- Define your security zones and traffic policy
Document which zones exist (public, app, data, management) and which flows are allowed between them.- Start from default deny (no flows allowed) and add only necessary exceptions.
- Separate inbound/outbound policies (from internet, to internet, inter-zone, inter-VPC/VNet).
- Establish perimeter firewall and entry points
Choose managed or appliance-based firewall para segmentação de rede na nuvem at the edge.- Terminate internet traffic via load balancers, WAF and edge firewalls.
- Use bastion hosts or VPN/Zero Trust access instead of opening SSH/RDP to the world.
- Apply subnet-level distributed firewalls
Use cloud-native constructs (Security Groups, NSGs, VPC firewall rules) to enforce zone policies.- Group workloads by role (web, app, db) using tags/ASGs and apply rules to the group.
- Restrict database subnets to only accept traffic from application subnets on required ports.
- Harden host-level firewalls
Enable OS firewalls as the last line of defense.- Linux: iptables/nftables, firewalld, or ufw with a default deny inbound policy.
- Windows: Windows Defender Firewall with host-based rules reflecting application needs.
- Centralize logging and alerting for firewall events
Ensure all layers log traffic and blocks.- Enable VPC flow logs, NSG flow logs and firewall logs.
- Send logs to a central SIEM/observability platform with alerts for suspicious patterns.
- Implement policy-as-code and safe deployment
Manage firewall policies as code for repeatability and safety.- Store rules in Git; use pull requests, reviews and automated linting.
- Test changes in non-production VPCs/VNets before rollout to production.
- Regularly review and refine firewall rules
Schedule periodic cleanups to remove unused or overly permissive rules.- Use log analysis to identify unused access rules.
- Gradually tighten
0.0.0.0/0orAnyrules into specific CIDR ranges or security groups.
Provider-specific configuration snippets
AWS: simple Security Group example (Terraform) for como configurar vpc segura na aws
resource "aws_security_group" "web_sg" {
name = "web-sg"
description = "Web tier SG"
vpc_id = aws_vpc.main.id
ingress {
description = "HTTPS from internet"
from_port = 443
to_port = 443
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Role = "web"
}
}Azure: NSG + ASG baseline example (Bicep) for melhores práticas de vnet segura no azure
resource webAsg 'Microsoft.Network/applicationSecurityGroups@2023-04-01' = {
name: 'asg-web'
location: resourceGroup().location
}
resource webNsg 'Microsoft.Network/networkSecurityGroups@2023-04-01' = {
name: 'nsg-web'
location: resourceGroup().location
properties: {
securityRules: [
{
name: 'Allow-HTTPS-From-Internet'
properties: {
access: 'Allow'
direction: 'Inbound'
priority: 100
protocol: 'Tcp'
sourceAddressPrefix: '*'
sourcePortRange: '*'
destinationApplicationSecurityGroups: [
{
id: webAsg.id
}
]
destinationPortRange: '443'
}
}
]
}
}Fast-track mode: minimal safe firewall rollout
- Define 3-4 zones (public, app, data, management) and write down allowed flows between them.
- Create subnet-level rules (Security Groups/NSGs) that implement those flows with default deny.
- Keep only load balancers and bastions public; everything else stays in private subnets.
- Turn on flow logs and firewall logs, send them to a central log workspace, and review weekly.
- Migrate any manual firewall changes into Terraform/Bicep/CloudFormation as soon as possible.
Microsegmentation patterns: labels, agents and enforcement points
Use this checklist to verify that your microsegmentation and soluções de microsegmentação em cloud are correctly implemented and safe.
- All workloads are consistently labeled/tagged by role, environment, sensitivity and owner.
- Segmentation policies reference labels/tags or groups, not static IPs wherever possible.
- Every policy has a clear business justification and is documented in code or central policy console.
- East-west traffic between application tiers is restricted to required ports and protocols only.
- High-value assets (databases, secrets stores, control-plane components) have the strictest policies.
- Microsegmentation agents or enforcement points are deployed through your existing deployment pipeline.
- Changes to segmentation policies go through review and automated testing before reaching production.
- Logs clearly show allowed and blocked connections per label/group, making troubleshooting feasible.
- There is a rollback plan for segmentation changes that could break critical application flows.
- Security and platform teams jointly review segmentation rules at regular intervals.
Controlling east-west traffic: service mesh, ACLs and isolation gates
Common mistakes when trying to control east-west traffic using service meshes, ACLs and isolation mechanisms:
- Relying only on perimeter firewalls while leaving intra-VPC/VNet traffic mostly unrestricted.
- Deploying a service mesh without actually enforcing authentication (mTLS) and authorization policies.
- Using overly broad ACLs that allow
Any-to-Anytraffic between subnets or namespaces. - Mixing production and non-production workloads in the same subnets or clusters without strict policies.
- Not updating network policies when applications change ports, paths or dependencies.
- Assuming that Kubernetes NetworkPolicies or service mesh defaults are secure without explicit review.
- Lacking isolation between tenants in multi-tenant clusters or shared VPC/VNet environments.
- Disabling east-west security features during incident response or performance debugging and forgetting to re-enable them.
- Failing to align service identity (certificates, JWTs) with network-layer policies, leading to gaps.
- Not documenting isolation gates (e.g., specific gateways or proxies) and how they are configured.
Visibility and enforcement: logging, policy automation and incident playbooks
There are multiple options for building visibility and enforcement; choose based on your team size, skills and tooling.
- Cloud-native only (VPC flow logs, Security Groups/NSGs, provider firewalls)
- Best when you want low operational overhead, tight integration and moderate complexity.
- Suitable for smaller teams or when you mainly use one cloud provider.
- Cloud-agnostic security platforms (SASE, CNAPP, cloud microsegmentation tools)
- Useful for multi-cloud and hybrid deployments needing统一 policy across environments.
- Good when you already operate a central security stack and have integration capacity.
- Service-mesh-centric approach (Istio, Linkerd, AWS App Mesh, Azure service mesh options)
- Recommended when most workloads are containerized and you need deep L7 visibility and control.
- Requires platform engineering skills and solid observability practices.
- Host-based and EDR-focused enforcement
- Relevant when you have strict compliance on endpoints or legacy workloads that cannot be easily re-networked.
- Pairs well with VPC/VNet segmentation but should not replace network-layer controls.
Compact comparison: firewall and microsegmentation options
| Option | Scope | Strengths | Limitations | Good fit |
|---|---|---|---|---|
| Perimeter firewall (cloud-native or appliance) | North-south traffic (internet, on-prem) | Central control, good for ingress/egress, DDoS/WAF integration | Limited visibility inside VPC/VNet, cannot fully enforce lateral movement | Edge protection, simple architectures |
| Distributed firewall (Security Groups/NSGs) | Subnet/instance level | Cloud-native, scalable, low latency, IaC-friendly | Can become complex without tag-based design and policy-as-code | Most standard cloud workloads |
| Host-based firewall | Individual VM/container host | Last line of defense, fine-grained control, complements network rules | Operational overhead, per-OS configuration and monitoring | Sensitive systems, mixed OS estates |
| Microsegmentation platform | Workload-to-workload flows | Strong lateral movement control, label-based policies, good visibility | Agent footprint or overlay complexity, licensing and governance needed | Multi-tenant SaaS, regulated workloads |
| Service mesh network policies | Service-to-service in clusters | L7-aware, integrates auth (mTLS), rich telemetry | Requires platform maturity, mainly for containerized workloads | Microservices-heavy, Kubernetes-based platforms |
Practical troubleshooting and deployment pitfalls
How do I test that my VPC/VNet segmentation is working correctly?

Use simple connectivity tests (e.g., curl, nc, Test-NetConnection) from each zone to expected destinations. Confirm that allowed flows succeed and all others fail. Cross-check results with flow logs to ensure the correct rules are matching.
What should I do if I accidentally lock myself out with a firewall change?
Always keep an emergency access path such as a bastion in a separate security group or an out-of-band management VPC/VNet. Use your IaC pipeline to rollback to the last known-good configuration instead of manual hotfixes.
Why are my microsegmentation agents causing application issues?
Usually policies are too strict or not aligned with real application dependencies. Start in monitoring mode, learn normal flows, then enforce gradually. Coordinate with application owners and test in non-production before enabling enforcement in production.
How can I keep firewall rules manageable over time?
Use tags/labels and groups (ASGs, security groups, dynamic groups) instead of per-IP rules. Manage policies as code in a repository, with naming conventions, owners and periodic cleanups based on log usage data.
Do I still need host-based firewalls if I use strong VPC/VNet rules?

Yes, host-based firewalls provide an additional barrier if network rules are misconfigured or an attacker gains a foothold. Keep host rules simple, aligned with application ports, and centrally managed via configuration management tools.
When should I add a service mesh for east-west security?
Consider a mesh when most critical workloads run in Kubernetes, you need mTLS between services, and you already have basic segmentation in place. Do not use a mesh as a quick fix for fundamental VPC/VNet and firewall design issues.
How do I choose between cloud-native controls and third-party soluções de microsegmentação em cloud?
Start with cloud-native controls for simplicity and cost efficiency. Move to third-party platforms if you operate multi-cloud at scale, need unified policy and visibility, or must meet strict audit and compliance requirements across heterogeneous environments.