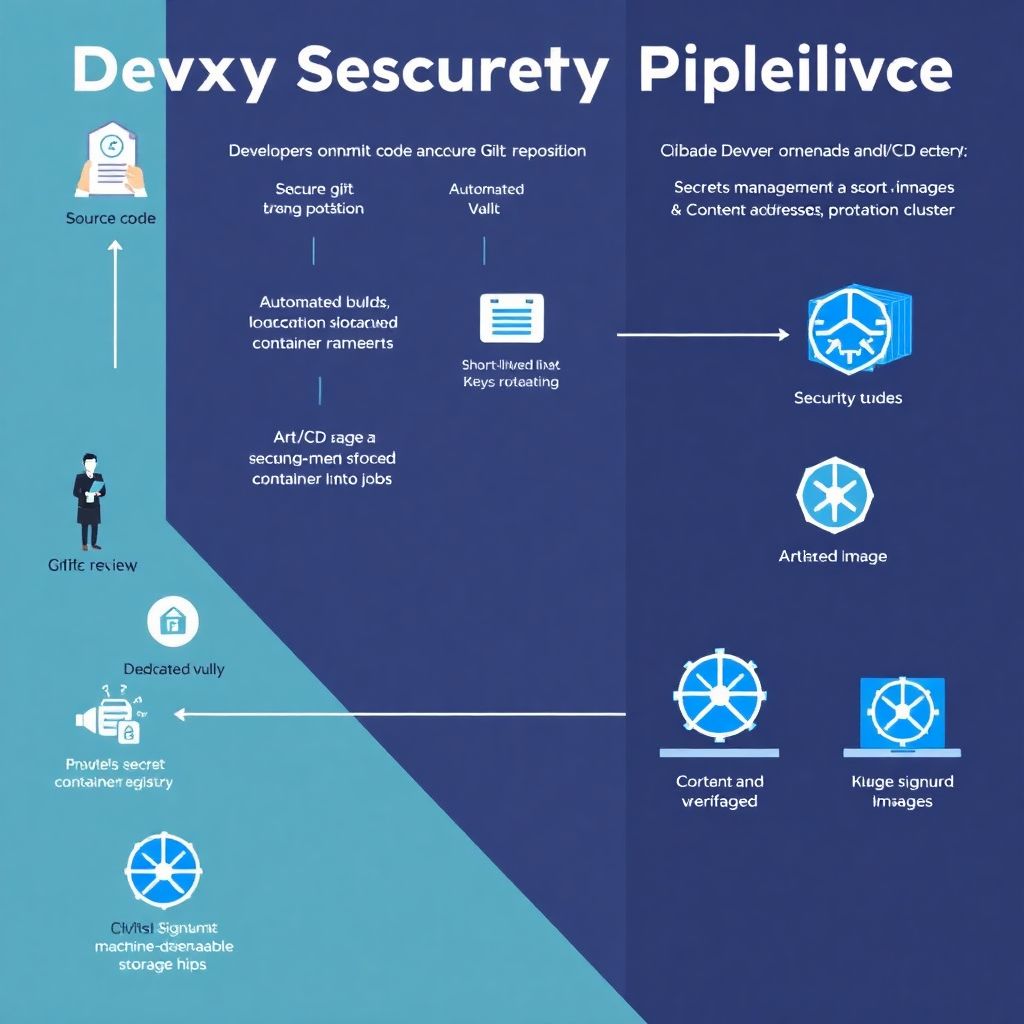
Why CI/CD security is the lever that changes your entire delivery game
When teams talk about CI/CD, they usually focus on speed: more deployments, more automation, more features in production. But if you ignore security, that same pipeline becomes a perfectly oiled weapon — only pointed at your own infrastructure. Segurança em pipelines CI/CD isn’t a “nice to have”, it’s the backbone that lets you sleep at night after hitting “merge”. When you treat your pipeline as critical infrastructure — at the same level as your production cluster — every improvement in protection of secrets, artefacts and registries pays off not just in less risk, but in more freedom to experiment and ship bold ideas.
Segredos no pipeline: o elo mais fraco ou sua maior vantagem estratégica
It’s hard to overstate how dangerous leaked secrets are. Tokens in logs, passwords in environment variables, SSH keys in config files — the classic “small oversight” that becomes a critical incident. Proteção de segredos em pipelines DevOps starts with an uncomfortable truth: humans are bad at handling secrets manually. Copy–paste to CI settings, storing them in a password manager and hoping for the best, or leaving them as plaintext in repo history — all of that scales badly. The turning point is when you fully accept that secrets must be machine‑managed: vaulted, rotated, audited and injected just‑in‑time, never hardcoded and never long‑lived.
Real‑world case: the token that opened the entire cloud
One fintech team I worked with had a “temporary” personal access token stored directly in a GitHub Actions secret, shared across multiple workflows. It leaked through a debug log inside a third‑party action. An attacker scanned public logs, found the token and used it to pivot into the company’s cloud account. Thankfully, guardrails stopped data exfiltration, but they still spent a week rotating credentials and re‑auditing IAM. The fix was brutal but effective: move every sensitive value into a centralized secret manager, auto‑rotate keys, and forbid personal tokens in pipelines entirely. That incident did more to build a security culture than any internal training ever had.
From “just hide the secrets” to segurança em CI CD melhores práticas
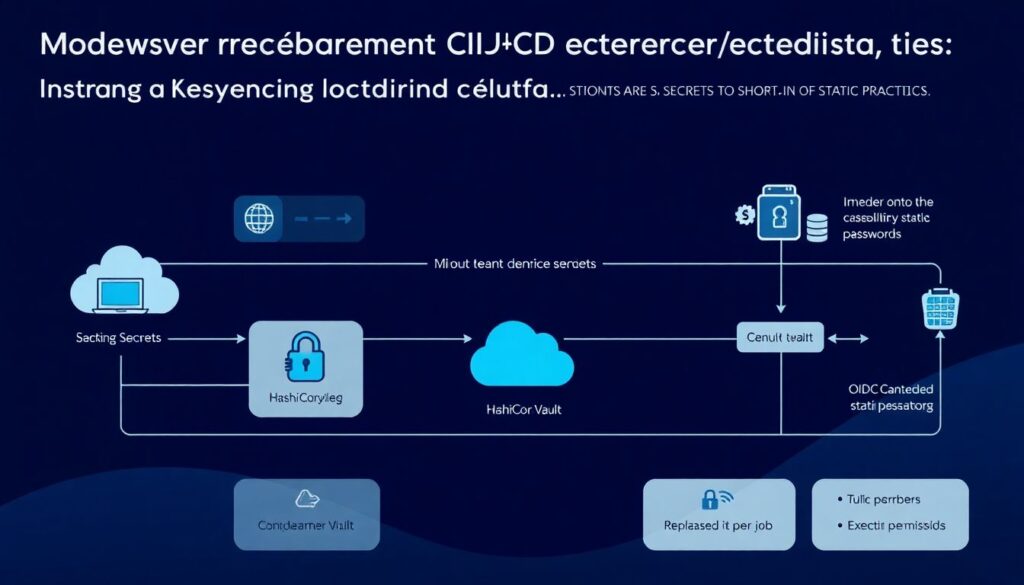
If you want to move from “we encrypt some stuff” to segurança em CI CD melhores práticas, treat secrets as short‑lived capabilities, not static passwords. Use cloud KMS or tools like HashiCorp Vault to issue dynamic DB creds per job, OIDC‑based federation instead of static cloud keys, and explicit policies that define which pipeline context can access which secret. The more granular and auditable this is, the less scary it becomes to give your pipelines real power. Over time, you’ll notice something interesting: developers start thinking in scope‑limited tokens instead of “god‑mode” keys, and your default mental model shifts toward least privilege.
Artefacts and images: the invisible supply chain you’re already running
Every build in your CI/CD pipeline produces artefacts: binaries, packages, Helm charts, Docker images. Many teams obsess about code review, yet treat artefact storage as a boring detail. That’s a blind spot. If an attacker can swap an artefact in your registry or artefact repository, they’ve effectively edited your code after review — only now it’s invisible. Learning como proteger artefatos e imagens de containers no CI CD is less about fancy tools and more about building a verifiable story: which source commit produced which artefact, who approved it, and what guarantees you have that no one tampered with it in transit or at rest.
Case: the “harmless” internal image that became a backdoor
In a SaaS company, internal tooling containers were pushed to a private registry with minimal controls. An engineer’s laptop was compromised through a browser exploit, and the attacker grabbed the registry credentials from a local config file. They replaced one internal image with a modified version that quietly exfiltrated environment variables at runtime. The blast radius could have been huge, but was caught because the team had recently enabled image signing and promotion gates: only signed images built by CI from main were allowed in production. The rogue image never passed the admission controller. Without that guardrail, the compromise likely would have gone unnoticed for months.
Building a trustworthy artefact flow
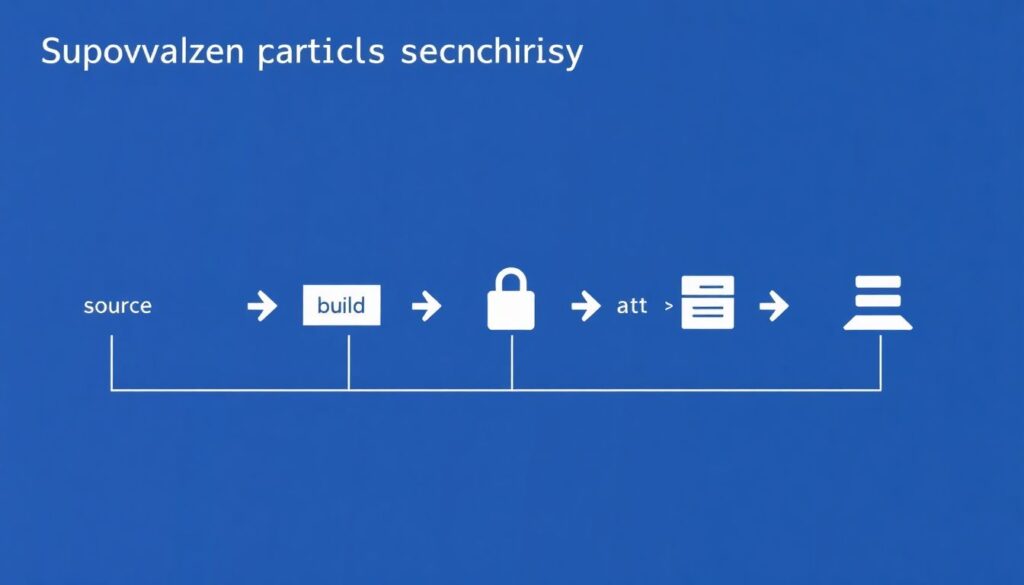
The analytical way to think about artefact security is as a supply‑chain graph: source → build → artefact → registry → deployment. Each edge needs validation. Start by ensuring your CI jobs run in isolated runners with minimal credentials. Then enforce that artefacts are only uploaded by CI, never by developers from laptops. Introduce content‑addressable storage and checksums so you can verify integrity end‑to‑end. Add image signing (Sigstore/cosign, Notary) and make your deployment environments verify signatures before pulling. This combination doesn’t just reduce risk; it forces discipline in the release process and makes debugging deployments radically easier.
Registries of containers: the new perimeter you forgot you had
Your container registry is effectively a critical production system: if someone controls it, they control what runs in your cluster. Segurança em registries de containers Docker e Kubernetes means treating the registry as a high‑sensitivity asset, not just “where images live”. This includes access control, network segmentation, logging, vulnerability management and even lifecycle policies. When you see the registry as part of your security boundary, you start to question who really needs push access, whether public images are mirrored and scanned, and how quickly you can revoke compromised credentials without halting deliveries.
Case: from open registry to controlled gateway
A large e‑commerce company once allowed any engineer to push images to a shared Docker registry used by staging and, indirectly, by production. Nothing terrible happened by malice — but one day, a developer overwrote a “latest” tag with a debug build containing extra logging and disabled auth. That image slipped into a sidecar in production, exposing an internal API. Post‑incident, they redesigned access entirely: CI was the only actor allowed to push to production registries, tags became immutable, and image promotion followed a strict path between environments. The result wasn’t just safer; it also eliminated the recurring “it works locally, not in prod” mysteries.
Picking and combining the right tools for your CI/CD security stack
There’s no single magic product that will “secure your pipeline”. Ferramentas para segurança de pipelines CI CD work best as a layered ecosystem. On one layer you have secret management and identity; on another, artefact integrity and image signing; alongside those, static and dynamic scanners; at the outer layers, policy engines and admission controllers. The analytical approach here is to map risks to controls, instead of stacking tools blindly. For example, if your main concern is secrets leakage, start with a vault and scanning of repos and logs. If supply‑chain tampering is your fear, prioritize signing, SBOMs, and restricted registry access with auditing.
Case: a small team that built a serious security posture with limited budget
One startup with a three‑person platform team decided up front that they wouldn’t compete on number of features shipped, but on security and reliability. They used managed CI runners, cloud‑native secret managers, and a single private registry. Over six months, they systematically rolled out improvements: branch protection, mandatory code review, SAST in pull requests, SBOM generation, and image scanning integrated into deployment. Each step was small, but together they created a robust chain of trust. Interestingly, security never blocked them; instead, it gave them confidence to experiment aggressively because they knew where the guardrails were.
Growing your skills: how to move from ad‑hoc fixes to a security mindset
To truly master segurança em pipelines CI/CD melhores práticas, you need to think beyond “checklist compliance” and move toward systemic understanding: threat modeling, trust boundaries, least privilege, and observable pipelines. A practical way to grow is to treat your own CI/CD as a learning lab. Start by diagramming every step: which identities act, what they can access, and how data flows. Then challenge each assumption: what if this token leaks? what if this runner is compromised? Over time you’ll develop intuition for weak spots, and the recommendations you implement will feel justified, not dogmatic.
Concrete steps for personal and team development
If you want to level up, alternate between theory and practice. Read about real‑world supply‑chain attacks (SolarWinds, Codecov, dependency hijacking) and then ask: “Could our pipeline be abused in a similar way?” Run internal “red team” exercises against your own CI/CD: try to inject secrets into logs, bypass checks, or push unreviewed artefacts. Use the findings not to blame, but to improve. Encourage pairing between DevOps engineers and security specialists, so pipeline design naturally incorporates both perspectives. Over time, you’ll move from reactive patching to proactive design, where security becomes a built‑in property of your delivery system.
Inspiring examples: when secure pipelines unlock faster innovation
A powerful mindset shift happens when teams realize that strong protection de segredos, artefatos e registries doesn’t slow them down — it accelerates them. In one media company, deployment to production used to require manual approval by ops because “we don’t fully trust the pipeline”. After a year of investing in CI/CD security — signed commits, locked‑down runners, enforced reviews, and strict registry policies — ops flipped the switch to full continuous deployment for most services. Incidents decreased, mean time to recover improved, and developers felt safer merging changes because the system would only promote builds that met clearly defined security and quality policies.
From fear‑driven controls to confidence‑driven automation
What separates average teams from standout ones is not the absence of incidents, but the way they interpret them. Teams that use every security scare to tighten their pipelines, refine policies and automate checks gradually replace fear with confidence. Automated tests, scanners and approval workflows become less about bureaucracy and more about shared protection. Over time, this culture attracts engineers who appreciate working in an environment where deployments are fast, reversible, and auditable, rather than chaotic. That cultural flywheel — built on secure CI/CD foundations — is a competitive edge that’s hard to copy quickly.
Resources to keep learning and staying ahead
If you want to go deeper, focus on a few core topics: secret management, software supply‑chain security, container hardening and Kubernetes admission control. From there, explore reference architectures from major cloud providers and CNCF projects that demonstrate como proteger artefatos e imagens de containers no CI CD using real tooling. When you study resources, don’t just copy configs — instead, ask why each control exists and which threat it mitigates. That analytical habit will serve you better than memorizing any specific tool’s UI, because the ecosystem will evolve, but the underlying attack patterns and defensive principles will remain.
Turning knowledge into lasting practice
Reading alone won’t transform your pipelines. Pick one improvement per month and make it non‑negotiable: maybe moving all long‑lived secrets into a managed vault, enabling image signing for critical services, or tightening push permissions to your registries. Document each change, its rationale, and the risks it addresses. Share short internal write‑ups so the whole team learns, not just the person who did the work. Over a year, these incremental changes compound into a radically more secure CI/CD foundation — and you’ll look back realizing that the path to strong segurança em pipelines CI/CD was not a huge project, but a steady series of deliberate steps.