Why cloud data protection is trickier than it looks
When you move critical workloads to the cloud, you don’t just change where your data lives — you fundamentally change how it’s accessed, shared and attacked. Proteção de dados sensíveis na nuvem is less about one magic product and more about putting several well‑designed layers in place: encryption, tokenization, and good data classification at scale.
In practice, the hardest part isn’t enabling a security feature. It’s deciding *what* to protect first, *how* to protect it without breaking apps, and *who* should be allowed to see the real data. That’s where a practical, step‑by‑step approach helps much more than a bunch of buzzwords.
—
Core principles before you touch any settings
Think of your cloud as a rented building: the provider secures the walls, cameras and elevators; you still need to lock your office doors and your filing cabinets.
Shared responsibility and real‑world risk

Cloud providers give strong primitives, but they don’t know what’s sensitive for *your* business. You’re responsible for:
– Deciding what is “sensitive” and why
– Controlling who can see or use that information
– Proving to auditors that controls actually work
Expert tip (CISO of a fintech, anonymized):
> “Every breach post‑mortem I’ve seen in the cloud had the same root cause: someone assumed the provider was doing data protection for them. They’re not — they’re giving you building blocks.”
—
H2: Necessary tools for serious cloud data protection
Before designing workflows, you’ll want a concrete toolset. You don’t need everything on day one, but you do need to know what each category does.
H3: Native cloud security and key management tools
Start by mastering what your cloud platform already gives you. These are your baseline ferramentas de segurança para dados confidenciais na nuvem:
– Key management / HSMs (KMS, Cloud KMS, Key Vault, etc.)
– Native disk and storage encryption (EBS / disk encryption, S3 / Blob encryption, database TDE)
– IAM / roles and policies, including fine‑grained permissions
– Secret managers (for passwords, API keys, connection strings)
Short version: if you aren’t using the provider’s managed keys, audited access controls and secret stores, you’re running with the parking brake off.
H3: Encryption, tokenization and classification platforms
To go beyond “checkbox security”, you’ll likely add:
– Data classification tools that scan object storage, databases and logs for PII, PCI, PHI and trade secrets
– Tokenization platforms that substitute raw values with reversible tokens
– Format‑preserving encryption libraries or services
– CASB and data loss prevention (DLP) services that monitor use of sensitive data across SaaS and IaaS
– A serviço de compliance e proteção de dados na nuvem (managed service or consultancy) to align tech with regulations like GDPR, LGPD, HIPAA, PCI DSS
Expert recommendation (cloud security architect):
> “Aim for one central place where you define classification rules and policies, then propagate them into your encryption, DLP and monitoring tools. Don’t hard‑code rules into every app.”
—
H2: Step‑by‑step process: from chaos to controlled data
Instead of starting with tools, start with a map. Then decide how deep your protections should go.
H3: Step 1 — Inventory and classify data at scale
You can’t do proteção de dados sensíveis na nuvem without knowing what you have and where it lives.
1. Map your data stores
Include object storage buckets, databases, data warehouses, backups, logs, analytics platforms and SaaS exports.
2. Adopt a simple but strict classification scheme
For example: Public, Internal, Confidential, Highly Confidential. Add regulatory tags like “GDPR” or “PCI”.
3. Deploy soluções de classificação de dados sensíveis em escala
Use automated scanners to:
– Detect patterns (credit cards, IDs, emails, health codes)
– Apply labels or tags directly on buckets, tables and files
– Generate reports that show where high‑risk data is concentrated
4. Involve the business, not just IT
Ask data owners to validate classifications. Finance, HR and Product know the business impact of leaks much better than infra teams.
Keep the first pass quick and rough. You can refine categories later; you can’t protect data you haven’t even discovered.
H3: Step 2 — Design an encryption strategy that won’t break apps
Criptografia e tokenização de dados em nuvem should be planned with your application patterns in mind.
Longer, more detailed view:
– Encrypt everything at rest by default
Switch on storage and database encryption using managed keys, at minimum. Use customer‑managed keys (CMKs) for highly sensitive workloads or strict compliance.
– Centralize key management
– Use a single KMS account or subscription per environment (prod / non‑prod)
– Separate key admins from data admins
– Enable key rotation and log every key use
– Plan encryption in transit
Enforce TLS from clients to load balancers, between microservices, and into databases. No plain‑text internal traffic, even inside “trusted” VPCs or VNets.
– Avoid homegrown crypto
Use audited libraries and provider‑supported encryption modes. Don’t invent your own algorithms or key formats.
Expert recommendation (crypto engineer):
> “Your biggest win is not a fancy algorithm; it’s minimizing who can ever touch the decryption keys. If your app layer can’t read plain data, attackers usually can’t either.”
H3: Step 3 — Introduce tokenization where plain text is truly risky
Encryption protects data “at rest” and “in transit”. Tokenization changes how that data behaves inside applications.
Short, practical guidelines:
– Use tokenization when:
– Many systems need *identifiers* but only a few should see the *values*
– You must reduce PCI scope by replacing card numbers with tokens
– You need realistic‑looking values for testing, analytics or logs
– Choose between reversible and irreversible tokenization:
– Reversible (with a secure vault) if you must occasionally retrieve the original value
– Irreversible (similar to hashing with salt) for cases where you never need to see the original again
– Keep tokenization in a dedicated, hardened service:
– Strict access control and network isolation
– Full audit logging
– Integration with KMS or HSM for key handling
This is where the line between criptografia e tokenização de dados em nuvem really matters: encryption is perfect for storage and backups; tokenization is often better for transactional systems and multi‑team environments.
H3: Step 4 — Connect classification to controls
Once you know what is sensitive, use that knowledge to drive automation.
– Attach IAM policies to labels: Highly Confidential → stronger MFA, limited roles, strict logging
– Configure DLP rules so that classified data can’t be emailed out or synced to unmanaged devices
– Integrate labels into CI/CD: if a resource marked “Highly Confidential” is about to be created without encryption, the pipeline fails
This is where soluções de classificação de dados sensíveis em escala pay off: they become a “policy engine” instead of just a fancy scanner.
H3: Step 5 — Governance, monitoring and continuous improvement
Your controls are only as good as your visibility.
Longer but crucial steps:
– Aggregate logs from:
– KMS and key usage
– Data access (database audit logs, storage access logs)
– IAM changes and privilege escalations
– Feed them into a SIEM or security data lake
– Build simple, high‑signal alerts first:
– Mass downloads of sensitive data
– New keys created outside standard workflows
– Access to PII from unusual locations or service accounts
Many teams use a serviço de compliance e proteção de dados na nuvem or an MDR/SOC partner to help interpret these signals and maintain compliance reports.
—
H2: Practical expert recommendations for real‑world teams
H3: Make security usable for developers
Developers are your first line of defense. If security is painful, they will route around it.
Experts typically recommend:
– Provide ready‑to‑use libraries or SDKs for encryption and tokenization
– Offer “golden templates” for databases, buckets and queues — encryption and logging preconfigured
– Add security checks to CI/CD pipelines, not just manual reviews
Security lead quote:
> “We stopped writing documents and started shipping Terraform modules. Adoption went from 30% to 95% because devs could just plug them in.”
H3: Start with high‑value, high‑risk data
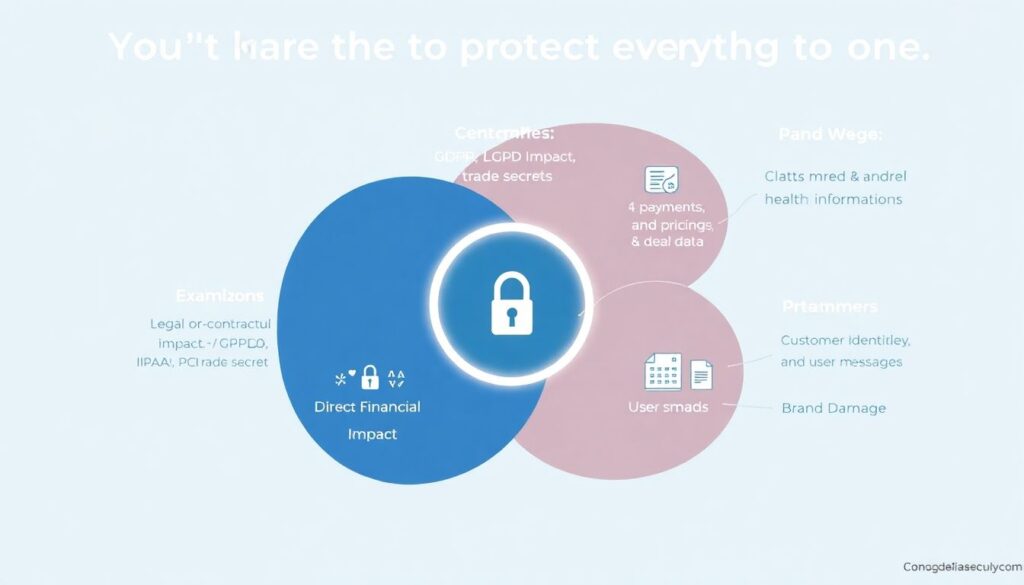
You don’t have to protect everything at once.
Focus your initial effort where three things intersect:
– Legal or contractual impact (GDPR, LGPD, HIPAA, PCI, trade secrets)
– Direct financial impact (payments, pricing, deal data)
– Brand damage (customer identities, health information, user messages)
Secure those zones deeply with encryption, tokenization, and tight access. Then extend the same patterns to less critical datasets.
—
H2: Troubleshooting and common pitfalls
Even good designs hit bumps in production. Here’s how to handle them without dismantling your entire model.
H3: Performance and latency issues
Encryption and tokenization add work. If they’re implemented in the hot path of your application, users may feel it.
Typical symptoms:
– Longer response times for read/write operations
– Timeouts during peak load
– Higher CPU usage on app or tokenization services
How to fix:
– Cache decrypted results where acceptable, with strict TTLs
– Batch operations instead of per‑row or per‑field calls
– Offload operations to asynchronous workflows where business flows allow
– Profile carefully; optimize the 10% of requests causing 90% of overhead
Expert tip:
> “Measure before optimizing. We’ve seen teams blaming encryption for latency when the real issue was inefficient queries or oversized ORM models.”
H3: Broken analytics and search
Analysts often complain that once you encrypt or tokenize, data science becomes harder.
Short, targeted remedies:
– Use partial or format‑preserving techniques when you need pattern matching or prefix search
– Maintain separate, heavily restricted analytics environments with access to re‑identified data when legally permitted
– For many analytics tasks, tokenized IDs are enough — models often care about relationships, not the original values
If your data science teams are blocked, invite them into the design discussions rather than bolting security on after the fact.
H3: Key and token vault misconfigurations
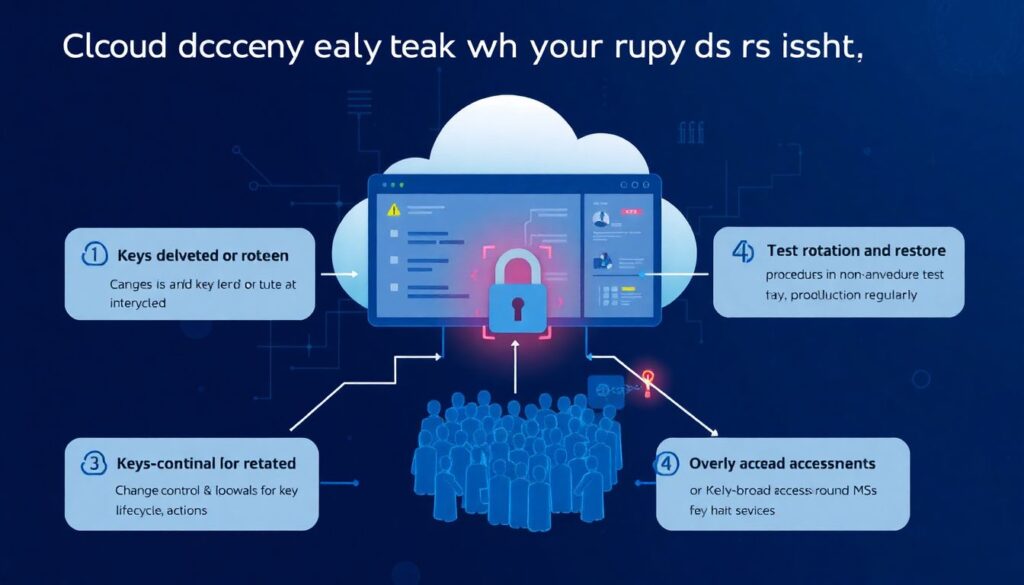
Misconfigured key or token services can cause outages or scary security gaps.
Common issues and fixes:
– Keys deleted or rotated incorrectly
– Implement change‑control and approvals for key lifecycle actions
– Test rotation and restore procedures in non‑prod regularly
– Overly broad access to KMS or tokenization APIs
– Use least privilege: specific roles for encryption vs. decryption
– Deny‑by‑default at network and IAM layers
– No visibility into who uses which keys
– Enable detailed logging and integrate with your SIEM
– Review high‑sensitivity key usage at least monthly
—
H2: Putting it all together: a realistic rollout roadmap
To wrap the instructions into something actionable, here’s a condensed, expert‑style rollout:
– Month 1–2: Discovery and design
– Run automated discovery and classification
– Agree on labels and data ownership
– Draft your encryption and tokenization patterns
– Month 3–4: Pilot and hardening
– Pilots in one or two systems containing sensitive data
– Integrate with KMS, secret management and logging
– Fix performance and developer‑experience issues early
– Month 5–8: Scale and automate
– Roll out to other high‑risk systems
– Attach policies to classification labels
– Embed checks into CI/CD for new resources
– Ongoing: Monitor, review and adapt
– Periodic classification rescans
– Regular access reviews and key audits
– Lessons‑learned sessions after incidents and near‑misses
Handled this way, proteção de dados sensíveis na nuvem stops being a one‑off project and becomes part of how you design and run every new service. Over time, encryption, tokenization and classification in the cloud fade into the background — not because they’re less important, but because they’ve become part of the default way you build.